Various kinds of OSI Layer Attacks
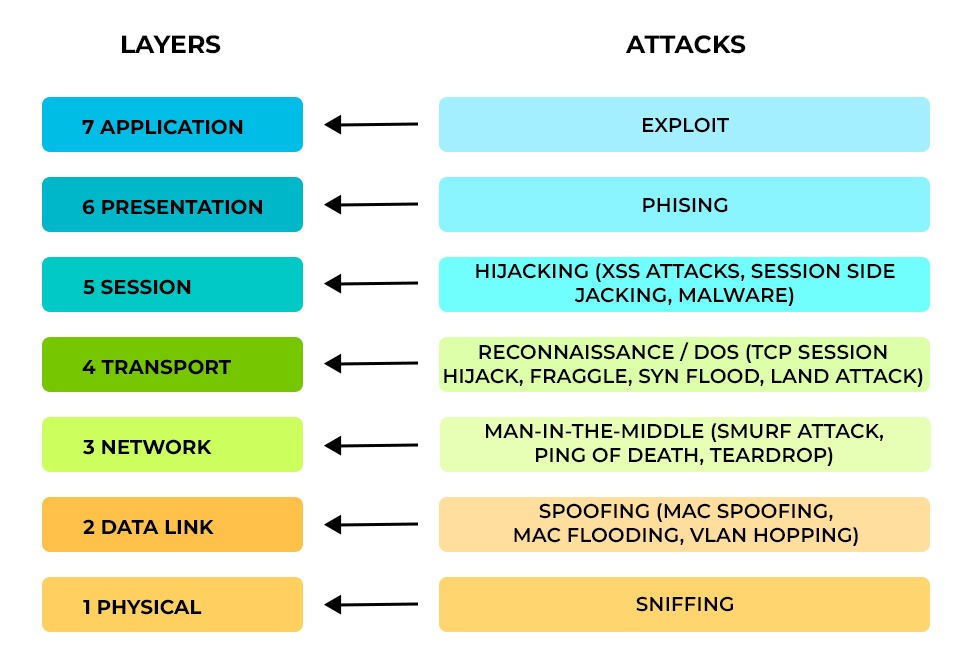
Cybersecurity is a dynamic field since hackers are always developing new methods of breaking into networks and stealing private data. Understanding the many forms of OSI layer attacks and strategies of cyberattacks is vital for establishing a successful defense against them. It is essential to understand the different kinds of cyberattacks at each layer to put appropriate security measures in place. In this blog, we will focus on the different types of attacks on OSI layers and how they affect each layer. Before getting into the different types of attacks on OSI layers, knowing about the OSI model is crucial. Let’s Begin! The OSI model specifies seven abstraction levels that computers may use when communicating with one another via a network. There are different functions for each layer in the OSI model, and those functions include interaction and communication with the layers above and below them. Late in the 1970s, the OSI reference model was developed. Unfortunately, it now just serves as a reference model. The TCP/IP (Internet Protocol Suite) framework is now in use on the Internet. Here are the differences between OSI and TCP/IP Model. Now, let’s focus on the different types of OSI layer attacks in detail. It is possible that hackers can penetrate each layer of the OSI model as each layer has its vulnerability. There are various reasons, such as software bugs, design flaws, and misconfigurations, that act as a weakness and give the attacker an upper hand to easily penetrate through all 7 layers. Let’s discuss different types of attacks on OSI layers and their effects. The application layer, or “desktop layer,” allows interactions between the host and client applications. A user’s experience begins at this layer. Access to data and application services through a network is made possible. Additionally, it details the common interface techniques and communications protocols used by hosts across networks. Layer 7 in the OSI reference model is responsible for interaction and communication with the presentation layer. The most common security attack on this OSI layer is an exploit. An exploit is a process of taking advantage of other systems to your benefit via vulnerabilities. The vulnerability may result from improper system setup or a bug in a particular version of software running on the victim machine. Numerous vulnerabilities are made to provide super user access to a target system or to launch DoS (denial of service) or DDoS (distributed denial of service) attacks, which allow attackers to take down a website or important system without ever needing an exploit. Examples of exploits include SQL injections, cross-site scripting, and parameter tampering. These OSI Layer attacks can result in data theft, identity fraud, or system damage. The presentation layer or “syntax layer” is responsible for formatting as well as translating data into the specific format as directed by the application layer. The network’s data translator ensures that the data transmitted by the application layer is formatted in a way that can be understood by the receiving system’s application layer. The OSI model layer takes part in communication and interaction with the application layer and the session layer. The most common security attack on this OSI layer is phishing. Phishing attacks include delivering false messages that seem to be from a reliable source. Email is often used for this. The intention is to steal personal information like credit card numbers and login credentials or to infect the victim’s computer with malware. Everyone should educate themselves about phishing, a prevalent kind of cyber-attack, in order to defend themselves. Examples of phishing include fake websites, email messages, or pop-ups that appear to be from a legitimate source. Opening, maintaining, and ending sessions between end-user application processes are the responsibilities of the session layer. The connections between remote and local apps are established, managed, and terminated by the session layer. This host layer establishes the configuration, manages the connection, makes checkpoints, and restores sessions in case of failure. This layer interacts and communicates with the presentation layer and the transport layer. The most common security attack on this OSI layer is hijacking. Hijacking attacks involve the interception and subsequent control of an established communication session. The primary objectives of such attacks are to gain unauthorized access to the targeted user’s computer or account or to obtain sensitive data. Mainly, there are two types of hijacking: active and passive hijacking. Examples of hijacking include session fixation, session replay, and session sidejacking. Data transmission between end systems must be dependable and effective, and this is the job of the transport layer. It interacts with the network layer and segments, sequences, acknowledges, and retransmits data packets using protocols like TCP and UDP. It also manages congestion and flow management. It supports reliable data transfer between network nodes in two distinct modes: connection-oriented and connectionless. It mainly interacts and communicates with the network layer and the session layer. The most common security attack on this OSI layer is reconnaissance or DoS (Denial-of-Service). Reconnaissance is the process of learning as much as possible about a target system so that its weaknesses may be exploited. Originally developed as a method for improving security, malicious actors now routinely use vulnerability assessments to locate weak spots in a network before initiating an attack. DoS attacks, also known as “Denial-of-service attacks,” involve flooding the target with unnecessary requests to prevent valid requests from being processed, hence rendering the resource inaccessible to users. The disturbance may be momentary or ongoing. The term “distributed denial-of-service attack,” or “DDoS attack,” refers to an attack that comes from several sources simultaneously. Examples of reconnaissance or DoS attacks include port scanning, SYN flooding, TCP reset, UDP flooding, and ICMP flooding. The network layer is in charge of offering methods for packet transfers between linked nodes via one or more networks. Using routers and switches to control its traffic, it constructs and administers multi-node networks. The transport layer and the data connection layer are the two layers with which this OSI model layer interacts and communicates. The most common security attack on this OSI layer is man-in-the-middle. MitM attacks, or “man-in-the-middle” attacks, include third-party intercepting, re-transmitting, or modifying communications between two parties. While each side is convinced, they are safely and directly exchanging information. Examples of man-in-the-middle include email hijacking and Wi-Fi eavesdropping. Transferring data frames between two directly linked nodes within the same LAN falls within the responsibility of the data link layer. It creates frames out of the raw data from the physical layer. Additional functions include error detection and rectification. This layer of the OSI model interacts with and communicates with the network and physical layers below it. The most common security attack on this OSI layer is spoofing. Spoofing attacks involve deliberately manipulating data by an individual or software application to pretend to be an authorized user or device. Attackers have the ability to bypass access control to systems, steal data, and spread malware by claiming to be authorized users or devices. Spoofing can be done in many ways; some of these are ARP spoofing, DHCP spoofing, and MAC flooding. The physical layer deals with transmitting and receiving unstructured raw data between devices and physical transmission media. The implementation can be achieved using various hardware technologies. The communication and interaction of this OSI model layer occur with the data link layer. The function of this system is to convert logical communications requests originating from the data link layer into hardware-specific operations. This conversion enables the system to transmit and receive signals effectively. The most common security attack on this OSI layer is sniffing. A sniffing attack aims to steal information by monitoring network traffic using special software, also known as sniffer applications. The packet sniffer may then read the packets if they are not encrypted. This provides an opportunity for attackers to gain insight into the network and learn enough to compromise it or perhaps bring it down. These are the most common OSI Layer Attacks. Layer 2 is the data link layer, and the attacks associated with it are spoofing, Mac flooding, and ARP attacks. Layer 3 is the network layer, and the attacks associated with it are man-in-the-middle. Layer 5 is the session layer in the OSI reference model, and the attack associated with it is hijacking. A layer 1 attack is a type of cyberattack that targets the physical layer of the OSI model, which is responsible for transmitting data over a medium. The attack associated with the layer 1 attack is sniffing. Each OSI model layer has its own protocol and functions and is susceptible to different cyberattacks. For example, the data link layer is susceptible to MAC spoofing, ARP poisoning, and denial-of-service attacks, while the physical layer is susceptible to sniffing and eavesdropping. Today’s ordinary IT risks cannot be ignored. As a consequence, enterprises are increasingly using tight security strategies against OSI layer attacks to guarantee business continuity. In this blog, we have covered all seven layers and attacks with their impact.Introduction
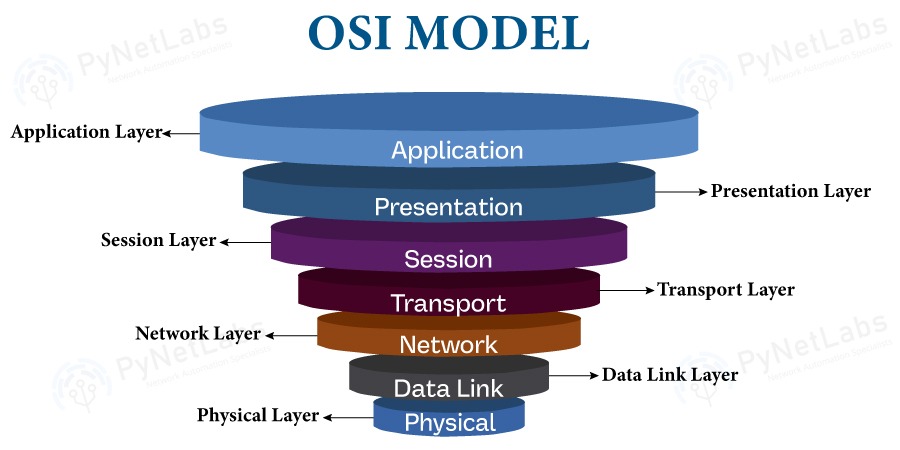
What is an OSI model?
Types of OSI Layer Attacks
Application Layer
Application Layer Attack
Presentation Layer
Presentation Layer Attack
Session Layer
Session Layer Attack
Transport Layer
Transport Layer Attack
Network Layer
Network Layer Attack
Data Link Layer
Data Link Layer Attack
Physical Layer
Physical Layer Attack
Frequently Asked Questions
Q1 – What are the layer 2 and layer 3 attacks?
Q2 – What is a Layer 5 attack?
Q3 – What is a layer 1 attack?
Q4 – In what layer of the OSI model are vulnerabilities found?
Conclusion







