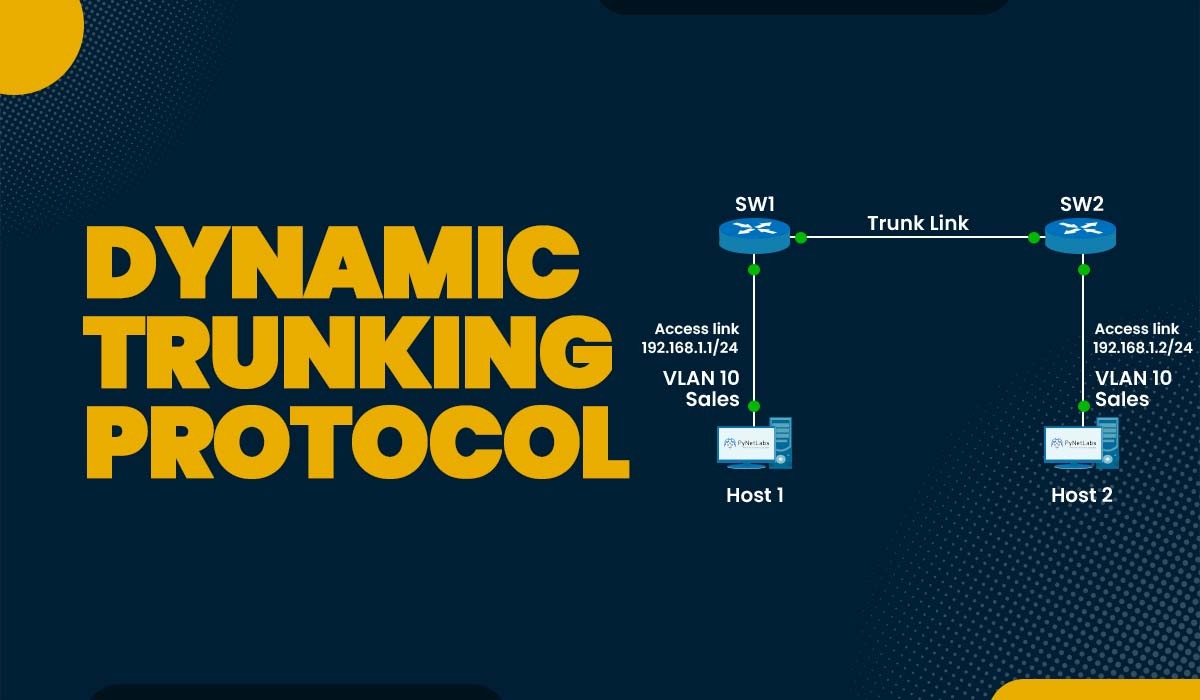
Introduction The word trunking may be familiar to network engineers or students studying networking. Multiple VLANs (virtual LANs) may share the same physical connection between switches using the practice known as trunking. With this method, you may separate various traffic types for security and performance reasons while conserving ports, cables, and bandwidth. But how do […]
Read More
Introduction Nowadays, everyone relies heavily on digital platforms, whether for business purposes or some important transactions. With the increase in digital presence, protecting personal data from hackers is crucial. VPN in cyber security is one approach to stop third parties from obtaining vital data for their benefit. In this blog, we will discuss what a […]
Read More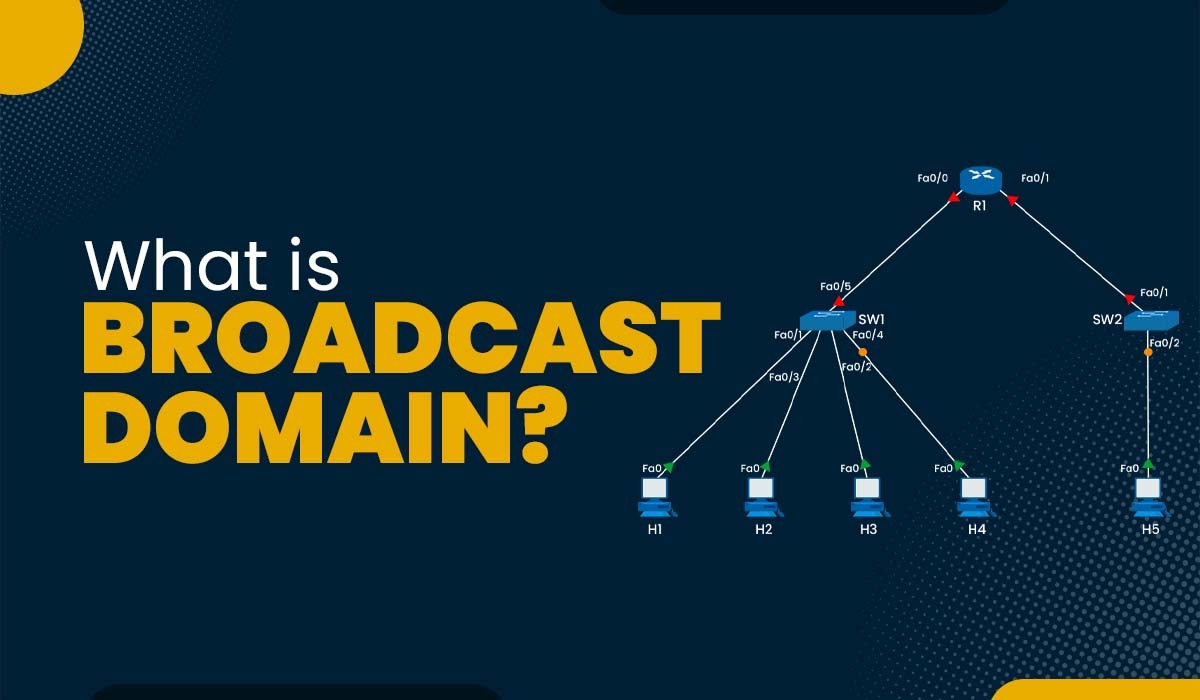
Introduction The study of networking covers a wide range of topics and technologies. A logical subdivision of a computer network where all nodes may interact with one another by sending and receiving broadcast messages is known as the broadcast domain. Regardless of their destination address, broadcast messages are unique data packet types distributed to all […]
Read More
Introduction Networking is now crucial to the success of almost every business in the modern digital environment. The importance of understanding how VLAN and Subnet function has grown as networks have expanded in both complexity and size. In this blog, we will explain the basic difference, i.e., VLAN vs Subnet, that will assist in understanding […]
Read More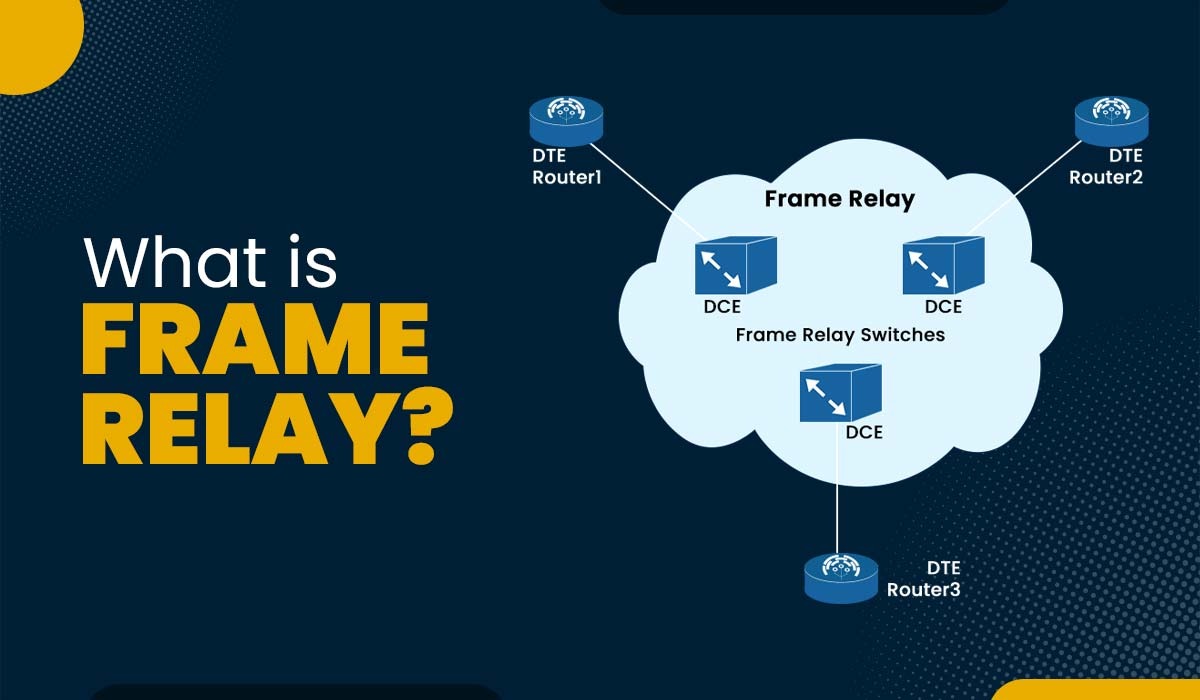
Introduction In computer networks, data communication is crucial for many applications as well as services. Data communication is the data transmission process over a network between multiple devices. It is important to note that various devices support different data formats, transmission speeds, and protocols. Hence, there is a need for a common network technology that […]
Read More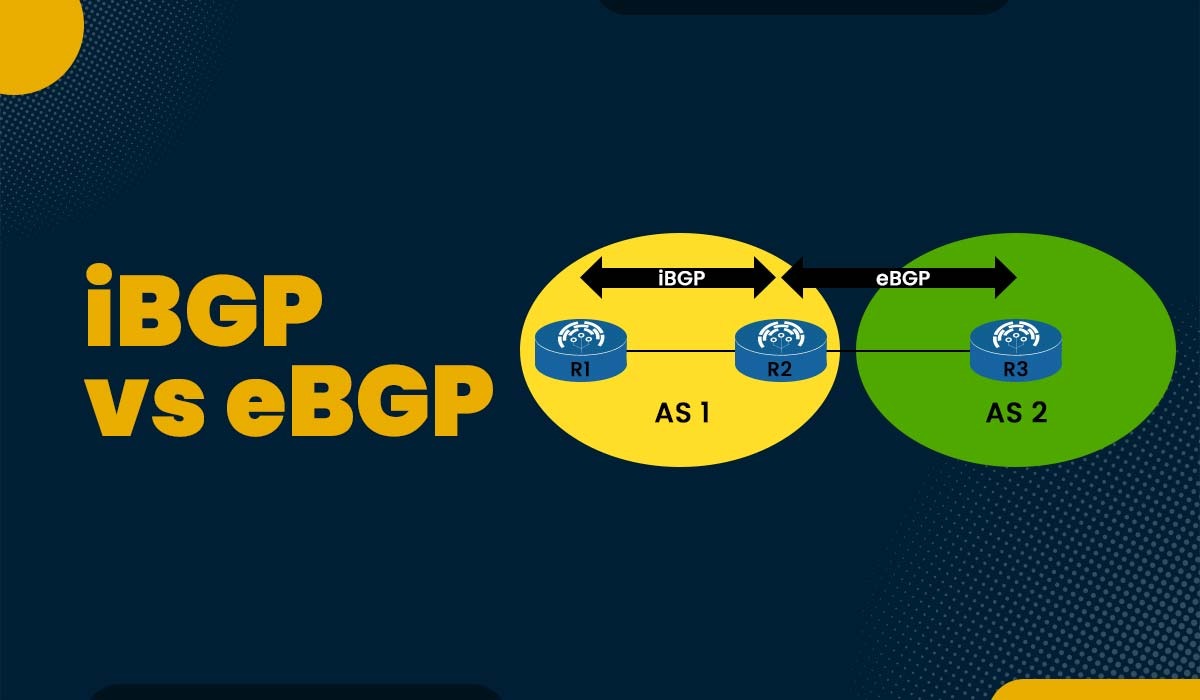
Introduction One of the foundations of modern networking is the border gateway protocol or BGP. Without BGP working in the background to allow system communication, the modern internet as it is known today would not be able to operate. The routing protocol known as BGP has two different versions, i.e., eBGP and iBGP. Both provide […]
Read More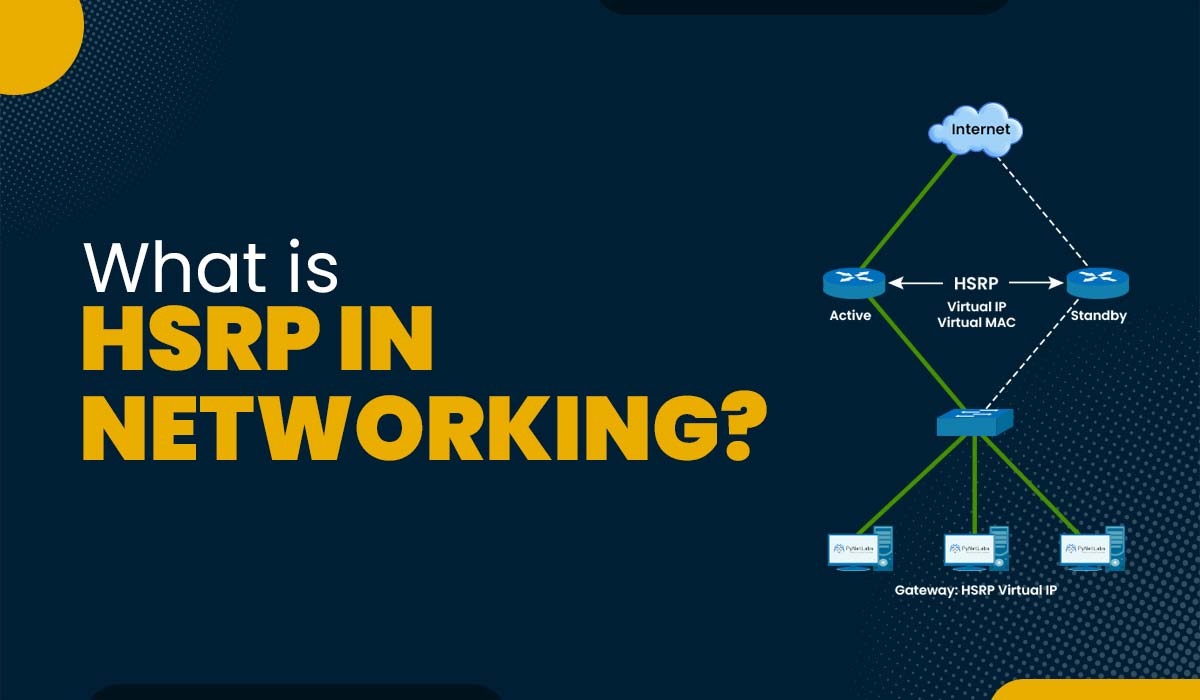
Introduction Redundancy is a crucial component of every modern network. In this digital era, staying without a network for even a short time is hard. You should include some redundancy if you don’t want your firm to cease operating. All of your devices will stop communicating with the outside world if the default gateway fails […]
Read More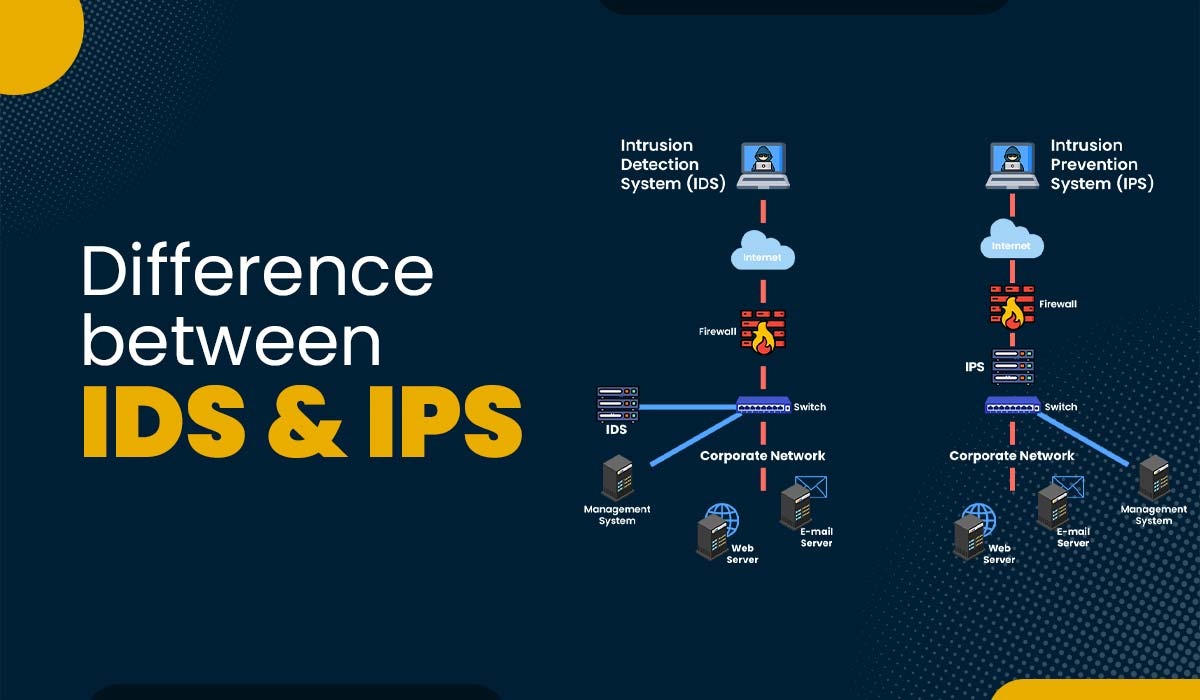
Introduction Nowadays, attackers’ knowledge and sophistication level is increasing steadily, making a single defensive method against intruders insufficient in providing substantial security. Instead, organizations should prioritize implementing a comprehensive and multi-layered strategy that combines proactive and defensive measures to safeguard their network and assets from unauthorized individuals. That’s where IDS, IPS, and firewalls come into […]
Read More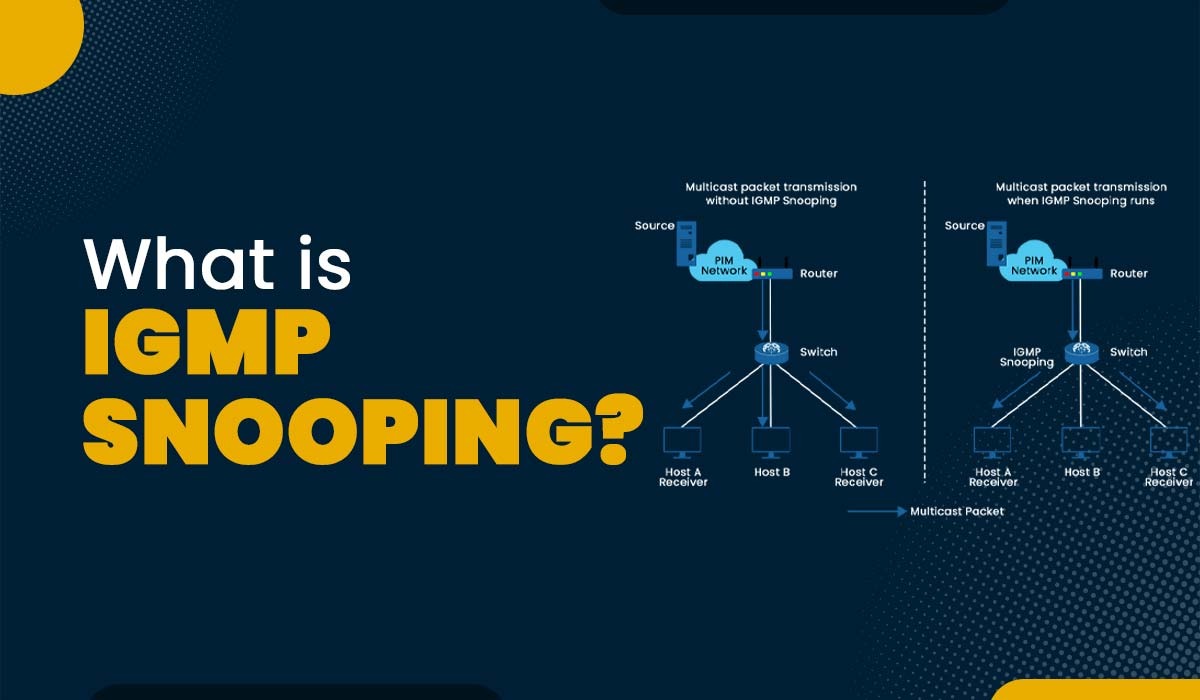
Introduction Today’s data transmission demands can’t be met by the inefficient and resource-intensive unicast method used by most networks. Internet Group Management Protocol (IGMP) Snooping was developed as a solution and is now often implemented in network multicast mode. In this blog, we will explain IGMP snooping, its working, functions, and applications. Let’s begin with […]
Read More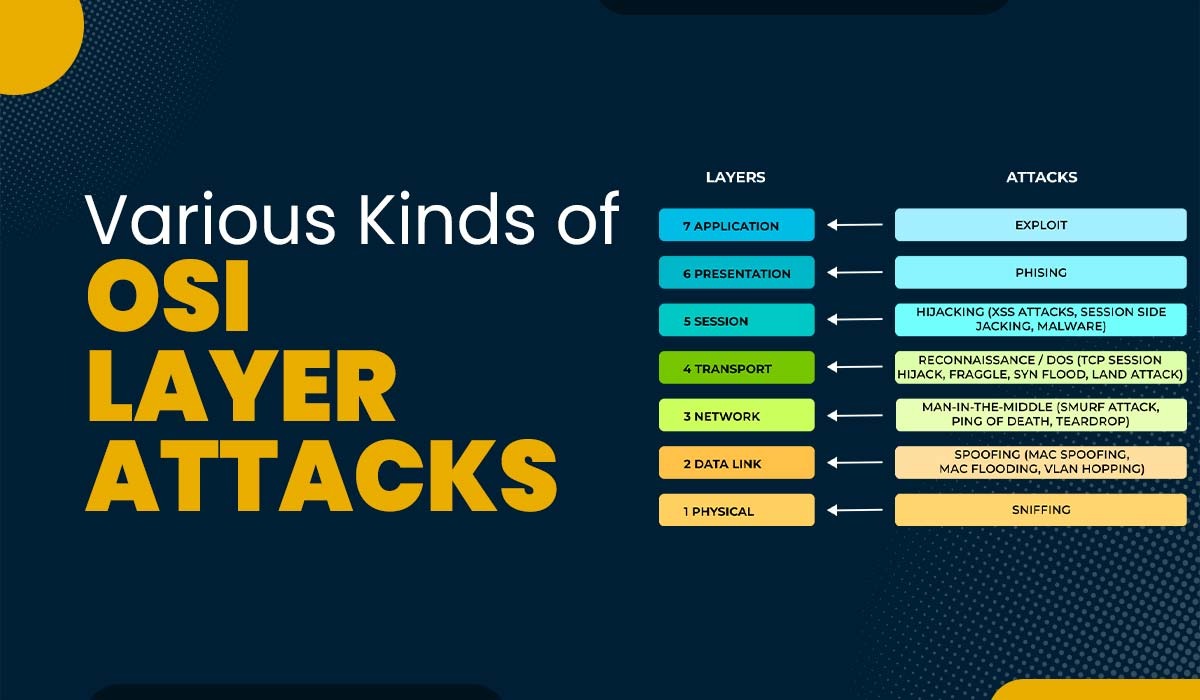
Introduction Cybersecurity is a dynamic field since hackers are always developing new methods of breaking into networks and stealing private data. Understanding the many forms of OSI layer attacks and strategies of cyberattacks is vital for establishing a successful defense against them. It is essential to understand the different kinds of cyberattacks at each layer […]
Read More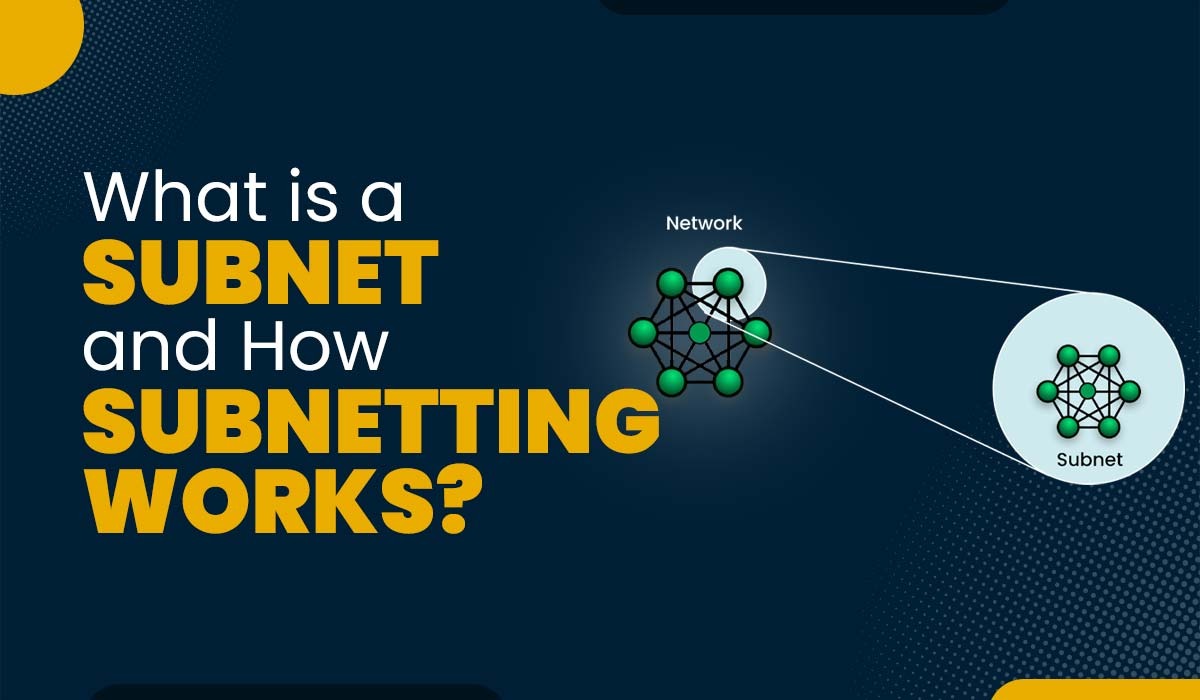
Introduction The management of a network on a major scale is not easy. As networks continue to grow in size and complexity, network engineers are faced with the challenge of determining optimal routes for handling the substantial volume of traffic flowing through them. Subnetting is one of the solutions developed, but the question is, what […]
Read More
Introduction Generic Routing Encapsulation, or GRE, is a tunneling system that allows various network layer protocols to be encapsulated within IP tunnels. Using either public or private networks, GRE may establish point-to-point logical links between network devices. In this blog, we will explain the GRE protocol with its working, benefits, drawbacks, and configuration. What is […]
Read More










