Difference between Active Attack and Passive Attack
Clearly, the Internet is one of the most significant innovations of our time. It has simplified our life in more ways than we can even count. This development has similarly exposed us to a wide variety of cyberattacks. Cybersecurity attacks pose a greater threat to all that is part of the Internet. Cybersecurity threats are further classified into active attack and passive attack. But what exactly are these attacks? This blog will mainly focus on cybersecurity attacks, their types, and the basic difference between active and passive attacks. Before getting into more details, let’s first understand Cyber security attacks. When someone takes illegal or unauthorized steps that put the security of a system at risk, it is known as a cyber security attack. These kinds of attacks aim to corrupt, delete, or steal private data or information. Mainly Cyber security attacks are of two types, i.e., active attack and passive attack. Join Ethical Hacking Course to learn more about cyber attacks and how to save your organization from these attacks. Let’s first understand what active attacks really are in detail. In an active attack, the hacker deliberately attempts to alter the original message or data. These types of attacks pose a significant risk to the system’s integrity and availability. These assaults cause harm to systems and may even modify data. Due to the wide variety of physical and software weaknesses, protection against these assaults is challenging. The adverse effects caused by these attacks can have significant consequences on the system and its resources. One positive aspect of this attack is that the victim is alerted when an active attack is being carried out. Rather than prioritizing prevention, the emphasis is placed on the detection of attacks and the subsequent restoration of the system. An active attack usually requires more effort and involves more challenging consequences. The following are a few preventive measures to take when facing such attacks: Active attacks are classified into four types. These are: We have studied active attacks and their types in detail; now, let’s move on to passive attacks and their types. In passive assaults, the attacker just monitors in on messages and steals any information they can get their hands on. They have dedicated themselves to monitoring every message and gathering information. The attacker does not attempt to change the content of the information he steals. These assaults pose a serious danger to the privacy of your information but can do no actual damage to the system. Since no data or information modification is involved, Passive attacks are harder to detect than Active ones. As a result, the attacked person has no idea they are being attacked. However, there are encryption methods that can be used to stop this. This makes the communication inaccessible to hackers at any stage of the transmission process. This is why it’s important to focus on prevention rather than detection. Below we have shown some of the preventive measures that one can take to prevent such attacks: Passive attacks can easily take many forms, but it has been divided further into two. These are: Till now, we have studied active attack and passive attack and also their types in detail. Now let’s understand the basic difference between them. Below we have explained the difference in tabular form – These are the difference between Active and Passive Attacks. Mainly cyber security attacks are classified into two categories. These are – Active Attack and Passive Attack. The basic difference is in their mode of operation. When we talk about an active attack, the attacker updates or changes the data or information meant for the client. In the case of a passive attack, the attacker observes the information for a period of time to see the client’s behaviour and also stores that information for the future. An active attack is a type of cyberattack that involves modifying, deleting, or injecting data into a network or system. Active attacks are carried out in different forms. Some of which are: We have covered detailed information about cyber security attacks, i.e., active attack and passive attack. So, the main difference between active attack and passive attack is that Active attacks involve direct actions by an unauthorized entity to compromise a system, while passive attacks are attempts to gain unauthorized access or information without directly affecting the system’s operation. We can confidently conclude that such attacks bring significant risks to any company and can result in significant damage. It is critical to take some preventive measures to protect from such attacks. Feel free to leave a comment below if you have any questions or concerns about this topic.Introduction
What is a Security Attack?
What are Active Attacks?
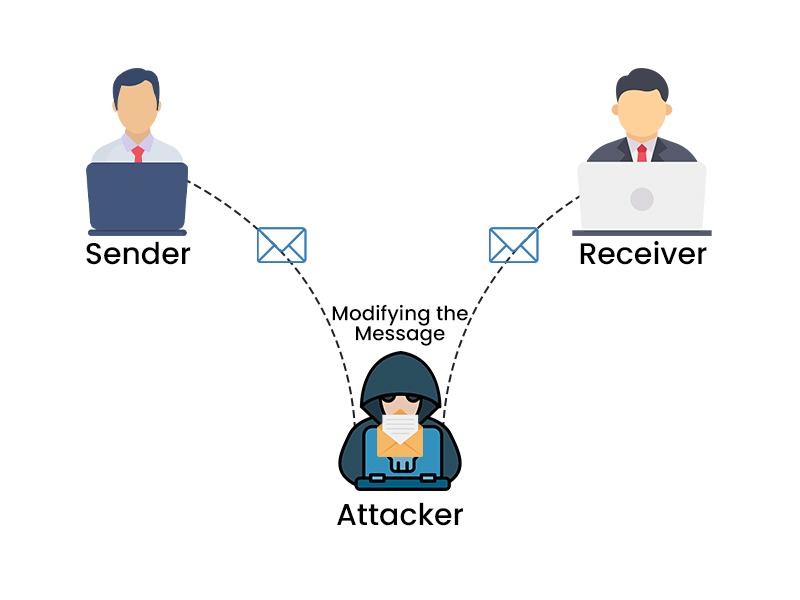
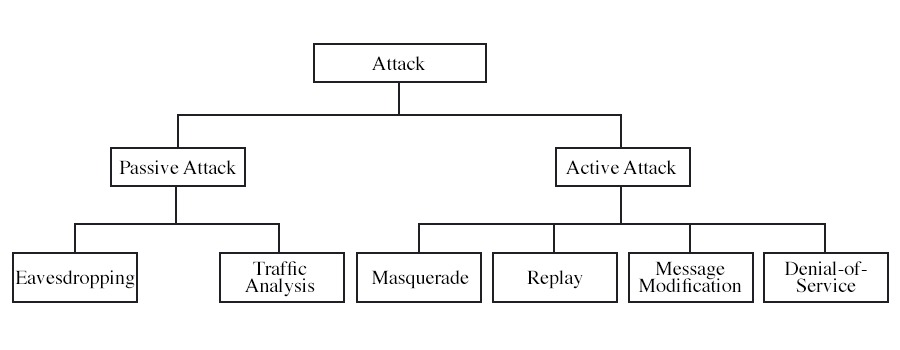
Types of Active Attacks
What are Passive Attacks?
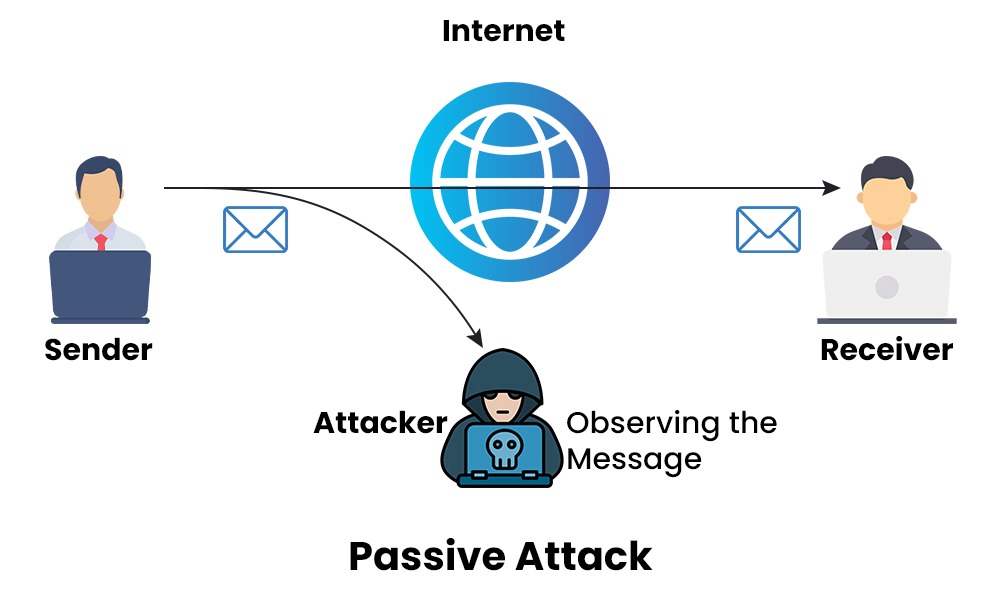
Type of Passive Attacks
Difference between Active Attack and Passive Attacks
Parameters Active Attacks Passive Attacks Initiation Actively Initiated by the attacker. Attacker passively observes and collects information. Interaction Involves direct interaction with the system or network. No direct interaction. Objective To change or disrupt data or systems. To collect or observe information. Frequency Mostly less frequent as it involves higher risk and visibility. Can be frequent as it relies on stealth and might go undetected for a long period of time. Impact Data integrity, availability, or confidentiality may be compromised; system functionality or performance may be degraded or disrupted; unauthorized access or control may be gained. Data confidentiality may be compromised; system behaviour or configuration may be revealed; network topology or activity may be mapped. Detection Easier to detect due to changes or anomalies in data or systems. Harder to detect due to the lack of changes or anomalies in data or systems. Visibility Visible and leaves traces in logs and network traffic. Less visible and often leaves minimal traces. Prevention It can be prevented or mitigated by using encryption, authentication, authorization, firewall, antivirus, etc. It can be prevented or mitigated by using encryption, obfuscation, masking, tunneling, etc. Response Time Requires immediate response as attacker is actively affecting. Response time may delayed as it doesn’t affect user in real-time. Duration The duration of the active attack is lower compared to the passive attack. The duration of the passive attack is much longer as it is based on observing the data for as much time as possible. Example Denial-of-service, replay, masquerade, message modification Eavesdropping and traffic analysis. Common Techniques Exploiting vulnerabilities, Sending malicious payloads, Brute-force attacks Sniffing, Social Engineering, Passive reconnaissance Frequently Asked Questions
Q1 – What are the two basic types of attacks?
Q2 – What are the basic difference between passive and active attacks?
Q3 – What is an active attack?
Q4 – What are the various active attacks?
Conclusion







