
Introduction With the increasing number of organizations shifting to the digital world, the importance of protecting data from hacking and cyber-attacks has become more critical than ever. Many companies are now recognizing the potential risks associated with these attacks and considering proactive measures, such as ethical hacking. But how can ethical hacking help in saving […]
Read More
Introduction In the networking field, various network devices are utilized for different purposes. Hubs, switches, routers, and other network devices are utilized to perform different tasks within a network infrastructure. In order to analyze the functionality and effectiveness of network devices, various metrics, defined as standards or systems of measurement, are used. The Collision domain […]
Read More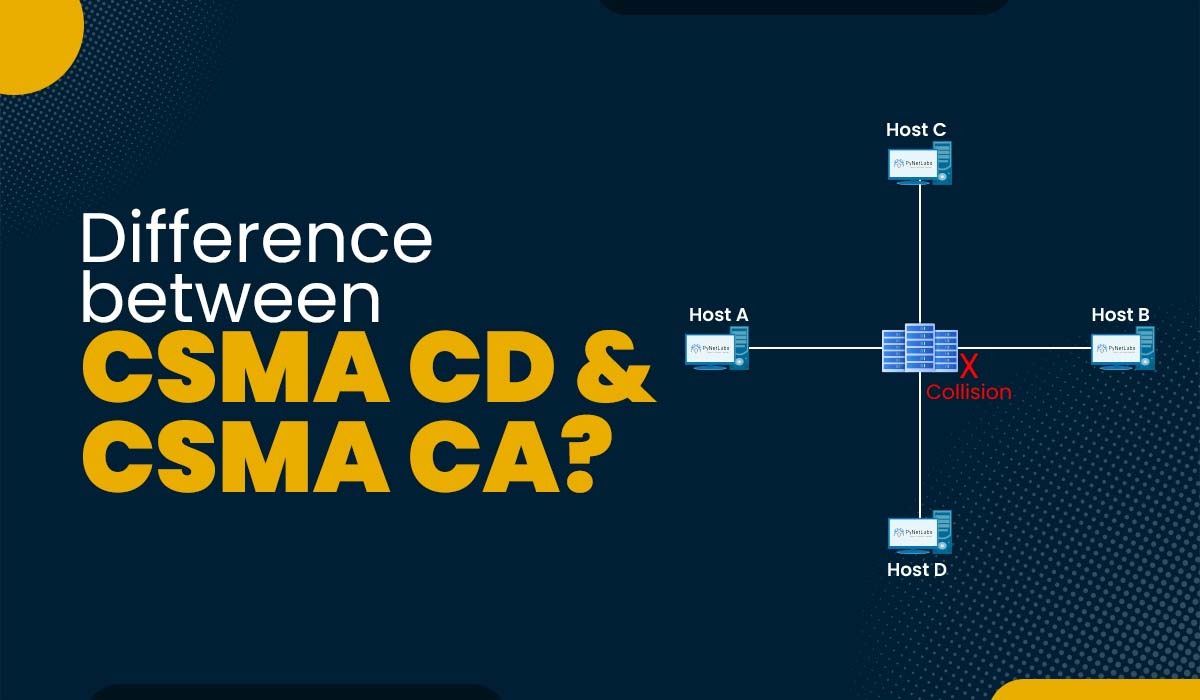
Introduction The ability of multiple network computers to transmit data to each other without experiencing significant packet collisions is truly remarkable. One could expect various issues due to the vast number of data packets transmitted across a typical network. However, it is important to note that the majority of modern computer networks display a high […]
Read More
Introduction Nowadays, most organizations rely heavily on the Internet for daily business; as a result, there has been a surge in cyberattacks. As cybercrime becomes more common, businesses find it difficult to protect sensitive data without compromising productivity. That’s why IPsec is widely used by businesses to allow secure transmission and access of data. But […]
Read More
Introduction VRRP stands for Virtual Router Redundancy Protocol, and it is a protocol that provides high availability and fault tolerance for routers in a network. It allows multiple routers to form a virtual router group and share a virtual IP address, which is used as the default gateway for the hosts in the network. In […]
Read More
Introduction The software industry now relies heavily on automated processes. Ansible streamlines the process of automating and managing configurations for both development and production settings. If you’re preparing for an interview based on the tool, you’ll want to give yourself enough time to prepare. We have added a list of frequently asked ansible interview questions […]
Read More
Introduction One of the fundamental concepts in computer networking is transmission, which is the process of sending data from one device to another over a network. Transmission can be classified into different types based on how the data is addressed and delivered to the intended recipients. The main difference between broadcast and multicast is that […]
Read More
Introduction New technologies and the increasing number of hosted services have transformed network and application infrastructures. As a result of these changes, consumers now have access to a wider set of alternatives than ever before. But they have also made us far more dependent on a reliable network to keep these critical programs running smoothly. […]
Read More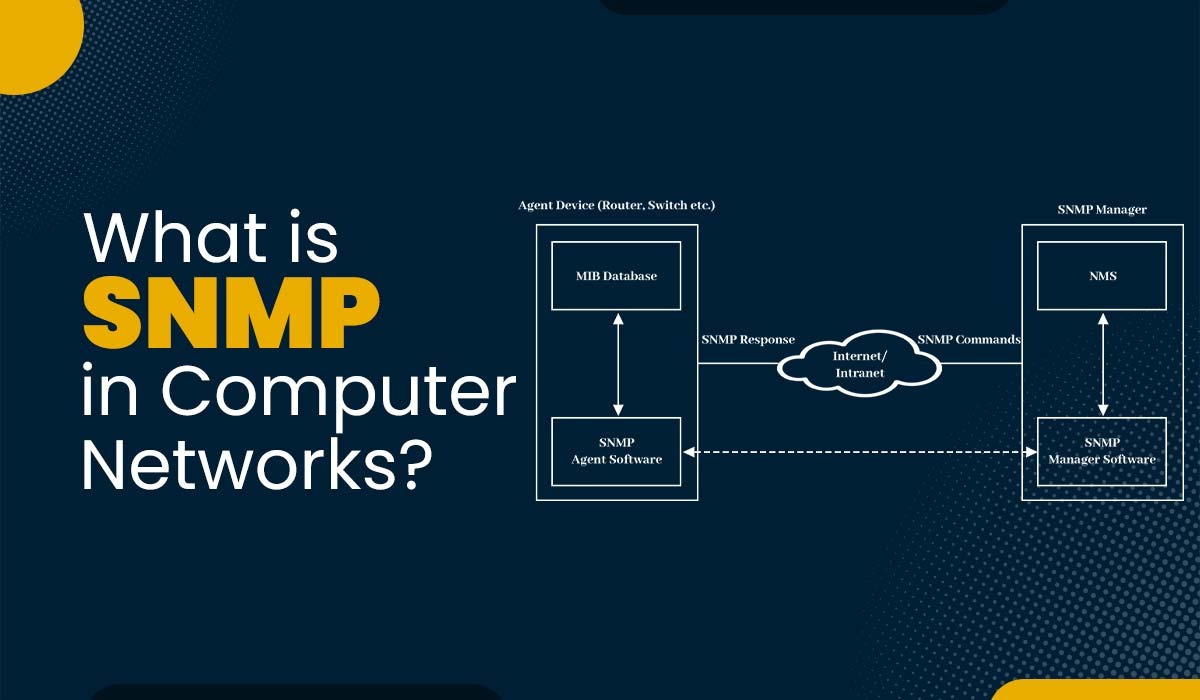
Introduction Over the last decade, the development of wireless networking has accelerated the rapid expansion of computer networks. Meanwhile, network management challenges, such as managing complex networks of routers, servers, or switches, have become much more complex as a result of this expansion. This is where SNMP comes into action. SNMP in computer networks was […]
Read More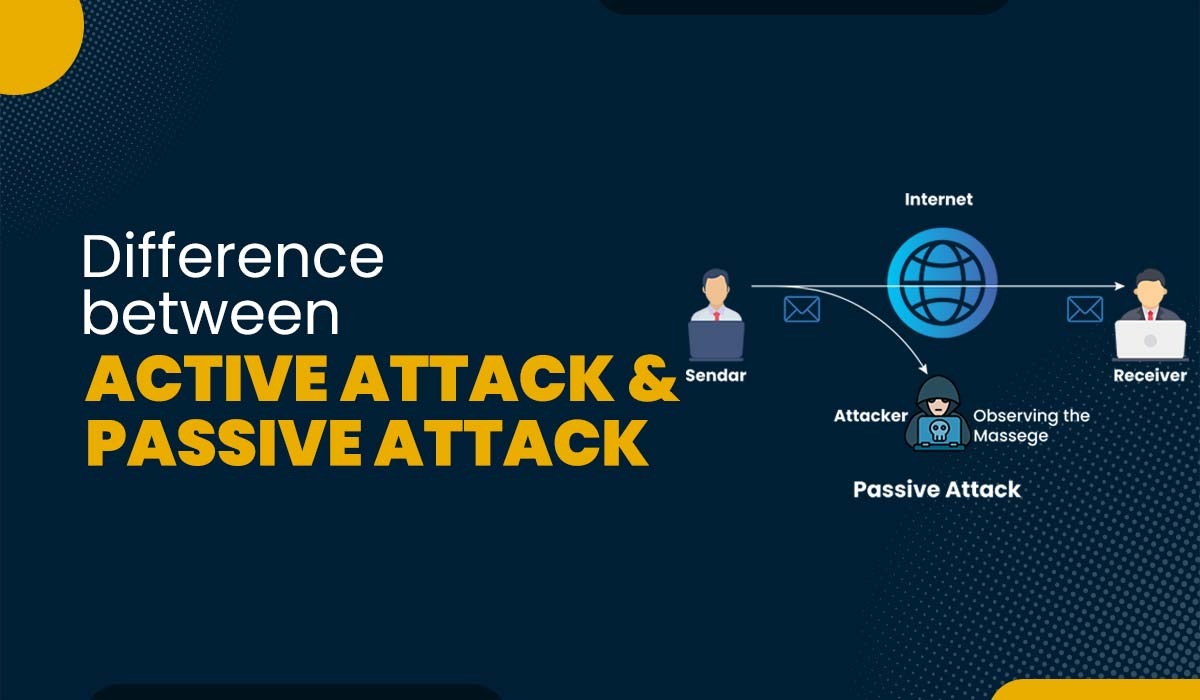
Introduction Clearly, the Internet is one of the most significant innovations of our time. It has simplified our life in more ways than we can even count. This development has similarly exposed us to a wide variety of cyberattacks. Cybersecurity attacks pose a greater threat to all that is part of the Internet. Cybersecurity threats […]
Read More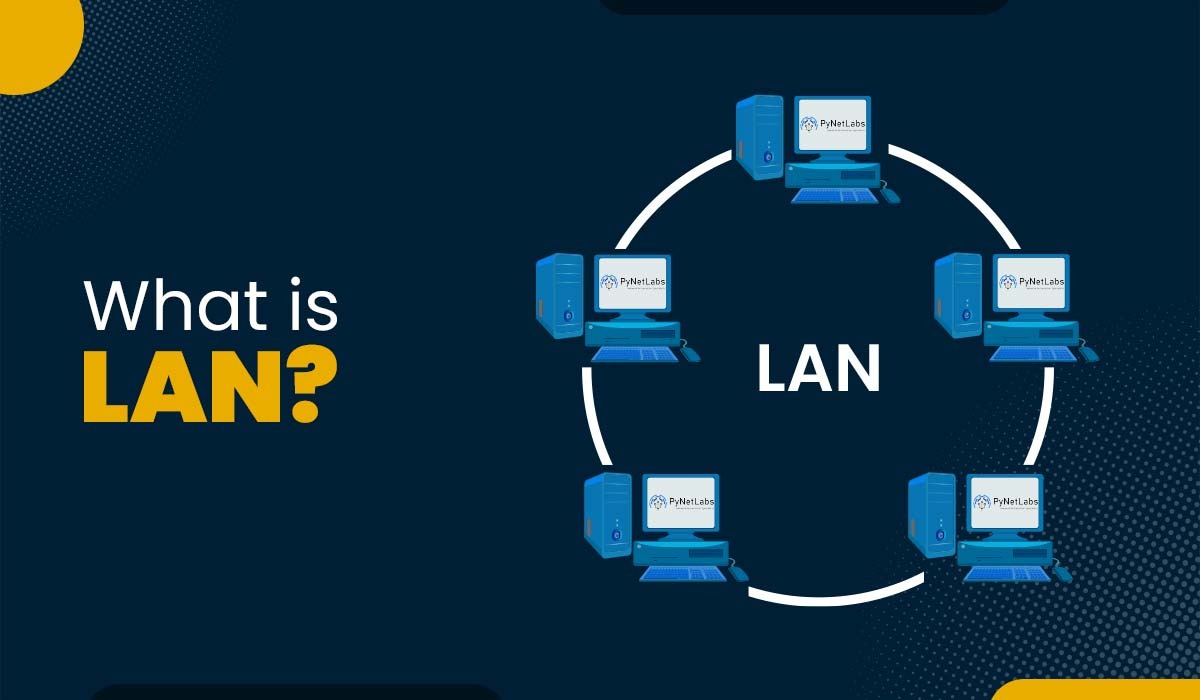
Introduction A computer network is a digital network that provides a central connection point for several computers and other computing devices. There are different types of computer networks, each of which may be classified according to the scale of their operations and purpose. One of the most common types of computer networks is LAN. But […]
Read More
Introduction TCP/IP stands for Transmission Control Protocol/Internet Protocol, which is a set of rules that governs how data is transmitted and received over a network. It is one of the most widely used protocols that allows communication between different devices across various networks. Jobs in this field often need a thorough understanding of TCP/IP. In […]
Read More










