What is the difference between Encryption and Hashing?
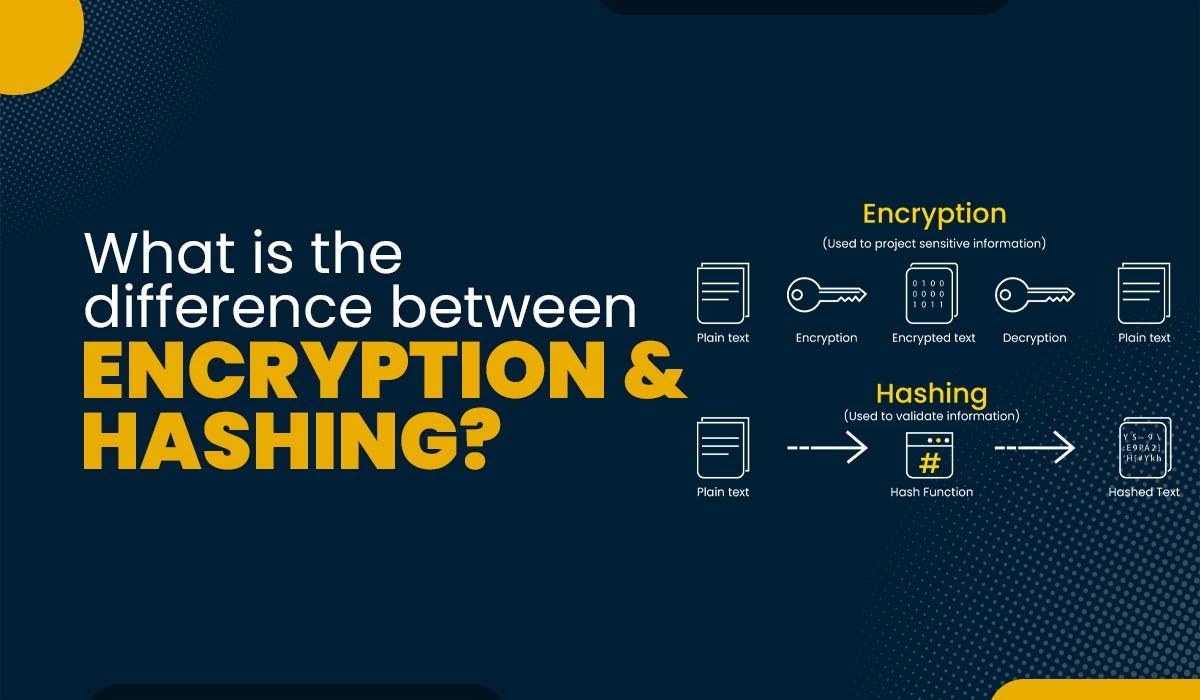
When it comes to data security, hashing and encryption are the two most crucial foundational operations. Both of these techniques transform the raw data into an entirely different format. The terms Hashing and Encryption are often used in the domain of data security, but do you know what is the difference between encryption and hashing? Some individuals mistakenly use the two terms as equivalents, but hashing and encryption are two separate (though related) techniques. These two are part of our CCNA Course. Encryption is a bidirectional process; plaintext is the input, and cypher text is the output. Due to the bidirectional nature of Encryption, the data may be decrypted and made legible once again. In contrast, hashing is a one-way process, and the plaintext is converted into a one-of-a-kind digest using salt, and the original is subsequently irreversible in the hashing process. While it is theoretically possible to reverse a hash, the amount of computing power required to do so renders the process impractical. These are the common difference between encryption and hashing. Moving on, let’s take a deep dive and understand what encryption is. Encryption is a two-way function where data is passed in as plaintext and comes out as cipher text. Encryption is a process where the normal text data which normally we as humans can read is converted into data that is unreadable by humans and technology, and we call it to cipher text. It is designed to protect sensitive data, whether the data is over the internet or the data is inside an offline device. The process of Encryption typically involves the following steps: Encryption is used to protect data from being accessed or modified by unauthorized parties and is a critical component of computer and network security. Encryption involves temporary confusion of essential details, and the recipient receives unreadable data, but transcription contains a key that eliminates the confusion. When put together, the meaning of the messages becomes clear. There are 40% of organizations that adopt an enterprise-wide encryption strategy in operations, and this number grows yearly. This practice is essential in business sectors that deal almost exclusively with private data, such as: Password encryption is highly universal and one of the reasons encryptions are so widely accepted is that we’ve been using these technologies for hundreds of thousands of years. It means that scribes preserved essential information with hieroglyphs, and only those who knew the translation code could check what was said in each phrase. Encryption is straightforward; data is transferred from one party to another in unreadable form and translated upon arrival. End users do not need to verify the encryption key; the data must travel back and forth. So, the user’s device shares a query with another party, and in reply, that party shares back a duplicate of the security authentication that includes a decode key. Here are the different types of encryptions that are used – This type of Encryption uses a key for the Encryption and decryption of data, and the key is the same in both ways either encrypt or it’s decrypt. Also, this key which we generate should be shared on both sides, either source or destination and if the Encryption is between multiple users so users must have the same key which is generated for Encryption. This symmetric Encryption is majorly used because, with this kind of Encryption, a large amount of data is encrypted in a small amount of time using the secret key which is being generated. In this category of Symmetric Encryption, two more types of sub-categories are there – Some examples of symmetric algorithms are – RC4 (Rivest Cipher 4) RC5 (Rivest Cipher 5) RC6 (Rivest Cipher 6) AES (Advanced Encryption Standard) -Mostly used now! DES (Data Encryption Standard) In this kind of Encryption, there are two keys used for the encryption process one is the private key, and the second is your public key. It’s more secure as compared to symmetric Encryption because here, the private key is used by users or the nodes who generate the key pair, whereas the public key is used by the user who wishes to send the encrypted data to the user who has the private key. Many protocols rely on asymmetric Encryption, which includes the TLS & SSL protocols. These keys are very long in length with large number mathematical numbers and paired together to make the Encryption more reliable, so the hackers can’t decrypt the data. Examples of asymmetric keys – Rivest Shamir Adleman (RSA) Digital Signature Standard (DSS) Digital Signature Algorithm (DSA) Elliptical Curve Cryptography (ECC) There are some of the widely applied encryption algorithms: Now that we have seen what is encryption, it is time to move on to understand what is hashing. Hashing is a process that takes plain data as input and provides the output by doing some mathematical functions. We often call this mathematical function hash value, message digest (MD), or thumbprint as message digest we also see in the routing protocol authentications where plain text and MD5 are there. The input can be of any size and the hash is typically much smaller, often a fixed number of characters. Hashing is used for a variety of purposes, including verifying the integrity of data, generating unique identifiers, and creating a non-reversible representation of a password. In the context of computer security, hashing is often used to store passwords in a secure manner, as it is not possible to determine the original password from the hash. It is computationally infeasible to retrieve the original input from the hash since hashing algorithms are intended to have one-way functions. There is a wide variety of hashing algorithms to choose from, and they all have their advantages. A secure hash algorithm creates a hash value called a hash function. Hashing algorithms produce different values for different keys. That is why an individual input string must have a unique hash value. But through this, some cases of identical hash values are used by keys, known as hash collisions. An interpretable characteristic of any hashing algorithm is how collisions change its hash function. Collisions are a hash-function vulnerability that bad actors can potentially abuse, so a good hashing algorithm must be complex enough to prevent collisions. Some common hashing algorithms include Here are the main difference between Encryption and Hashing in tabular form – We hope after these explanations, you have a better clarity of the difference between encryption and hashing. Encryption transforms plaintext into ciphertext using an algorithm and key for confidentiality. Whereas, Hashing creates a fixed-size hash value for data integrity, but it is irreversible and Encoding converts data into a specific format, but it does not provide security. Encryption and hashing are both cryptographic techniques that use algorithms, but they differ in their reversibility and purposes; encryption is reversible, used for confidentiality, and requires a key, while hashing is irreversible, used for data integrity verification, and doesn’t require a key. Encryption is a specific technique within the broader field of cryptography. Cryptography encompasses a range of techniques and methods used to secure communication and data. Encryption specifically refers to the process of converting plaintext into ciphertext using an algorithm and key. To summarize, cryptography is the larger field that deals with securing information, while encryption is a specific method employed within that field. Encryption and hashing offer different security guarantees. Encryption is primarily used for confidentiality and is reversible, while hashing is used for data integrity verification and is irreversible. While encryption is generally considered more secure in terms of protecting data confidentiality, both techniques are important in different aspects of information security. Data security relies on the use of encryption and hashing. Both encryption and hashing have advantages and disadvantages and are commonly used in combination to provide further protection for sensitive data. Encryption and hashing operations adhere to the two components of the triangle in information security, which are confidentiality and integrity. This blog provides a brief overview of what is the difference between encryption and hashing. It also draws attention to the subtle differences between them and shines a light on the ways in which their unique features open varied doors for their area of application or usage. Check out our Courses at – PyNet Labs CoursesIntroduction
Encryption vs Hashing – A quick overview
What is Encryption?
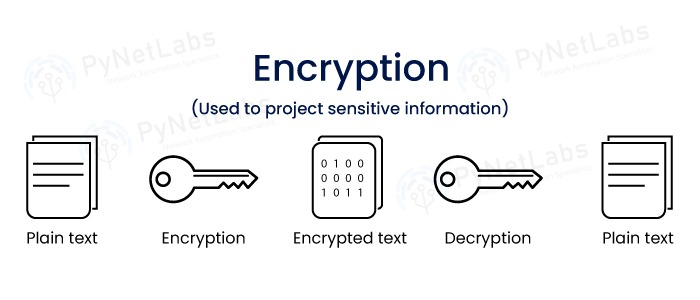
How Encryption works?
Types of Encryption
Symmetric Encryption
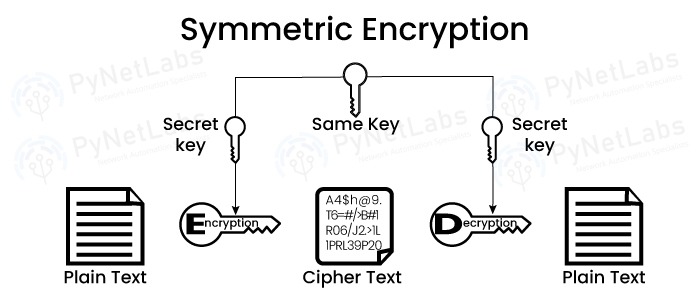
Asymmetric Encryption
Encryption Algorithms
What is Hashing?
How Hashing Works?
Hashing Algorithms
Difference between Encryption and Hashing
Basis Hashing Encryption Meaning It is a 2-way process that takes plain text and converts it into a cipher text. It is reversible, meaning encrypted data can be converted back to plain text. It is a one-way process where plain text is converted to digest using a salt. It is considered to be non-reversible. String Length The length of the converted string will not change. There is no certainty that the length of the original data and the length of the encrypted characters will be the same. Function It cannot be reversed. It only works in one way. It can be reversed only by the use of a decryption key. It’s a two-way process. Usage It is used in several digital applications, including digital signatures, file transfers, passwords, and more. Digital certificates, electronic mail, and other forms of digital communication all employ encryption. Keys Since hashing is a one-way function, there is no need to use a key to decode the message. Encryption is keyed. In the case of symmetric encryption, a public key is generated and given to the recipient so that they may decode the message. With asymmetric encryption, the recipient is given their own private key. Algorithms MD4, SHA, MD5, etc. AES, ECC, RSA, etc. Purpose The goal of hashing is to protect the integrity of data. The goal of encryption is to keep the confidentiality of data. Types Identity Hashing, Digit Folding, and Division Hashing Symmetric and Asymmetric encryption Frequently Asked Questions
Q1 – What is the difference between encryption and hashing and encoding?
Q2 – What are the similarities and differences between encryption and hashing?
Q3 – What is the difference between encryption and cryptography?
Q4 – Which is more secure hashing or encryption?
Conclusion







