What is ICMP (Internet Control Message Protocol)?

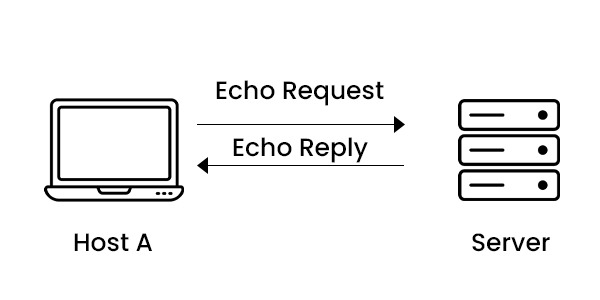
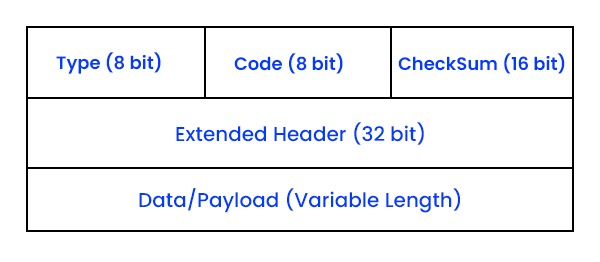
The Internet is a web of interconnected devices that communicate using protocols. One such protocol is the Internet Control Message Protocol (ICMP), which helps network devices diagnose communication issues. ICMP protocol plays a significant role in determining whether the data is reaching its intended destination on time or not. Typically, routers and other network devices utilize the ICMP protocol. In this blog, we will mainly focus on what ICMP in computer networks is, its history, purpose, and how it works, and last, we will look into how ICMP is used in DDoS attacks. Let’s first understand what ICMP is. ICMP or Internet Control Message Protocol is a kind of protocol that operates at the network layer on top of the Internet Protocol (IP). IP handles the transportation of data packets between sources and destinations, whereas ICMP is responsible for transmitting control and error messages among network devices. For instance, if a router encounters an issue while forwarding an IP packet, it can utilize ICMP to send an error message to the source host. Similarly, if a host wishes to assess connectivity or latency with another host, it can employ ICMP to transmit an echo request and await an echo reply. ICMP messages are enclosed within IP datagrams. This means they consist of an IP header followed by an ICMP header and accompanying data. The ICMP header contains two fields: type and code. The type field specifies the purpose of the message (echo request, echo reply, destination time exceeded). On the other hand, the code field provides information about the message type (e.g., reason for error or query subtype). Now that we have a basic understanding of ICMP protocol, let’s discuss its history. ICMP came into action in 1981 as part of the TCP/IP suite of protocols as defined in RFC 792. Its purpose was to offer feedback regarding communication issues and assist tools, like ping and traceroute. Initially meant for IPv4, the fourth version of IP. A newer version of ICMP, also known as ICMPv6 (defined in RFC 4443), came into action with the introduction of IPv6, the sixth version of IP, in 1998. ICMPv6 differs from ICMPv4 by employing message types and codes. It supports IPv6 features like fragmentation and neighbor discovery and integrates security measures such as IPsec. ICMP serves two purposes in computer networks: error reporting and querying. Error reporting is used to notify hosts or routers about issues that arise during the transmission of IP packets. For instance, if a router cannot find a route to the intended destination host, it can send an ICMP message indicating that the destination is unreachable back to the source host. This helps the source host become aware of the problem and either halt transmissions or explore routes. Querying, on the other hand, is employed to request or provide information regarding the status or configuration of hosts or routers. Let’s say a host wants to determine the round-trip time or hop count to another host; it can send an ICMP message requesting an echo. Wait for an ICMP reply carrying that echo. This enables the host to measure latency or trace its route to reach its intended destination. By offering feedback and diagnostic functions, ICMP helps overcome the limitations of IP. For example, IP lacks a built-in mechanism for sending error or control messages as reliable delivery service and congestion control mechanisms. By utilizing ICMP, network devices are able to communicate errors, queries, and congestion information without relying on higher-layer protocols like TCP or UDP. Here are the various types of ICMP Protocol messages – Let’s move on to understand the working of ICMP. ICMP operates by exchanging messages between network devices using IP datagrams. An ICMP message comprises an IP header followed by an ICMP header and data. The IP header contains details like source and destination addresses, protocol number (1 for ICMP) and a checksum. The ICMP header includes information such as message type, code, another checksum and optional identifier, and sequence numbers. The data section carries information depending on the type and code of the message. When a network device sends an ICMP message, it packages it within an IP datagram. Forward it to the specified destination address mentioned in the IP header. Upon receiving an ICMP message, a network device unpacks it from the IP datagram. It then checks the type and code fields in the ICMP header. Based on these values, different actions or responses may be triggered. The most common type of ICMP message is an echo request or echo reply, which is primarily used for the ping utility. An echo request is a message that sends a response from the destination device. In contrast, an echo reply is a confirmation that the destination device has indeed received the echo request. The ICMP header contains two fields for the echo request and reply messages. Identifier (16-bit): A number that helps to match the echo request and reply messages. Sequence number (16-bit): A number that increments with each echo request and reply message. The ICMP protocol header comes before the IPv4 and IPv6 packet headers. The first 32 bits of the packet hold three fields in the ICMP packet format: Type (8-bit): For message type, the first 8 bits of the packet provide a short description of the message. This allows the receiver to identify what type of message it is receiving and how to respond to it. Here are some common message types: Code (8-bit): The code is the next 8 bits of the ICMP packet format containing the error message and some additional information. Checksum (16-bit): In the ICMP packet header, the last 16 bits are for the checksum field. The checksum helps check the number of bits in the complete message and enables the ICMP tool to ensure that the complete data is sent. The Extended Header is the next 32 bits of the ICMP header that identifies the problem in the IP message. The byte locations are analysed through a pointer containing the problem message and the receiving device looks here to see the problem. The last part of the ICMP packet is the Data or Payload of variable length. The bytes involved in IPv4 are 576 bytes and in IPv6 are 1280 bytes. Below, we have explained how ICMP protocol can be used for DDoS attacks. This is a type of DDoS attack that involves sending a large number of ICMP echo request messages to a target from multiple sources. The target has to process and respond to each echo request message, which consumes its resources and bandwidth. If the target cannot handle the incoming traffic, it may slow down or crash. This is a type of DDoS attack that involves sending malformed or oversized ICMP echo request messages to a target from multiple sources. The target may not be able to handle or process the invalid packets, which may cause it to crash or reboot. This is a type of DDoS attack that involves sending ICMP echo request messages with a spoofed source address to a broadcast address on a network. The broadcast address is a special address that reaches all devices on the network. The devices on the network will respond to the echo request messages by sending ICMP echo reply messages to the spoofed source address, which is actually the target. The target will receive a large amount of unsolicited traffic from multiple sources, which may overwhelm its resources and bandwidth. Two important limitations of Internet Control Message Protocol are mentioned below – The router rejects data transmission due to an error and there is no mechanism in the Internet Control Message Protocol to notify the sender of this error. For example: while surfing the Internet the lifetime of the data packet has expired and the value of the time live field in the data packet has become zero; If the data packet will be rejected. Generally, one device needs to connect to another, in such a situation ICMP protocol has no process to transmit information to the device. For example: The host has to analyze whether the destination is still active after sharing the data. These are the limitations of ICMP Protocol. ICMP serves as a means for reporting errors and diagnosing networks. It relies on messages like echo requests, echo replies, and time exceeded. Unlike TCP or UDP protocols, ICMP operates without establishing a connection. Its purpose revolves around network management tasks such as error reporting and synchronization. ICMP acts as a protocol facilitating the exchange of error and control messages among network devices. The tool known as Ping utilizes ICMP to assess the connectivity and latency of a device by sending out echo requests and awaiting replies. Ping leverages the ICMP protocol to create connectivity between two devices. ICMP, short for Internet Control Message Protocol, functions at the network layer by transmitting error and control messages. When Ping launches ICMP echo requests, it patiently anticipates matching ICMP echo replies. ICMP protocol serves at the network layer, enabling network devices to exchange information regarding errors, queries, and congestion. It plays a role in diagnosing and resolving network issues. It can also be misused by attackers to carry out DDoS attacks. This blog explains ICMP, its significance, and its historical background. Additionally, we explore the misuse of ICMP in computer networks for executing DDoS attacks.Introduction
What is ICMP Protocol?
History of ICMP
What is ICMP used for?
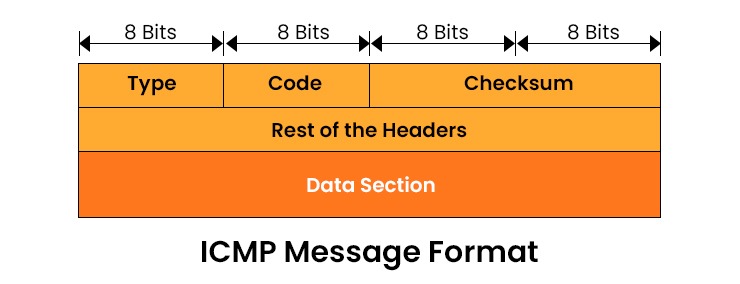
Types of ICMP Messages
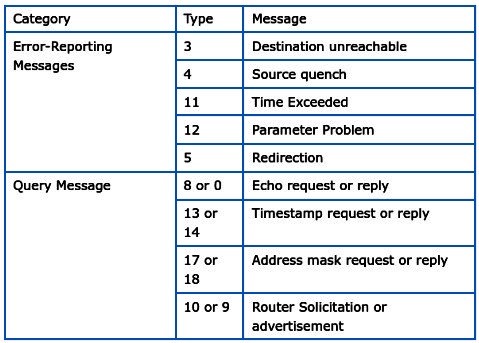
How does the ICMP Protocol work?
ICMP Packet Format
How is ICMP Protocol used in DDoS Attacks?
ICMP flood attack
Ping of death attack
Smurf attack
Limitations of Internet Control Message Protocol
No Error Reporting
No Communication
Frequently Asked Questions
Q1. Where is ICMP protocol used?
Q2. Is ICMP a TCP or UDP protocol?
Q3. What is ICMP and ping?
Q4. Is ping an ICMP protocol?
Conclusion







