What is SSH (Secure Shell) in Networking?
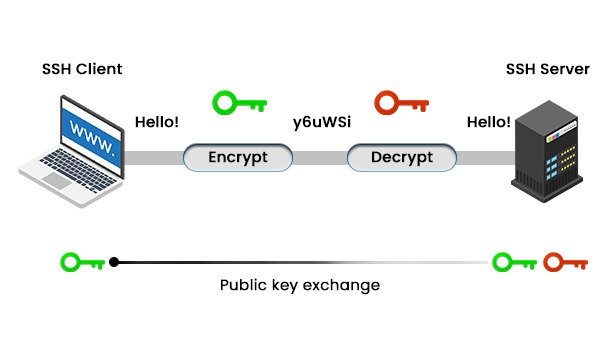
If you want to control a server or machine that is physically inaccessible, you need to communicate with it remotely. However, not all remote strategies are stable and secure. For example, older protocols like Telnet or rlogin ship your commands and passwords in simple text, which can effortlessly be intercepted by means of hackers or malicious people. SSH in networking is designed to overcome this issue by providing a secure channel between your device and a remote server. Secure Shell makes use of public-key cryptography to encrypt your data, which ensures that the recipient can only decrypt it. In this blog, we will explain what SSH is, its purpose, its history, and how it works. Let’s start by explaining what SSH is. SSH or Secure Shell is a network protocol, and its main function is to provide a secure shell or command-line interface for remote communication. SSH in networking is mainly based on a client-server architecture where an SSH client connects to an SSH server using a TCP/IP connection. Generally, it is widely used to manage servers, transfer files, and perform other network-related tasks. There are three main components of SSH, these are: A better substitute for insecure protocols like Telnet or rlogin, Taty Ylonen developed SSH in the year 1995. It was highly accepted by network professionals and adopted with open hands. The original version was called SSH, which is now known as SSH-1. Still, SSH-1 has many limitations, which include unstable and poor encryption techniques, and there is also a lack of platform compatibility. Soon after, IETF (Internet Engineering Task Force) came up with a new version of SSH, also known as SSH-2, which became the standard in the year 2006. When we talk about SSH-2, it’s better than the SSH-1 in many ways. Some of these are: One of the most used versions of SSH is OpenSSH. It is an open-source project, and it is based on Ylönen’s original code. It is maintained by the OpenBSD developers. It supports both SSH-1 and SSH-2 protocols and is available for various operating systems. We have explained What is SSH in networking and also the history of its origin. Now, let’s understand how SSH works. SSH works by setting up a connection between an SSH client and an SSH server through the use of public-key cryptography. Public-key cryptography includes a variety of keys: public keys and private keys. A public key can be shared with everybody, whilst a private key must be kept secret. The keys are mathematically related but no longer the same. Data encrypted with one key can only be decrypted with the opposite key. The simple steps of an SSH connection are: Here we will learn what SSH is used for: So, there are three parameters of SSH security: The SSH protocol consists of thrее layеrs, these are: Transport Layеr The transport layer plays a crucial role in establishing a secure connection between client and server. It also encrypts the data, and side-by-side, verifies the integrity of the connection. Data caching and compression are some of the steps taken by this layer to improve performance. Authentication Layer When we talk about the authentication layer, it is simply responsible for the client authentication process. In order to authenticate, it supports various authentication methods like GSSAPI (Generic Security Services Application Program Interface) and many others. Connection Layer The Connection layer is the layer that is responsible for managing communication channels once the authentication is completed. Now, what is channel? A channel is a logical data stream that can be multiplexed over a secure connection. SSH supports various channels such as session channels, dirеct-tcpip channеls (for local port forwarding), or forwardеd-tcpip channеls (for rеmotе port forwarding). SSH uses three distinct encryption techniques to make secure communication at many points at the time of communication. These techniques are: Let’s discuss each one in detail. In symmetric encryption techniques, only one key is used to encrypt and decrypt messages sent and received from the destination. Since the same key is used by both devices to encrypt the shared data and decrypt the received data, this technique is called shared key encryption. With this technique, the entire SSH connection is encrypted which helps prevent man-in-the-middle attacks. One issue that arises when exchanging the first key is that if the party is present at the time of the key exchange, they may have the key and can read the entire message. To prevent this problem, key exchange algorithms are used that help to exchange the secret key securely without blocking it. Asymmetric encryption is required to execute the key exchange algorithm. In asymmetric encryption, two different keys are used for encryption and decryption, such as private and public keys: It is a secure technique because if a third party has the public key to encrypt the message, but they cannot decrypt the message without the private key. Asymmetric encryption is used for the key exchange algorithm of symmetric encryption, but it does not encrypt the entire SSH session. In this, both systems (client and server) temporarily create public-private key pairs and then share their private keys to create a shared secret key before establishing a connection. After establishing a secure symmetric connection, the server uses the public key to share it with the client for authentication. The private key allows the client to decrypt the data, thus securing the SSH session. Another form of cryptography in SSH is one-way hashing which serves as an encryption technique. This does not mean decryption which is why it is different from the above two methods. This creates a signature of the information. The use of HMAC (Hash-based Message Authentication) by SSH ensures that messages are received in their entirety without any modification. In hash technology, each shared message must have a MAC which uses three components such as symmetric key, packet sequence number, and message content. The hash function includes all three components that create a string without any meaning and this string is shared with the host. If the details are the same then the host also creates a hash function and when the hash created matches the received hash, it means the message has not been tampered with. These are the three Secure Shell Encryption Techniques. SSH or Secure Shell is a kind of protocol that makes it possible for anyone who wants to communicate and transfer data over a network that is not secure. It uses public-key cryptography in order to authenticate as well as protect the connection. SSH default port is 22. SSH stands for Secure Shell, which is a secure and encrypted protocol. Whereas, when we talk about TCP or Transmission Control Protocol, it is a connection-oriented protocol. Examples of SSH are: SSH is commonly used for remote login and command-linе еxеcution. SSH or Secure Shell is one of the most powerful network protocols that allows secure access to devices remotely over a network that is not secure. It makes use of public-key cryptography in order to authenticate and encrypt connections between devices. In this blog, we have explained what is SSH in networking, its purpose, and how it works for better understanding.Introduction
What is SSH in Networking?
History of Secure Shell
How does Secure Shell Works?
What is Secure Shell used for?
Architecture of SSH in Networking
Secure Shell Encryption Techniques
Symmetrical Encryption
Asymmetrical Encryption
Hashing
Frequently Asked Questions
Q1. What is SSH and its port?
Q2. What is SSH vs TCP?
Q3. What are examples of SSH?
Q4. Why is SSH used?
Conclusion







