What is Cisco ASA (Adaptive Security Appliances)?
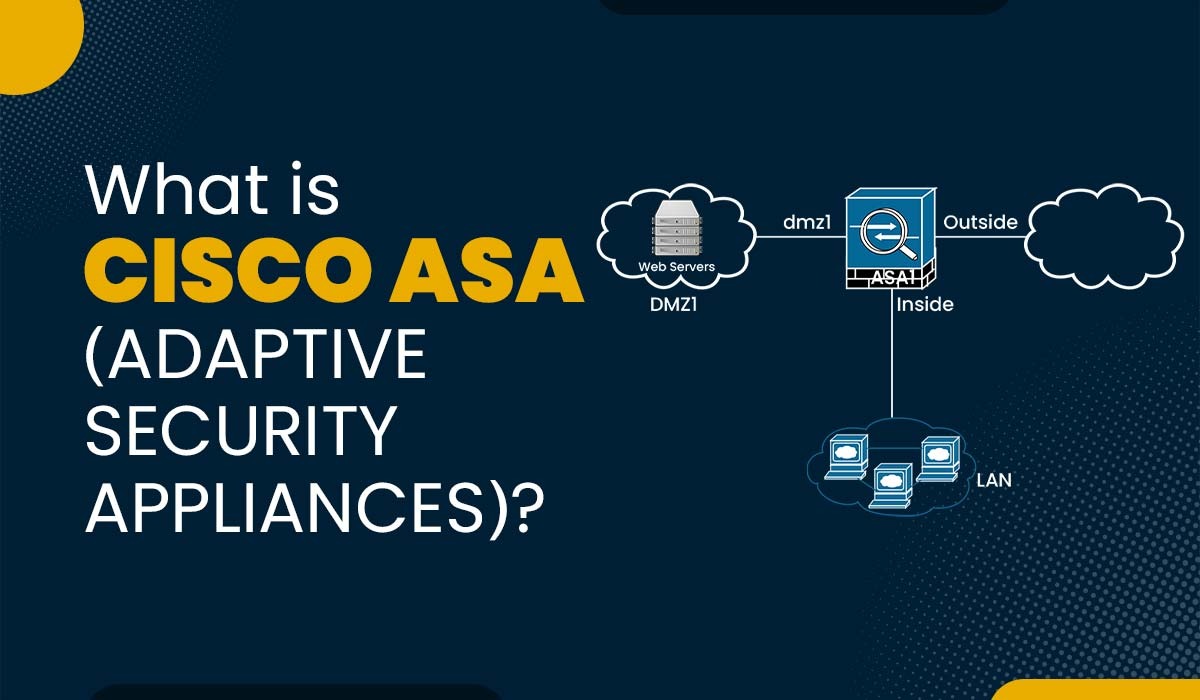
Nowadays, network security is more than crucial for any organization that completely relies on the Internet for its operations. Cyberattacks can lead to an impact on the integrity, confidentiality, and availability of data as well as network resources. Therefore, it is mandatory for all to have a robust network security solution that can protect the network from any unauthorized access. One of the most popular and widely used for the purpose of network security is the Cisco ASA (Adaptive Security Appliance). It is a part of Cisco’s advanced network firewall portfolio. This offers firewall and network security capabilities for any distributed network environment. Cisco ASA devices have been deployed in more than 1 million networks worldwide and, in return, provide secure access to data and network resources. In this blog, we will discuss Cisco ASA, its features, and how does it works. Let’s begin by first understanding the basic meaning of ASA. Cisco ASA, or Cisco Adaptive Security Appliances, is a network security product that is designed for the purpose of protecting networks of different sizes and types, from small businesses to large enterprises and from data centers to cloud environments. One can deploy Cisco ASA as a standalone appliance or a virtual appliance on a hypervisor. Apart from this, it combines a stateful firewall, VPN, intrusion prevention, antivirus, web filtering, and other security features in a single device or software. It supports multiple interfaces that can be assigned to different security zones or subnets. Each interface can have its own security level and access rules. It also supports VLANs to create sub-interfaces for further segmentation. Before getting into its functioning, let’s first understand the different Cisco ASA features. It provides many security features that can be either enabled or disabled by the network administrator, depending on the needs and preferences of the organizations. Below, we have discussed some of these features. Let’s now discuss its functioning in detail. Below, we have explained how Cisco ASA works in detail. Step 1: A packet arrives at one of the interfaces of the device. Step 2: The device checks if the packet belongs to an existing connection or a new connection. If it is an existing connection, it skips to step 6. If it is a new connection, it proceeds to step 3. Step 3: The device performs a prefiltering check to see if the packet matches any prefiltering rules that are configured on the device. Prefiltering rules are used to bypass or accelerate certain types of traffic without performing further inspection. If the packet matches a prefiltering rule, it skips to step 7. If not, it proceeds to step 4. Step 4: The device performs an access control check to see if the packet matches any access control rules that are configured on the device. Access control rules are used to allow or deny traffic based on various criteria, such as source, destination, protocol, port, application, etc. If the packet matches an access control rule, it proceeds to step 5. If not, it is dropped. Step 5: The device performs a security inspection check to see if the packet needs to undergo any additional security inspection, such as antivirus, intrusion prevention, VPN, content filtering, application control, etc. If the packet needs to undergo any security inspection, it is processed by the corresponding feature. If not, it proceeds to step 6. Step 6: The device updates the connection table with the information about the packet and the connection state. Step 7: The device performs a postfiltering check to see if the packet matches any postfiltering rules that are configured on the device. Postfiltering rules are used to modify or redirect certain types of traffic after performing inspection. If the packet matches a postfiltering rule, it is processed accordingly. If not, it proceeds to step 8. Step 8: The device forwards the packet to the appropriate interface based on the routing table. We have explained the working of ASA with these 8 steps. Cisco ASA assists in protecting your network from any unauthorized access and threats caused by cyber-attacks. A Cisco ASA is a firewall that can also perform some routing functions. Whereas when we talk about a router, it is a device that connects different networks and forwards packets. ASA stands for Adaptive Security Appliance. Cisco ASA 5000-X series is the next-generation firewall that offers advanced threat protection, application visibility and control, and integrated VPN features. Cisco ASA is a powerful and versatile firewall solution that can assist in providing network security for any organization. It’s devices can protect the network from various threats, control access to the network resources, and monitor the network activity. In this blog, we have explained what the Cisco adaptive security appliance is, its features, and its functioning.Introduction
What is Cisco ASA (Adaptive Security Appliances)?
Cisco ASA Features
How Does Cisco ASA Work?
Frequently Asked Questions
Q1. What does Cisco ASA do?
Q2. Is a Cisco ASA a router or firewall?
Q3. What does ASA stand for in Cisco?
Q4. Is Cisco ASA a next-generation firewall?
Conclusion







