What is Device Hardening?
The internet has completely transformed how we communicate, work, learn, and entertain ourselves. It has also brought new opportunities for innovation, collaboration, and creativity. Along with these opportunities come risks. Cyberthreats are constantly becoming more sophisticated, targeting not only large organizations and governments but also individuals and small businesses. These cyberattacks can compromise the confidentiality, integrity, and availability of data, devices, and networks. In order to protect data from these cyberattacks, we must take measures to secure devices and systems. One effective approach is through a process called device hardening. In this blog, we will explain device hardening, its purpose, and the different types and practices of device hardening in order to secure your device. Before getting into more details, let’s first understand the meaning of device hardening. Device hardening refers to securing a device by minimizing its vulnerability to threats by reducing its attack’ surface area. This involves decreasing exposure points like ports or services on the device, protocols or applications that could be exploited, or even user accounts that may pose risks if not properly configured. Vulnerabilities are essentially weaknesses or flaws in a device’s software or hardware that malicious actors can exploit to gain access or cause harm. Device hardening has the goal of reducing the areas that can be attacked and addressing or lessening the weaknesses of a device. The objective is to make it more resistant and less susceptible to cyberattacks. This procedure goes beyond safeguarding software; it encompasses a strategy that involves securing software applications, operating systems (OS) firmware, databases, and networks. The main purpose of device hardening is to improve the security and reliability of a computer system. By hardening a device, you are making it more difficult for hackers to break into it and compromise its functionality or data. Device hardening can also help you comply with various security standards and regulations that may apply to your industry or organization. Device hardening helps to: Let’s now understand the different types of device hardening. There are different types of device hardening depending on the level and scope of security required. Below, we have discussed the different types in detail. This involves securing the ports, data, permissions, and functions of a data server. Some common practices for server hardening include using strong passwords, locking user accounts after a certain number of failed login attempts, implementing multi-factor authentication, disabling USB ports, etc. This involves securing the applications deployed on the server. Some common practices for hardening software applications include using antivirus, spyware, malware protection applications, establishing intrusion detection systems, etc. This involves securing a system’s own operating system. Some common practices for securing the operating systems of servers include limiting access to work with operating systems among personnel, uninstalling unnecessary device drivers, etc. This involves securing the data stores of any enterprise. It mainly consists of three parts- Some common practices for database hardening include implementing a role-based-access policy, restricting admin and user privileges, etc. Hardening of network devices involves securing the channel that is used for communication between two ports. The most effective way to ensure a secure network is to establish an intrusion detection system in the communication channel which helps in the detection of a potential attack in advance. Configuring firewalls and encrypting your organization’s network traffic is also a good practice for hardening your network. Below, we have explained different practices for device hardening that one must take in order to protect from cyber threats. Device hardening is not a one-time activity; it requires continuous monitoring and updating to keep up with the changing threat landscape. Some of the best practices, or we can call these device hardening checklists for device hardening include using secure configuration settings, applying security patches and updates, implementing strong authentication and authorization mechanisms, encrypting your data and communications, and monitoring and auditing your devices and systems. By following these best practices, you can achieve a high level of device hardening that can protect your devices and systems from cyber threats. The first practice is to use secure configuration settings for devices and systems. This means disabling or removing any unnecessary features, services, or functions that can pose a security risk or create a vulnerability. For example, one can disable remote access or file sharing if they don’t need them or limit them to authorized users only. Another important step in device hardening is to apply security patches and updates regularly for their devices and systems. These patches and updates fix any known bugs or flaws that can be exploited by hackers or malware. It is always mandatory to monitor security bulletins that are applicable to the system’s operating system and applications and act accordingly. A crucial aspect of device hardening is to implement strong authentication and authorization mechanisms for your devices and systems. Authentication refers to verifying the identity of a user or device before granting access to a system or resource. Authorization refers to granting or denying access based on predefined rules or policies. One should make use of strong passwords that are not easy to guess or crack and change them frequently. One can also use multi-factor authentication (MFA) which requires more than one piece of evidence (such as a password and a code sent to your phone) to verify your identity. It is highly recommended to implement a role-based-access policy that defines the level of access and permissions that each user or device has based on their role and responsibility. One of the most crucial practices for device hardening is to encrypt your data and communications. Encryption is a technique by which one can transform their data into an unreadable form that can only be deciphered by authorized users. With the help of encryption, one can protect data from any unauthorized access or modification. One can make use of secure protocols such as HTTPS, SSL, or TLS for their communication. VPN is also recommended in order to create a secure connection between the two parties. Last but not least, practice for device hardening is to monitor and audit your devices and systems. Monitoring refers to collecting and analyzing data about the performance, behaviour, and activity of your devices and systems. When we talk about auditing, it refers to reviewing and verifying the compliance and effectiveness of security policies and controls used in systems. For auditing and monitoring, one can use various tools such as antivirus, IDS, IPS, etc. It is highly recommended to do vulnerability scans and penetration tests regularly. This will not only help identify the security gaps but also assist in fixing them. Some of the benefits of device hardening are: There are many methods that can be used to harden a device. Some of these are: Hardware hardening is the process of improving the security of the hardware. With the help of hardware hardening, one can make it difficult for attackers to access or make any changes to the functionalities by reducing the attack surface. Device hardening is the process of securing a device by reducing the attack surface. One can take different measures in order to achieve device hardening, such as applying security configurations, patches, antivirus software, etc. Device hardening is a crucial technique that assists in protecting devices or systems from cyber threats. In this blog, we have explained device hardening in detail, along with its purpose and its different types. We also discussed different practices or proactive measures that one can take to protect their devices from cyber incidents. Feel free to use the comment section if you have any doubts or suggestions.Introduction
What is Device Hardening?
Purpose of Device Hardening
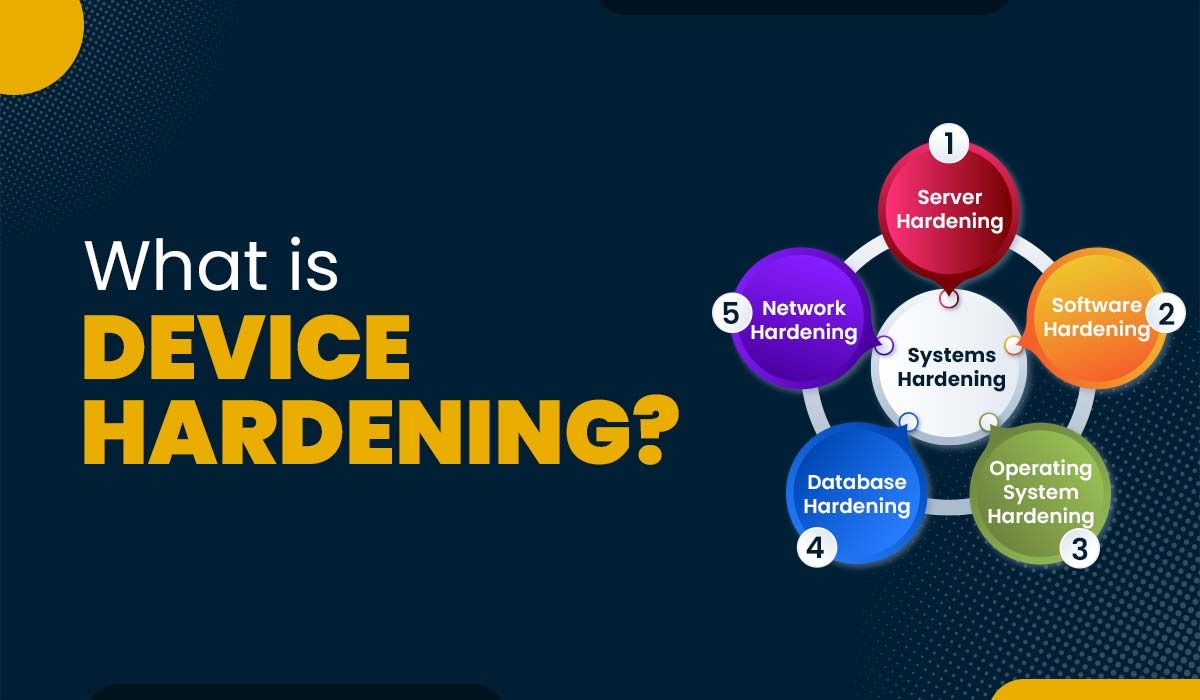
Types of Device Hardening
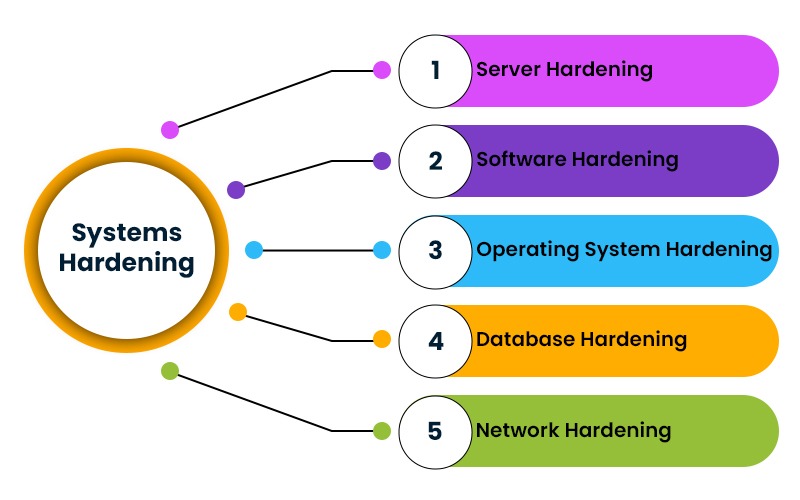
Server Hardening
Software Application Hardening
Operating System Hardening
Database Hardening
Network Hardening
Best Practices for Device Hardening
Use Secure Configuration Settings
Apply Security Patches and Updates
Implement Strong Authentication and Authorization Mechanisms
Encrypt Data and Communications
Monitor and Audit Devices and Systems
Frequently Asked Questions
Q1. What are the benefits of device hardening?
Q2. Which method can be used to harden a device?
Q3. What is hardware hardening?
Q4. What is meant by device hardening?
Conclusion







