Objectives of Network Security

Nowadays, almost every business has shifted online to offer their services. Companies now have more valuable information than ever before, and securing that information is critical to their success. Effective network security functions as a gatekeeper, prohibiting unwanted access, abuse, modification, or manipulation of a computer network and its resources. In this blog, we will explain what network security is, network security objectives, different types of network threats and attacks, and types of network security measures. In the end, we will define some courses one can take to make a career in network security. Let’s first understand what Network security really is. Network security is the practice of protecting a network and its devices, data, and users from unauthorized access, misuse, or malicious attacks. Network security is vital for any organization that relies on the internet or other networks to communicate, share, or store information. Network security is usually overseen by a network administrator who makes use of network security policies into practice as well as setting up network gear and software to: Let’s now understand network security objectives or goals in detail. The primary network security objectives include confidentiality, integrity, and availability. Let’s understand the CIA triangle in detail. It simply means that data and resources on a network can only be accessible by authorized users. In return, it assists in protecting sensitive information from unauthorized users. This simply ensures that the data, as well as resources on a network, are not altered or corrupted by unauthorized parties. With the help of integrity, one can maintain the accuracy as well as consistency of information and processes. This assists in ensuring that the resources and data on a network are accessible and usable by authorized parties. Further, availability helps to support the continuity and performance of business operations and services. Apart from all the goals discussed above, there are some other goals of network security, such as: We now have a basic understanding of different network security objectives. Let’s now move on to the network security threats and attacks. Do check out – Security of Wireless Networks Network Security threats and attacks are defined as the sources of damage that are carried out by hackers in order to either steal information or sometimes alter the information. Network security threats and attacks are classified into two categories. These are: You can also learn the difference between Active and Passive Attacks. Below, we have discussed some of the network security threats and attacks for better understanding. To understand the Network Security Objectives, one needs to understand the types of network security. So, let’s understand some of the measures one can take against network security threats and attacks to protect businesses and personal data. In order to protect businesses as well as personal data, there are various types of networking technologies that can be used to protect networks from cyber threats. Below, we have discussed some of the most common ones. A software or hardware device that filters network traffic coming in and going out based on predefined rules. Firewalls can be placed at the edges of a network. Used internally to divide a network into smaller subnetworks. Programs that scan computers or devices for malware infections and remove them. These software tools can also block downloads or attachments, thereby preventing malware from entering the network. A system that verifies and permits users to access the network and its resources. NAC can also enforce policies based on job functions, granting privileges to users accordingly. The process of converting data into a form using a secret key. Encryption is utilized to safeguard data while it is being transmitted or stored, rendering it incomprehensible to individuals or hackers. A private network that establishes a secure tunnel between multiple devices over a public network like the Internet. This ensures privacy and security for data transmission between these devices. A Virtual Private Network (VPN) can be used to secure and safeguard data while transmitted to conceal the identity and whereabouts of users. SIEM, which stands for Security Information and Event Management, is a system that gathers, collects, assesses, and alerts about security-related information from sources like firewalls, antivirus software, NAC systems, or intrusion detection systems (IDS). SIEM aids in identifying and reacting promptly to cyberattacks and security breaches. Now, many readers must be curious about how one can make a career in the network security domain. Below, we have added some of the courses for better understanding. In order to achieve excellence in network security, one must choose any of the below-mentioned courses. These are the courses one can take to take on network security. The main objective of network security is to prevent any unauthorized access to the network data as well as resources. The three main objectives of security are: Confidentiality, Integrity, and Availability. The three main objectives of networking are: The objective of Internet security is to protect data and systems from unauthorized access, use, modification, or destruction. Network security is an essential aspect of cybersecurity that protects network data and resources from attackers. Network security has three main objectives: to prevent unauthorized access, to detect and stop cyberattacks, and to ensure secure access for authorized users. In this blog, we have explained network security objectives, different types of network security attacks or threats, and different types of network security measures. Apart from that, we also have added some network security courses one can take to make a career out of it.Introduction
What is Network Security?
Network Security Objectives
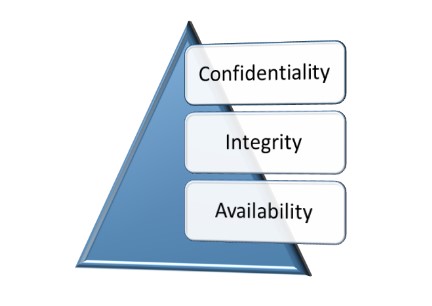
Confidentiality
Integrity
Availability
Different types of Network security threats and Attacks
Types of Network Security
Firewall
Antivirus and anti-malware software
Network Access Control (NAC)
Encryption
Virtual Private Network (VPN)
SIEM
Network Security Courses
Frequently Asked Questions
Q1. What is the objective of network security?
Q2. What are the main three 3 objectives of security?
Q3. What are the objectives of networking?
Q4. What is the objective of Internet security?
Conclusion







