Network Protocols
Network Protocols are the set of rules for communication between network devices, including the ways devices can identify and make connections with each other. In other words, we can say protocols help to make communication. Without protocols, devices would be unable to comprehend the electronic signals they transmit via network connections to one another. In this article, we will be discussing various network protocols and their importance. So, let’s get started with the network protocols. You get to learn about network protocols in CCNA Online Training. An established set of guidelines that determines how data is transferred between various devices connected to the same network is known as a network protocol. Moreover, it enables interconnected devices to communicate with one another despite any variations in their internal workings, organizational structures, or design. Network protocols are vital for modern digital communications because they make it possible to communicate with people anywhere on the globe. Network protocols allow devices to communicate with each other because of predetermined rules built into device software and hardware, similar to how speaking the same language makes communication between two individuals easier. Without the use of network protocols, local area networks (LAN) and wide area networks (WAN) could not operate as they do today. Network protocols divide massive operations into more manageable, specialized jobs or activities. This happens at every level of the network, and in order to finish the bigger goal at hand, each function must work together at every level. A group of smaller network protocols that cooperate with one another is referred to as a protocol suite. Network protocols are often developed in accordance with industry standards by various networking or information technology organizations. Here are the following groups have defined and published different network protocols: Although network protocol models typically operate in similar ways, each protocol is distinct and functions in the manner described by the company that developed it. The protocols can be classified in three different categories which are – We will discuss 15 network protocols in this article. You can also check our blogs for detailed information on these and other important networking protocols. IP, defined in RFC 791, is a protocol used to transfer data from one device to another. Internet Protocol is connectionless, which means it doesn’t guarantee data delivery. Still, to ensure the delivery of data, a protocol is needed, which we all know is Transmission Control Protocol (TCP). TCP is defined in RFC 793 as we all know about Transmission Control Protocol; it is a connection-oriented and reliable end-to-end protocol designed to fit into a layered hierarchy of protocols that support multi-network applications. As it’s a connection-oriented protocol it’ll always guarantee the ordering and sequencing of messages because it uses the 3-way handshake process, which is like – TCP Header – User Datagram Protocol (UDP) is a protocol that is used for internet communication. It is chosen for time-sensitive applications like gaming, playing videos, or if you have some audio-video communication over the internet, like video calls, video conferencing, etc. Some examples of UDP Protocol are – Voice over IP (VoIP), online games, and social media streaming like Instagram live, Facebook live and Twitter spaces and many more. UDP Header – Read more about TCP and UDP protocol differences here – TCP vs UDP FTP is defined in RFC 959. As the name represents file transfer protocol used for downloading and uploading files from a remote host running an FTP server. It allows us to create directories, delete files, transfer files, etc. FTP is an application layer protocol which uses port number 21. FTP clients that are available for free download include FileZilla Client, FTP Voyager, WinSCP, CoffeeCup Free FTP, and Core FTP. Many of us have used File Transfer Protocol without even realizing it. If you have ever downloaded a file from a web page, you’ve used FTP because that’s what the responsibility of FTP is. TFTP is defined in RFC 1350. Because TFTP is a simple file transfer protocol, it was termed as the Trivial File Transfer Protocol. The TFTP protocol is based on the similarly simplified transport protocol UDP (User Datagram Protocol), which allows data to be sent between communication partners without requiring them to share a fixed connection. It’s a variation on FTP, and it doesn’t have a security level compared to FTP. After all these protocols like FTP and TFTP were introduced, the users faced a major challenge; FTP was not secure. Even though some authentication methods were associated with FTP still, it was not as secure as we wanted it to be. FTP simply transmits the data between sender and receiver without any encryption, so any hacker in the middle of the network can capture the network. The solution for this challenge is the SFTP protocol which is based on (SSH) Secure Shell, which provides strong encryption between the users who are exchanging the data. SFTP is also a client-server protocol that can be accessed using GUI or CLI. Learn about the difference between encryption and Hashing SMTP is defined in RFC 821. It is used to send and receive emails. Sometimes it can be used with IMAP/POP3. The main work of the Simple Mail Transfer Protocol is to send and forward the messages to the server for forwarding, whereas it is allowed to send and receive both simultaneously. Note – There is also a new version of SMTP, which is (ESMTP) Extended SMTP. Model of SMTP – HTTP is defined in RFC 2068, and it’s an application layer protocol which allows text, graphics and other content to be downloaded from the server. This protocol is majorly used in surfing the web. It also defines what kind of actions can be requested by clients & how the server will initiate the requests the client sends on these particular servers. HTTP uses a URL to determine what page should be downloaded from the server where you are requesting the data. HTTP was designed in the early 1990s and has evolved over time. HTTPs is an encryption protocol to encrypt communications that is also known as (TLS) transport layer security. Formerly it was known as (SSL) secure socket layer. Some websites like Flipkart and Banking Websites use HTTPs. Now all the browsers are supported by HTTPs. Telnet is defined in RFC 854. This protocol is used to enable users to manage a device remotely. Telnet can be configured on devices like routers and switches. For example, a user sitting in the LAN network wants access to the switch, so using some IP address will easily take access to the switch without going to the physical location where your switch is located in the enterprise network. Telnet is not secure because whatever the data is being transferred always travels in clear text without any encryption. Telnet is also a client-server protocol. Secure Shell is the full form of SSH. It’s the enhanced version of Telnet because, in production networks, we mostly use this protocol to get secure access for users and the access of devices. The best part about SSH is that the data we are transmitting is always encrypted, so we really don’t need to worry about security. SSH has 3 layers – ARP is defined in RFC 826. It is one of the most common protocols in the entire networking. As we all know, ARP finds the MAC address of connected clients with the help of source and destination IP addresses by using some broadcast MAC address. Read more: ARP and the working of ARP ICMP is defined in RFC 792; this protocol works with Layer 3 of the OSI model. The major function of ICMP is to detect and report errors. It can also be used for network diagnostic like (PING, TRACERT) ICMP Messages Types – Type 0 – Echo Reply NTP, defined in RFC 958, is a part of TCP/IP Protocol that synchronises time between the devices. The term applies to both the protocol and the client-server model, which also runs on specific machines. Network Time Protocol (NTP) simply provides a reliable connection between time sources over the devices because synchronization with time is mandatory in today’s production networks. DNS is defined in RFC 1034, and we can say it is the naming database of the internet. As humans, we can’t remember all the numbers, so we always save our friends’ and family contact numbers with their names so we can identify them. DNS works in the same way; it is the naming database of the internet which converts the name into IP and IP into the name, so as humans, we can browse any website by writing the name of the website instead of IP. There are 4 DNS servers indulged in loading a webpage, and these are as follows – Note – If you want to see DNS details on your windows machine, you can use the “nslookup” command on the command prompt with the particular server like – Nslookup www.google.com As a result, we’ll get the IP of this particular domain we have entered. You can also Check out – Difference between EIGRP and OSPF DHCP is an application layer protocol which helps us to assign the IP addresses on the client machine automatically. For example, if we have 100 users in our production network, assigning IP to all the users is quite a pathetic task for the network admin. With the help of DHCP, we can automatically assign IPs to all 100 users. As DHCP is also a client-server model which performs DORA Process. In this DORA process – Discovery – is done by the client Offer – is done by the server Request – is done by the client Acknowledge – is done by the server DHCP Server uses port no. 67 DHCP Client uses port no. 68 These are the network protocols that every network engineer must be familiar with. Network protocols are a set of rules that govern how data is transmitted and received across a computer network. They define the format, sequencing, and error handling of data, ensuring efficient and reliable communication between devices. Common examples include TCP/IP, HTTP, and FTP. The three commonly used protocols in networking are TCP/IP, which facilitates reliable data transmission; HTTP, used for web communication; and DNS, responsible for translating domain names into IP addresses for internet access. TCP (Transmission Control Protocol) is a core networking protocol that enables reliable and ordered communication between devices over IP networks. It breaks data into packets, assigns sequence numbers, and handles error recovery and flow control, ensuring secure and accurate data transmission. The Internet Protocol (IP) has three commonly used classes: Class A, Class B, and Class C. Class D is used for multicast IP addresses, while Class E is reserved for experimental or future use. In this blog, we have discussed everything about network protocols including what are these, how these works, and what are various types of network protocols. We have also discovered various network protocols. In conclusion, network protocols form the backbone of modern communication and connectivity. These protocols, categorized into communication, management, and security, enable seamless data transmission, efficient network management, and robust security measures. If you wish to learn more about these protocols, you should consider joining PyNet Labs’ CCNA or CCNP ENCOR training to get a detailed explanation and how to use these protocols. Remember that having a training partner will help you achieve your career goals and be the best version of yourself. Hope you liked this article; please write to us with any suggestions or complaints in the comment box below. We really like to hear from our readers. If you are still with us, here’s a treat for you. Some more Protocols that might interest you: Introduction
What are Network Protocols?
How Network Protocols Works?
Various Types of Network Protocols
Network Protocols List
Internet Protocol
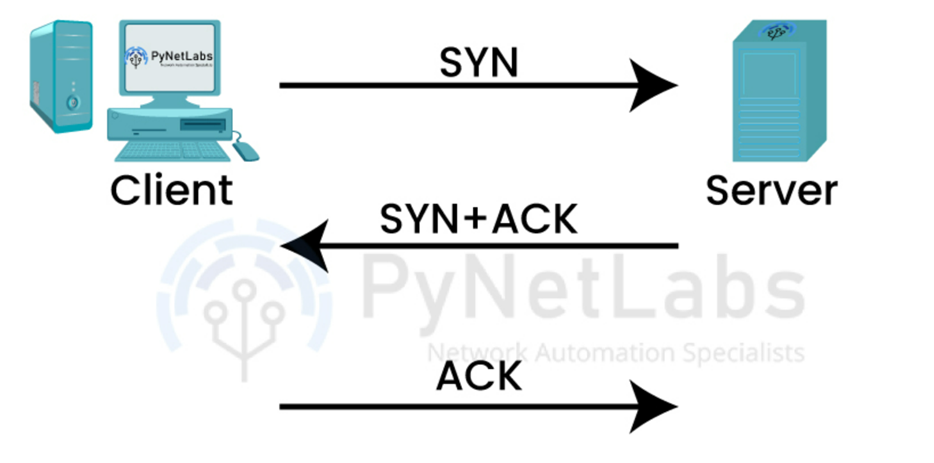
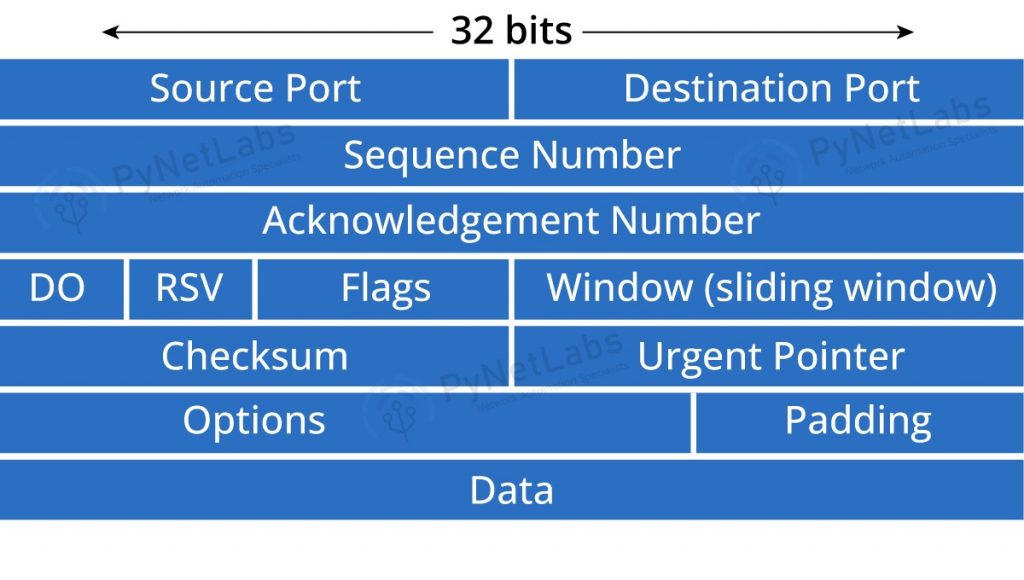
Transmission Control Protocol (TCP)
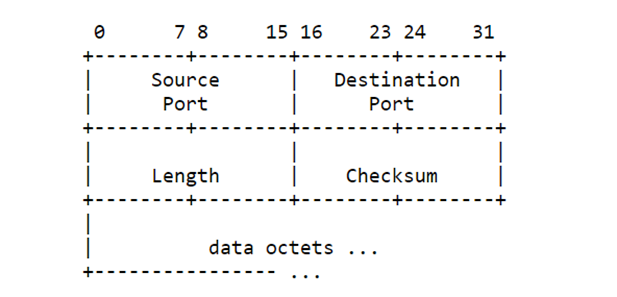
User Datagram Protocol (UDP)
File Transfer Protocol
Trivial File Transfer Protocol (TFTP)
Secure File Transfer Protocol (SFTP)
Simple Mail Transfer Protocol (SMTP)
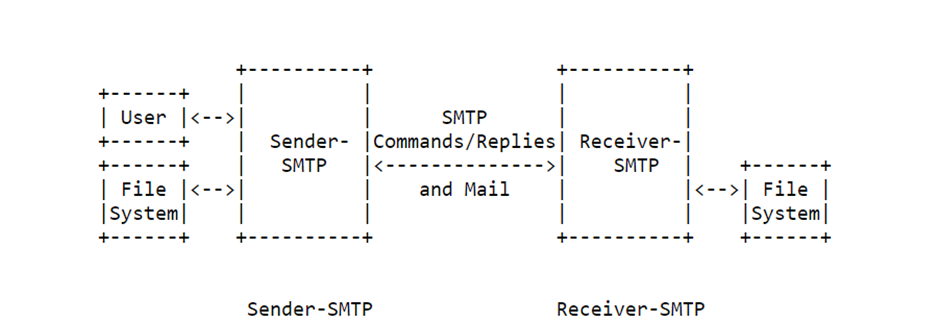
Hypertext Transfer Protocol (HTTP)
Hypertext Transfer Protocol Secure (HTTPs)
Telnet
Secure Shell (SSH)
Address Resolution Protocol
Internet Control Message Protocol (ICMP)
Type 1 – Unassigned
Type 2 – Unassigned
Type 3 – Destination Unreachable
Type 4 – Source Quench
Type 5 – Redirect
Type 6 – Alternate Host Address
Type 7 – Unassigned
Type 8 – Echo
Click on the link from IANA’s official documentation to check out the multiple types of messages.Network Time Protocol (NTP)
Domain Name System (DNS)
Dynamic Host Configuration Protocol (DHCP)
Frequently Asked Questions
Q1 – What are network protocols?
Q2 – What are the 3 protocols used in networking?
Q3 – What is TCP in networking?
Q4 – What are the 5 classes of Internet Protocol?
Conclusion
VTP – VLAN Trunking Protocol
VRF – Virtual Routing and Forwarding







