What is IS-IS Protocol?
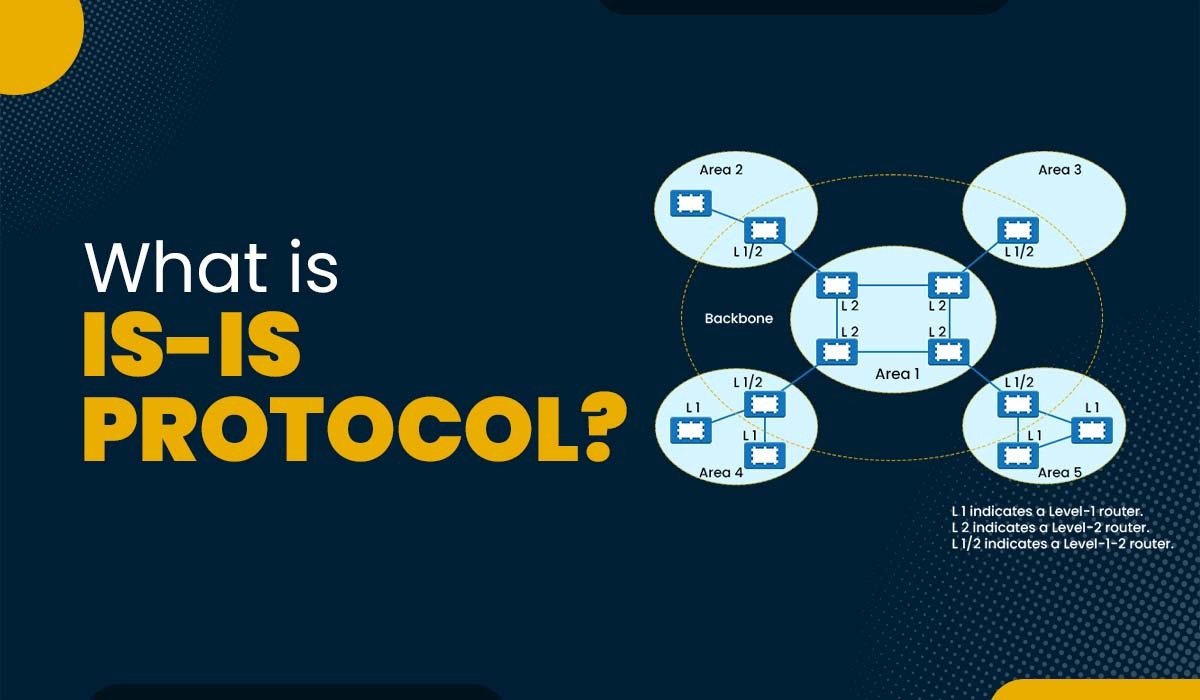
IS-IS is a link-state routing protocol that allows the efficient transmission of data in large and complex networks. Now, many network enthusiasts have heard of the term routing protocol, which is a set of rules and algorithms. Routing protocols are utilized by network devices to determine the best path for sending the data between the source and the destination. IS-IS is a widely used routing protocol due to its numerous advantages and features that make it suitable for different network scenarios. In this blog, we will explain what IS-IS protocol is, its history, its purpose, how it works, along with its different router types. Let’s first understand what ISIS protocol is. IS-IS protocol or Intermediate System to Intermediate System is a type of IGP (Interior Gateway Protocol), which simply means it can only be used for routing within a single administrative domain or network. One can not use it for routing between different ASes. For this role, EGP or Exterior Gateway Protocol such as BGP (Border Gateway Protocol) is used. The IS-IS operates by transmitting link state information throughout the network while ensuring reliability. Each IS-IS router independently constructs a database containing information about the network topology by aggregating the flooded network information. Similar to OSPF (Open Shortest Path First), which is also a type of link-state routing protocol, IS-IS uses Dijkstra’s algorithm to decide on choosing the best path through the network. Once the shortest path is chosen, packets are then transmitted to reach their intended destination along this path. IS-IS protocol operates at the network layer of the OSI model, and it rides directly on top of the data link layer, using its own header format. It does not use IP encapsulation like other routing protocols such as OSPF and EIGRP. IS-IS routers can have different roles depending on their location and function in the network. There are three types of routers, i.e., Level -1 router, Level -2 router, and Level -1-2 router. We will understand different types of routers in detail, but first, let’s look into the history of ISIS protocol. IS-IS is a link-state routing protocol that was originally developed by Digital Equipment Corporation (DEC) for their DECnet Phase V network architecture, which used a different network layer protocol called CLNS (Connectionless Network Service). IS-IS protocol is defined in ISO/IEC 10589:2002 as an international standard within the OSI (Open Systems Interconnection) reference model. The Internet Engineering Task Force (IETF) republished IS-IS in RFC 1142, but that RFC was later marked as historic by RFC 7142 because it republished a draft rather than a final version of the ISO standard. Later, IS-IS was adapted to support IP routing as well and became known as Integrated IS-IS (RFC 1195). Now we have a basic understanding of IS-IS protocol, let’s discuss its purpose. The main purpose of IS-IS protocol is to allow the routing of packets in an efficient as well as reliable manner. It can support both CLNS (Connectionless Network Service) and IP routing. Apart from this, it can also carry different types of information, which include MPLS labels, traffic engineering parameters, etc. ISIS protocol can also support multiple address families as well as instances within the same network. This allows a seamless integration of different routing protocols. Now if we talk about some of the advantages that make IS-IS protocol stand out from other protocols. These are: Below, we have explained how IS-IS protocol operates, i.e., its functioning. Below, we have explained the working of ISIS protocol. IS-IS protocol operates by establishing connections, also known as neighbor relationships, between routers through the use of hello packets. These packets are sent periodically on each interface to discover and maintain adjacencies with other routers available in the network. Apart from this, hello packets also carry information about the router’s level, area ID, priority, and various parameters. Once adjacencies are established, routers exchange Link State Packets (LSPs) to advertise their links and provide information about reachability. LSPs are reliably flooded throughout the network to ensure that every router receives the set of LSPs and builds a Link State Database (LSDB). Besides this, LSPs contain different types of information in the form of TLVs (Type Length Value), including network layer addresses, metrics, authentication details, and more. Upon receiving LSPs, routers utilize the SPF (Shortest Path First) algorithm, also known as the Dijkstra algorithm, in order to calculate the path to each destination based on link costs. These link costs can either be manually assigned or derived from interface bandwidth. The SPF algorithm generates a tree structure consisting of shortest paths, which is then used to populate the routing table. The routing table holds information about the route for each destination. It specifies the next hop router responsible for forwarding packets. Routers use the routing table to forward packets according to their destination address and network layer protocol. Let’s now discuss the different IS-IS Routers. ISIS protocol uses three types of routers to perform different roles in the network: This is an intra-area router, which only knows about the local area and the routes within it. It creates a level 1 link-state database and SPF tree for the area. It can only form neighbor adjacencies with other level 1 systems or level 1-2 systems in the same area. This is a backbone router, which knows about all the areas and the routes between them. It creates a level 2 link-state database and SPF tree for the backbone. It can only form neighbor adjacencies with other level 2 systems or level 1-2 systems in any area. This is a router that performs both roles. It creates a separate level 1 and 2 link-state database and two SPF trees, one for each database. It can form neighbor adjacencies with any type of router in any area. These are the IS-IS Protocol router types. The IS-IS protocol is one of the widely used protocols that is mainly used to transmit data efficiently in a network. It is a link-state protocol that uses Dijkstra’s algorithm in order to find the best path to each destination. The main difference between the OSPF and IS-IS is that in the case of OSPF, it has a hierarchical structure with a backbone area (area 0) and all the other areas connected to it. On the other hand, ISIS has a flat structure with level 1, level 2, and level 1 2 routers. IS-IS is a layer 2 protocol because it has its own protocol stack, i.e., CLNS, and does not use IP in order to route the information. The full form of IS-IS in Cisco is Intermediate System-to-Intermediate System. In this blog, we have explained the IS-IS Protocol or intermediate system to intermediate system protocol, its purpose, its operation, and different router types. We have seen that ISIS is a powerful routing protocol that can be used to handle large networks efficiently. We hope that this blog has helped you to understand the basics of IS-IS and its benefits for network routing. If you want to learn IS-IS Protocol in-depth, you should join our online CCNA Course. Still, feel free to use the comment section below for any suggestions or doubts.Introduction
What is IS-IS Protocol?
History of IS-IS Protocol
Purpose of IS-IS Protocol
How Does IS-IS Protocol Work?
IS-IS Router Types
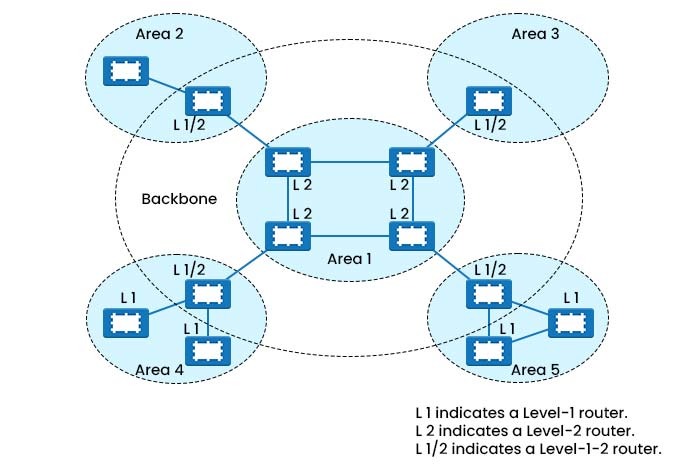
Level 1 Router
Level 2 Router
Level 1-2 Router
Frequently Asked Questions
Q1. What is-IS-IS protocol in networking?
Q2. What is difference between OSPF and IS-IS?
Q3. Why is IS-IS a Layer 2 protocol?
Q4. What is the full form of IS-IS in Cisco?
Conclusion







