Difference Between DoS and DDoS Attacks
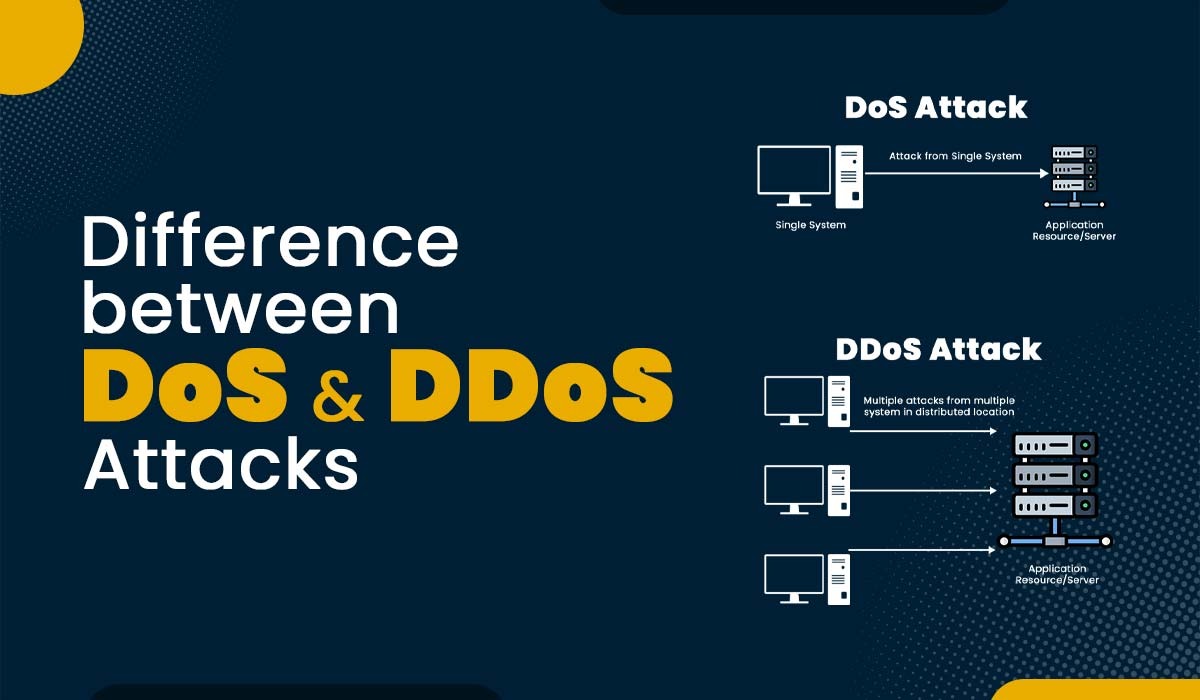
The modern age of technology is seeing a rise in the number of cyber-attacks, with DoS and DDoS attacks being the most popular forms of such attacks. The purpose of such attacks is to cause a website or network to become unavailable to its intended users by flooding it with an excessive amount of traffic or requests, resulting in an overload and subsequent crash. Regardless of the common goal of these two forms of attacks, there exists a significant difference between DoS and DDoS attacks. Learn more about these attacks with PyNet Labs’ Certified Ethical Hacker Course. A Denial-of-Service attack, or DoS, occurs when one computer floods another with so much data that it crashes it. By flooding the server with requests, this attack may take down any website hosted on the internet. The attacker uses a single computer or device to send malicious packets or data to the target system, exploiting its vulnerabilities or exhausting its resources. As a result, the target system cannot process legitimate requests from normal users and may crash or slow down significantly. Here are some examples of DoS attacks – A Distributed Denial of Service or DDoS attack occurs when multiple devices overload a server, service, or network with an excessive amount of network traffic and, as a result, make it inaccessible to the client. It’s like an unexpected traffic jam that blocks the road and prevents regular traffic from moving. A DDoS attack can generate much more traffic and requests than a DoS attack, making it harder to detect and stop. It can also target different layers of the network layers, such as the application layer, the transport layer, or the network layer. Below we have given some examples of DDoS attacks – These are the major differences between DoS and DDoS attacks. Let’s understand these differences in detail. The main difference between the two attacks is that in the case of a DoS attack, a single device is used to carry out the attack on the client, and in the case of a DDoS attack, multiple devices are used to carry out the attack. Below we have discussed some of the common difference between DoS and DDoS attacks based on different factors. Now, we have a basic understanding of DoS vs DDoS. Let’s now see the similarities between the two. Here are some similarities – Now, let’s understand the various types of DoS and DDoS Attacks. A wide variety of DoS and DDoS attacks can be utilized for different purposes. The goal may be to harm a company’s reputation, divert attention from other attacks, or make a political statement. Below we have explained different types of such attacks. DoS and DDoS attacks can cause serious damage to the network and website services. Therefore, taking some preventive measures and implementing security solutions to protect yourself from these attacks is important. Some of the best steps that you can take to protect from DoS and DDoS attacks are: These are some ways that can protect you from DoS and DDoS attacks. Yes, DDoS attacks are more dangerous than DoS attacks because they come from multiple devices, whereas DoS attacks come from an individual machine. That’s why it’s difficult for teams and security products to identify the root of attacks. Additionally, if there are multiple resources and they must be located and secured to protect against persistent attacks, the confusion and risk of DDoS attacks increase. A denial-of-service attack or DoS is a kind of attack that originates from one source. DDoS refers to a distributed denial of service attack. This suggests that more than one computer is contributing to the assault flow. There are three main types of DoS and DDoS attacks: DoS stands for Denial-of-Service attack, which is carried out from a single computer or device by flooding it with requests that make a server or a website crash. One example of a DoS attack is when the attacker makes the server busy during a sale on an e-commerce website by sending so many requests. As a result, the original buyer or user won’t be able to access the website. Yes, DoS is an active attack that focuses on sending multiple requests from a single machine to make a server crash or inaccessible to the client or user. Both the DoS and DDoS attack pose a greater threat to the organization and businesses. In comparison, the impact of a DDoS attack is much greater when compared to a DoS attack. However, it is critical to take some steps in order to safeguard one’s organization against such attacks. This blog covers DoS vs DDoS and different types of DoS and DDoS with some steps that can be taken to protect your system from such attacks. If you have any questions or comments, please feel free to share them below in the comment section.Introduction
What is DoS Attack?
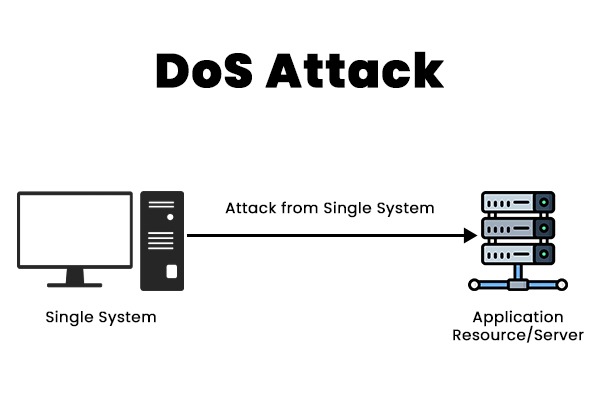
What is a DDoS attack?
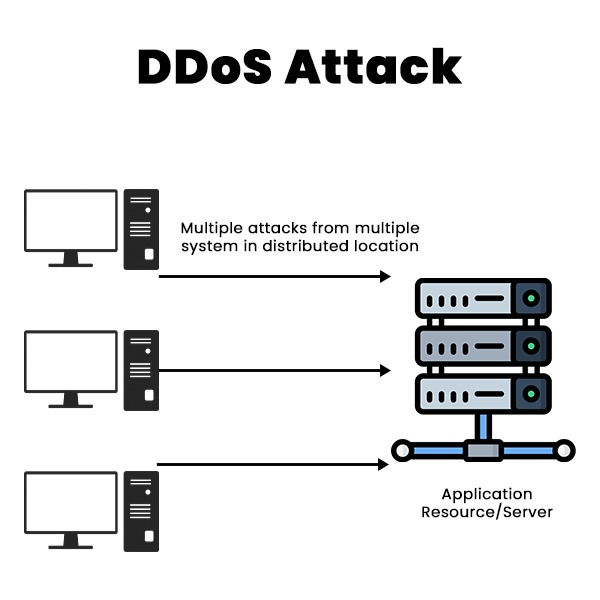
Difference between DoS and DDoS attack
Factors DoS Attack DDoS Attack Full Form Denial of Service Attack Distributed Denial of Service Attack Device A single device is used Involves a number of devices Pace Are generally slow in nature Faster than a DoS Attack Detection Can be detected easily as the traffic is less Very Difficult to detect as traffic comes from various sources that look legitimate Volume The volume of traffic is less The volume of traffic is very high Preventation Can be prevented easily Very difficult to prevent Loss DoS attacks can result in loss of revenue and reputation It can result in loss of revenue, reputation and increased cost for recovery, and security. Preventation DoS attacks can be prevented easily by using optimal security measures DDoS attacks are not easy to prevent as they involve compromised devices that are not under control of the victim Execution Manner Executed from a single device utilizing a script or software It utilizes a command-and-control (C&C) server
Similarities between DOS and DDOS
Types of DoS Attacks and DDoS Attacks
How to Protect from DoS Attacks and DDoS Attacks?
Is DDOS more dangerous than DOS?
Frequently Asked Questions
Q1 – What is the difference between a DoS and a DDoS attack?
Q2 – What are the three types of DoS and DDoS attacks?
Q3 – What is DoS attack and example?
Q4 – Is DoS an active attack?
Conclusion







