Objectives of Cyber Security

As technology advances, so does the reliance of businesses on digital services and networks. We all are either directly or indirectly dependent on the security and integrity of online systems in order to protect personal data as well as business operations. Cybersecurity is of utmost importance nowadays, as we all know that cyberattacks can cause serious damage to individuals and organizations. When we talk about the objectives of cyber security, it simply is to protect the data and systems from unauthorized access and modifications. In this blog, we will explain the cyber security objectives along with the measures one can take to protect crucial data from attackers. Before getting into more details, let’s first understand the purpose of cyber security. Below, we have mentioned some of the purposes of cybersecurity – Let’s now understand the different cyber security objectives. The main objectives of cyber security are to protect the confidentiality, integrity, and availability of information and systems. These are also known as the CIA triad and form the basis of all security programs. Apart from the CIA triad, there are also some other important cyber security goals or objectives. We will look into all the cyber security objectives in detail. Let’s Begin! Integrity simply means to ensure the data as well as systems must be accurate, complete, and consistent and have not been modified without the user’s prior permission by any unauthorized parties. The two most important aspects one always looks for in the information and processes are trustworthiness and reliability. Integrity is crucial in maintaining both these aspects. Integrity can be compromised by different cyberattacks that can indirectly alter as well as delete data. Sometimes accidental errors that may lead to corrupting the data also can compromise integrity. There are various measures one can take in order to achieve integrity, some of these are: Availability is simply to ensure that the data as well as systems are accessible and functional whenever needed by authorized parties. With the help of accessibility, one can maintain the continuity and efficiency of operations and services without delaying and wasting any time. It can also be compromised by cyberattacks that can lead to the disruption or denying access to the data as well as systems. Disruption or denying sometimes can also by accidental failures that cause downtime. Some of the cybersecurity measures one can take to achieve availability are: Confidentiality is also one of the objectives of cyber security which ensure that the data as well as system are protected from any unauthorized disclosure and exposure. It is one of the most essential in terms of maintaining the privacy and secrecy of information and processes. Like all others, it can also be compromised by different types of cyberattacks which can lead to stealing or leakage of crucial data. Sometimes accidental breaches can also lead to expose the data. Below we have suggested some of the cybersecurity measures in order to achieve confidentiality – Access control is to ensure that data as well as systems should only be accessed by authorized parties based on their roles, permission, and needs. It is essential to enforce the principle of least privilege. In other words, it means that the users should only be given the minimum access rights i.e., only those who are required to perform a specific task. Access control can also be compromised by cyberattacks that bypass or exploit access control mechanism. Sometimes accidental incidents such as granting access to inappropriate users can also lead to question the safety of the data. Some of the cybersecurity measure in order to achieve access control are: Authentication is one of the important objectives of Cyber Security. It is to ensure that users or devices are who they claim to be. It is crucial in a place where one has to verify the legitimacy and accountability of users or devices. Authentication can also be compromised by various cyberattacks that intend to show that they are the real user (Spoofing). Sometimes accidental cases such as allowing unauthorized or unauthenticated users to access data or applications. Some of the cybersecurity measures one can take are: Encryption is to ensure that the data should be transformed into unreadable formats or patterns that can only be decrypted by authorized users. It is one of the most crucial factors that assist in protecting the confidentiality, integrity, and authenticity of data. Encryption can also be compromised by different cyberattacks that either break or crack the encryption algorithms or keys. Sometimes accidental cases also impact the safety of data such as losing or exposing encryption keys. Some of the cybersecurity measures are: Compliance is to ensure that the data as well as systems adhere to the laws, standards, regulations, and policies. It is an essential objective that assists in maintaining the legibility, accountability, and responsibility of data or systems. Still, compliance can be compromised by different cyberattacks and can violate or evade compliance requirements. Accidental incidents can also lead to non-compliance penalties or sanctions. Some of the cybersecurity measures one can take to achieve compliance are: Incident response means ensuring that data and systems are prepared for, detected, analyzed, contained, eradicated, recovered from, and learned from cyber security incidents. It is among the most important Cyber Security Objectives. Incident response is essential for minimizing the impact and damage of cyber security incidents and restoring the normal operations and services of data and systems. Incident response can be compromised by malicious attacks that hinder or prevent incident response activities or by accidental incidents that delay or worsen incident response outcomes. To achieve incident response, cyber security measures include: Security architecture simply ensures that the data as well as systems are designed, developed, deployed, operated, and maintained securely. It is crucial for integrating security into the entire lifecycle of data and systems. Security architecture can also be compromised by carrying out various cyberattacks that will exploit design flaws and sometimes implementation errors. One can also lead to vulnerability or weakness in data or systems via some accidental incidents. Some of the cybersecurity measures that one can take in order to achieve security architecture are: The next one in Cyber Security objectives is Auditing. Auditing means evaluating, monitoring, and reporting the performance, compliance, and effectiveness of a cybersecurity system. It also means identifying the strengths, weaknesses, opportunities, and threats of a cybersecurity system and providing recommendations for improvement. Auditing is important for ensuring that the cybersecurity system meets the standards, expectations, and objectives of an organization and its stakeholders. To conduct auditing, organizations can use methods such as security audits, security assessments, or security reviews. These are the various objectives of Cyber Security. Cyber Security objectives are to protect data or systems from any unauthorized access that can further lead to modifications as well as stealing it. The three main objectives of information security are: The aims and objectives of cyber-attacks are to steal or damage sensitive data either from computer systems, networks, or devices. The objectives of cyber crime and security are to prevent and respond to attacks that are carried out by attackers in the hope of minimizing the damage from cyber incidents or completely preventing it. This requires a combination of institutional structures, people, processes, technology, and cooperation. Cybersecurity is a complex and dynamic field that has many objectives that we have gone through. The objectives of Cyber security and its goals align towards protecting the data, systems, and networks from cyber threats in order to ensure confidentiality, integrity, and availability. Cybersecurity also involves access control, authentication, encryption, compliance, incident response, security architecture, and auditing. We hope this blog will help you understand the different Cyber Security objectives. If you have any doubts or suggestions, feel free to use the comment section below. You can also start your Cyber Security Career with PyNet Labs’ Online CEH Course.Introduction
Purpose of Cyber Security
Objectives of Cyber Security
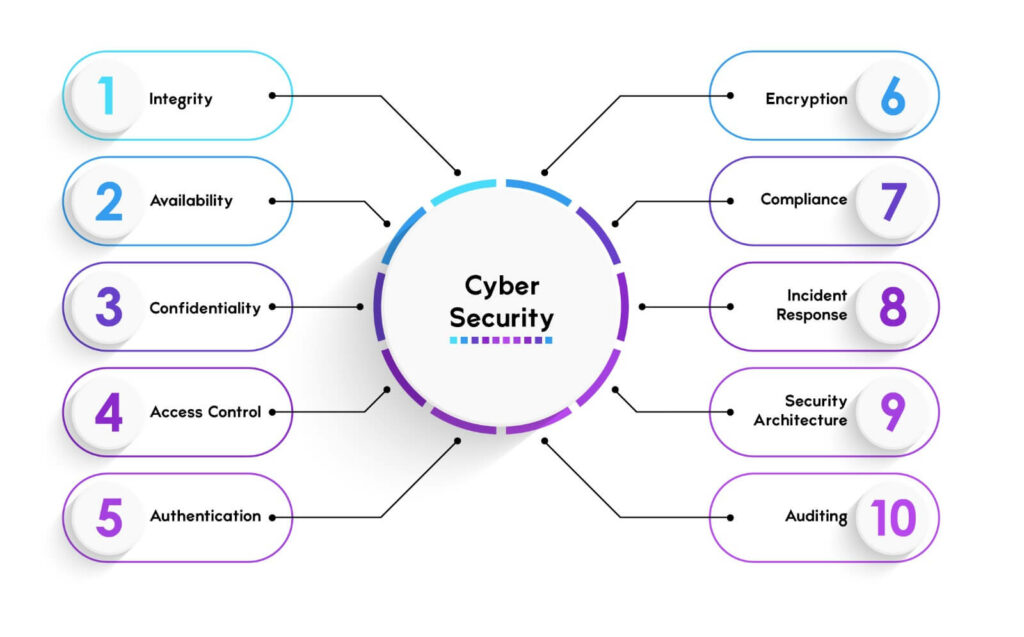
Integrity
Availability
Confidentiality
Access Control
Authentication
Encryption
Compliance
Incident Response
Security Architecture
Auditing
Frequently Asked Questions
Q1. What are cyber security objectives?
Q2. What are the 3 main objectives of information security?
Q3. What are the aims and objectives of cyber attacks?
Q4. What are the objectives of cyber crime and security?
Conclusion







