Network Devices and its Various Types
A computer network comprises a collection of interconnected devices. These devices, including computers, printers, and other data-transmitting tools, are linked through communication channels. Various types of network devices are utilized to establish, maintain, protect, and improve network connections. Network Devices carry out different functions at different layers of the OSI model and have different features. In this blog post, we will discuss Network Devices in Computer Networks, their purpose, and their different types. Before getting into the different types of Network Devices in Computer Networks, let’s first understand what network devices are. Network devices are hardware components that facilitate connection establishment and control network traffic between devices within a computer network. Apart from that, these devices manage their operations. They can function at different layers of the OSI model, like the data link layer, physical layer, network layer, or application layer. Some may even operate across multiple layers, while others are designed for only one layer. Network devices can be broadly classified into two categories: Let’s discuss the purpose of Network devices in detail. The primary objective of network devices is to facilitate communication and collaboration between nodes within a network. They also play a role in enhancing network performance, security, and reliability. Some specific functions performed by network devices include: Now we have a better understanding of computer network devices, let’s move on to the different types of networking devices. Many network devices can be used in computer networking. Some of these have been explained below: Switches serve as networking devices that function at the data link layer (layer 2) of the OSI model. The main purpose of switches is to connect end devices within a network and allow the forwarding of data packets utilizing their MAC addresses. By creating collision domains for each port, switches effectively mitigate collisions and congestion on the network. Additionally, switches are capable of configuring VLANs (Virtual LANs) to establish logical groups of devices on a network. Bridges are also a type of networking device that operates at the data link layer (layer 2) of the OSI model. Their primary role is to connect segments within a network and enable the forwarding of data packets based on their corresponding MAC addresses. Similar to switches, bridges create collision domains for each segment effectively. This will help in minimizing collisions and congestion on the network. Furthermore, bridges are equipped with filtering capabilities to discard unwanted packets or forwarding to pass desired packets. Routers are also networking devices that operate at the network layer (layer 3) of the OSI model. The main function of the router is to connect networks and allow the forwarding of data packets based on their respective IP addresses. By creating broadcast domains for each interface, routers effectively reduce broadcast traffic on the network. Apart from that, routers use different routing protocols such as RIP (Routing Information Protocol), OSPF (Open Shortest Path First), or BGP (Border Gateway Protocol) to determine paths for transmission through routing processes. There are many types of Routers in computer networking. Some of the common routers are: Repeaters are sometimes also known as “Signal Booster”. The main function of the repeater is to regenerate an incoming signal from the sender before retransmitting it to the receiver. The layer at which it operates is the physical layer of the OSI model. This layer is mainly responsible for the actual transmission and reception of the data over the physical medium such as cables or fiber optics. A repeater can extend the range of the network by boosting the signal and reducing the error and loss of data. Apart from that, repeaters are also responsible for converting the data between different network signals, such as optical, wireless, or electrical signals. Gateways are intermediary devices that usually operate at the network layer (Layer 3) of the OSI model and are responsible for connecting networks that are using different protocols or architectures. They do so by translating or converting data formats or protocols between different networks. A gateway is one of the important networking devices as it acts as a crucial component of any network architecture that involves multiple networks. Apart from this, Gateways can carry out various other functions such as filtering, security, routing, and encryption. Hubs are intermediary devices that usually operate at the physical layer (Layer I) of the OSI model that connect multiple devices on a local network. Hubs function by broadcasting data to all the devices that are connected to it, regardless of their destination. Hubs can help in simplifying the wiring and installation of a LAN by providing a central point of connection. Hubs are capable of creating a single collision domain and a single broadcast domain. Apart from its functions that are mentioned above, it does have some limitations, such as low security, low performance, and high collision rate. Modems are the network devices that usually operate at the physical layer (Layer I) of the OSI model. These devices can modulate or demodulate analog signals into digital signals or vice versa. Apart from that, with the help of modems, digital devices can communicate with one another over analog transmission media such as telephone lines or cable lines. Modems can easily connect a LAN to a WAN or the Internet. There are different types of modems. Some of these are: Access points are network devices that usually operate at the data link layer (Layer II) of the OSI model and are mainly used to bridge the wired and wireless network. In simple terms, it is a device that allows wireless-capable devices to connect to a wired network. Here, the data can be transmitted and received using radio waves or infrared signals. Apart from this, an access point can also be utilized to extend the range and strength of wireless signals. Most of the time, it is used in large offices or public places that need to provide wireless access to many users or devices. Further, it can support different wireless standards and protocols, such as Wi-Fi, Bluetooth, or IoT. Access Points are classified into 3 categories. These are: NIC stands for Network Interface Card and operates at the data link layer (Layer II) of the OSI model. It is a hardware component that is responsible for enabling a device to connect to a network. A NIC also has one or more ports that allow different types of cables or wireless signals to connect to the network. NIC further provides a physical interface for data transmission and reception purposes. Apart from that, it also has a unique MAC address that identifies the device in a network. Some of the major tasks performed by NIC are data transfer, network traffic engineering, and interrupt support. A firewall is an intermediary device that operates at various layers of the OSI Model depending on its type. It can be either hardware or software, and its main purpose is to protect the network from any unauthorized access or malicious attacks by enforcing policies or rules. Now, the question that arises is how these attacks can be stopped. All malicious activities can be controlled via a firewall as it can block or allow packets based on their source, destination address, port number, or protocol type. Some of the security functions carried out by firewalls are: There are various types of firewalls. Some of these are: These are the various networking devices mainly used in Computer Networks. Network devices are hardware components that connect computers and other devices in a network. Examples are routers, switches, hubs, modems, firewalls, NICs, and many others. There are various types of devices used in networks; some of the most common are hubs, switches, routers, bridges, gateways, and many others. All these devices perform certain functions as per the requirement of the network or the system. The 8 types of networks are: A computer network is nothing but a system of interconnected devices that can communicate and share data. Some of the devices that are used are routers, switches, hubs, and firewalls. These devices perform different functions in order to enable network connectivity and security. Network devices are essential components of computer networks that are mainly used to enable communication as well as data transfer between different devices in a network. Different computer network devices are utilized, and they perform different functions at different layers of the network model. In this blog, we have explained what are network devices, and their purpose, and discussed different types of network devices in computer networks.Introduction
What are Network Devices?
Purpose of Network Devices
Types of Network Devices
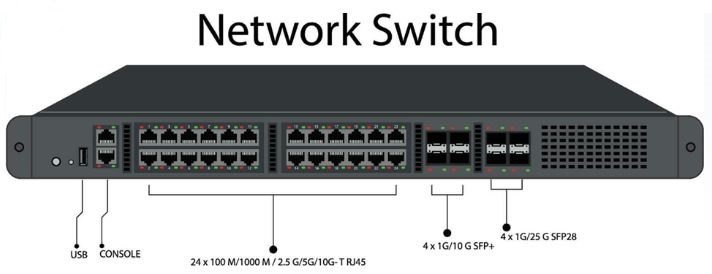
Switch
Bridge

Router

Repeater

Gateway

Hubs

Modem

Access Points

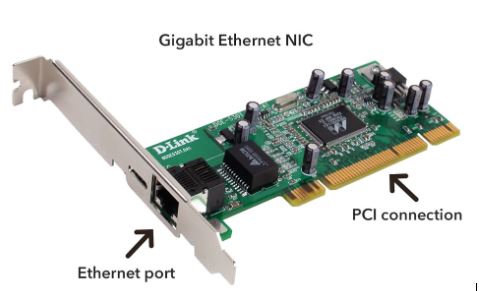
NIC
Firewall

Frequently Asked Questions
Q1. What is network devices and examples?
Q2. What type of devices are used in networks?
Q3. What are the 8 types of network?
Q4. What is computer network and its devices?
Conclusion







