Difference between Symmetric and Asymmetric Key Cryptography

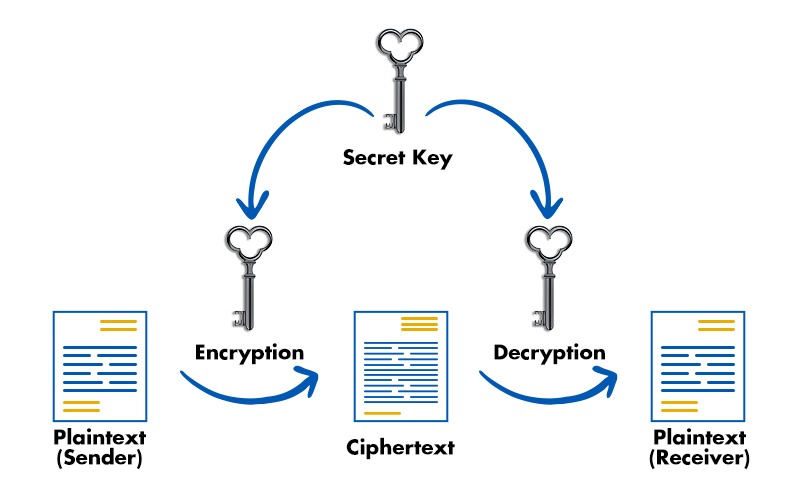
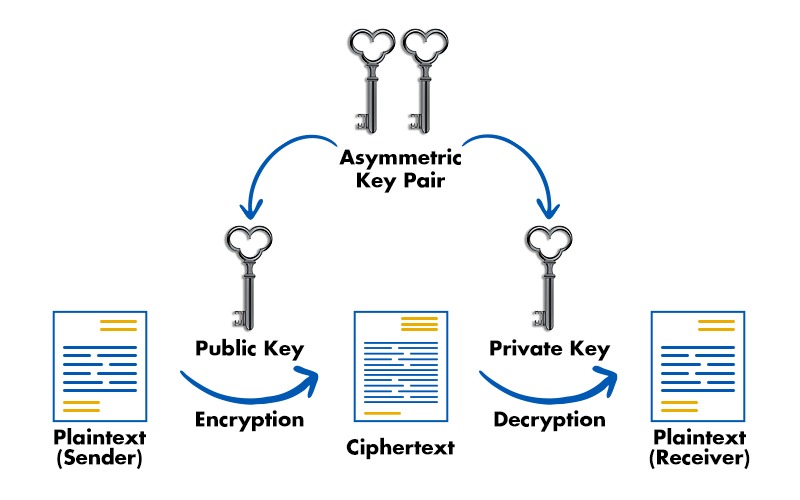
Scammers and other cyber criminals are getting more active in today’s society, harming millions of consumers. It is essential to encrypt everything to stop these people from stealing priceless data. Fortunately, three alternative encryption techniques may be used: symmetric encryption, asymmetric encryption, and hash functions (Keyless). In this blog, we will be mainly focusing on the difference between symmetric and asymmetric key cryptography, and will also be explaining them both in detail. Before getting into symmetric key cryptography vs asymmetric key cryptography, let’s first understand the basic terms, i.e., cryptography. Data must be encrypted using a method that only parties with the proper authorization may decipher. It shouldn’t be simple for third parties to read it in case of any leakage or assault. In general, the cryptography process changes plaintext (readable data) into ciphertext (enciphered data). The cipher is a set of two algorithms used to encrypt and decode data afterward. Furthermore, special keys have been used together with algorithms. Without them, we couldn’t read the data even if we possessed ciphertext and the algorithms. Now, we have a basic understanding of what cryptography is. Let’s now understand some of the important cryptography terminologies. Below, we have explained the basic cryptography terminologies. It involves utilizing cryptography to secure information. This method of locking information encrypts the data. Learn the difference between Encryption and Hashing. It is the process of applying cryptography methods to unlock or decode the encrypted data or information. For both encrypting and decrypting data, you need a password. Cryptography utilizes a variety of key types. Only the sender and the recipient of the information are aware of it. Let’s now focus on symmetric key cryptography vs asymmetric key cryptography. Below we have explained the basic difference between the two in a tabular form on the basis of various factors. Summing up, the major difference between the two is – Symmetric key cryptography uses a single key for both encryption and decryption, making it faster but requiring secure key distribution. Asymmetric key cryptography, on the other hand, uses a pair of keys (public and private) for enhanced security and key management but is slower in comparison. We have explained the difference between Symmetric and Asymmetric Key Cryptography. To understand these differences better, let’s focus on symmetric and asymmetric cryptography in detail. One key is used for both encryption and decryption in symmetric encryption. The algorithm and key combine to encrypt the original sensitive information by converting plaintext into ciphertext. This is effective for storing data that has to be decrypted at a later time. The use of a single key for encryption and decryption raises concerns because if the key got compromised, all the data it has encrypted would also be at risk. As you can see in the image below, only a single key is used in symmetric key cryptography. One such example of symmetric cryptography is bank transactions via payment applications. To prevent identity theft and fraudulent charges, personally identifiable information (PII) must be protected when used in payment applications. Let’s discuss the advantages and disadvantages of symmetric cryptography. Some of the advantages of symmetric key cryptography are: Apart from the advantages that it can provide, there are some disadvantages. These are: Asymmetric cryptography, commonly called public key cryptography, is a more recent technology than symmetric encryption. A plain text is encrypted using two keys in asymmetric encryption. Over the Internet or a vast network, secret keys are exchanged. It prevents malicious individuals from misusing the keys. Asymmetric cryptography uses two related keys to increase security since it is crucial to keep in mind that anybody with access to the secret key may decrypt the message. Anybody who wants to send you a message may get a public key. The second private key is kept secret so that only you are aware of it. A message encrypted with a public key can only be decrypted with a private key. Since the public key is accessible to the whole public and may be sent via the Internet, security is not necessary. Asymmetric keys are far more effective in ensuring the confidentiality of data sent during transmission. Let’s now discuss the advantages and disadvantages that Asymmetric cryptography can offer. Some of the advantages of Asymmetric key cryptography are: Asymmetric key cryptography also has some disadvantages, these are: Now we have compared Symmetric Key Cryptography vs Asymmetric Key Cryptography. The main difference between symmetric and asymmetric key cryptography is that in the case of symmetric cryptography, there is only one private key which is used for both encrypting and decrypting data. Whereas, in the case of asymmetric cryptography, two keys are used: one is public, and the other is private key. Two main types of cryptographic algorithms are: The other name for symmetric key cryptography is secret-key cryptography. RSA is a type of asymmetric key cryptography. It uses two keys: a public one for encryption and a private one for decryption. In this blog, we have covered the fundamental difference between symmetric and asymmetric key cryptography, and we also have explained symmetric and asymmetric key cryptography in detail for better understanding.Introduction
What is Cryptography?
Cryptography Terminology
Encryption
Decryption
Key
Difference between Symmetric and Asymmetric Key Cryptography
Factors Symmetric Key Cryptography Asymmetric Key Cryptography Size of cipher text The same or smaller than the original plain text The same or larger than the original plain text Data size Used for large amounts of data Used for small amounts of data Resource Utilization Low High Key Lengths 128 or 256 bits 2048 or higher Security Less secure as only one key is used for both encryption and decryption More secure as two keys are used, one for encryption and the other for decryption Number of keys One key for both encryption and decryption Two keys, a public key and a private key, one for encryption and the other for decryption Techniques Provides confidentiality Provides confidentiality, authenticity, and non-repudiation Confidentiality Only the key holder can decrypt the message Only the private key holder can decrypt the message Speed Fast Slow Algorithms Examples: 3DES, AES, DES and RC4 Examples: Diffie-Hellman, ECC, DSA, and RSA What is Symmetric Cryptography?
Advantages of Symmetric Key Cryptography
Disadvantages of Symmetric Key Cryptography
What is Asymmetric Cryptography?
Advantages of Asymmetric Key Cryptography
Disadvantages of Asymmetric Key Cryptography
Frequently Asked Questions
Q1 – What is the difference between symmetric and asymmetric key cryptography?
Q2 – What are the 2 main types of cryptographic algorithms?
Q3 – What is another name for symmetric cryptography?
Q4 – Is RSA asymmetric or symmetric?
Conclusion







