Top Cyber Security Interview Questions and Answers

While attending a job interview, one should have the confidence and the clarity to crack it effortlessly. This handpicked collection of the top cyber security interview questions and answers for a cyber-security job interview aims to help you prepare effectively for your next cyber security job interview. However, depending on the scope of the position, cyber security interview questions may test candidates’ familiarity with a wide range of technologies. You will need to demonstrate your trustworthiness, dependability, problem-solving expertise, inventiveness, and composure under pressure situations since cybersecurity jobs require safeguarding critical corporate data. Cybersecurity is the practice of safeguarding digital systems, networks, and data from unauthorized access, attacks, and potential damage. It encompasses a wide range of technologies, processes, and practices designed to protect information, devices, and infrastructure from cyber threats. These threats can take various forms, such as hacking, malware, phishing, ransomware, and more. Cybersecurity involves implementing layers of defense mechanisms, including firewalls, encryption, access controls, intrusion detection systems, and regular updates to ensure that sensitive information remains confidential, systems function reliably, and online interactions remain secure. In an increasingly interconnected and digital world, cybersecurity plays a crucial role in preserving the integrity, confidentiality, and availability of digital assets and ensuring the trust and privacy of individuals, businesses, and organizations. We’ve compiled a list of cyber security interview questions and answers to help you prepare for your next one. Let’s dive in! Here are the top 10 basic cyber security interview questions and answers – Cryptography is a method used for information protection from unauthorized parties called adversaries. It involves changing plain text into encrypted text (called “ciphertext”) and then back to plain text. Cryptography aims to ensure the confidentiality, integrity, and authenticity of information while it is being transmitted or stored. Cryptographic techniques include encryption (using symmetric or asymmetric key algorithms), digital signatures, message authentication codes, and hash functions. Cryptography is used in various applications, including secure communication, email, file protection, and online transactions. Here’s a comparison table between Symmetric and Asymmetric encryption, with key differences: The CIA triad is a framework or model encapsulating the three primary objectives of information security: confidentiality, integrity, and availability. The CIA triad is a commonly used framework for assessing the security of information systems and is considered a cornerstone of information security. The three components of the CIA triad are interdependent and must be considered together to ensure the overall security of information systems. The three-way handshake, also known as the TCP (Transmission Control Protocol) handshaking process, is a method used to establish and terminate a reliable communication session between two devices over a network. The three-way handshake consists of three steps: A traceroute is a network diagnostic tool that shows the route packets take from source to destination, including the time it takes for each hop. It is used to identify and troubleshoot network delays, locate bottlenecks and detect if a server is down or not reachable. You can protect your server by taking five simple, practical steps. These are: Here’s a comparison of HID (Host-based Intrusion Detection) and NID (Network-based Intrusion Detection): A brute force attack is a method where one try multiple combinations of username/password pairs to get into an unauthorized system. It is called a “brute force” attack because the attacker tries every possible combination of inputs until the correct one is found. This type of attack can be used on any system that relies on a username and password for authentication, including websites, servers, and even personal computers. Steps to prevent brute force attack: You can also check out – Bluetooth Hacking The OSI (Open Systems Interconnection) model is a 7-layer reference model that defines the rules and standards for communication between computers: A Distributed Denial of Service (DDoS) attack is a type of cyber-attack that attempts to make a website or online service unavailable by flooding it with a large number of requests from multiple sources. The goal of a DDoS attack is to overload the target’s servers, network, or resources, making it impossible for legitimate users to access the service. Some steps to prevent DDoS attacks are: You should also know the difference between DoS and DDoS Attack. These are the top 10 basic Cyber security interview questions curated by our experts with the help of our Cyber Security trainers. If you are going for a cyber security job interview, these interview questions are definitely going to help you. Now let’s move on to some advanced Cyber Security Interview Questions. Here are the top most asked Advanced Cyber Security Interview Questions and Answers – Data is encrypted and decrypted using the Secure Socket Layer (SSL) protocol on a secured server to prevent unauthorized access. The four stages to secure a server are as follows: Step 1: Password-protect the root and administrator users. Step 2: For Managing the system, create new users. Step 3: Avoid giving administrator or default root accounts remote access. Step 4: Configuring firewall rules is important for remote access. By creating a private and secure network, a virtual private network, or VPN, shields your online activities from the dangers of a public internet connection. Use a VPN to boost your anonymity and privacy when performing things like sending emails, making online payments, and conducting e-commerce. Working of VPN: You can take the following precautions to avoid identity theft: The identical password hashes will be generated if two users share the same password. In such a scenario, a dictionary or brute-force attack can be used to quickly crack the password. A salted hash is used to prevent this. A salted hash is one that adds or prefixes a random string (salt) to the password before hashing in order to randomize hashes. As a result, two entirely distinct hashes are generated, each of which can be used to defend the database users’ passwords from an attacker. In phishing, an attacker acts as a reputable entity (a real person or business) in order to manipulate the victim and gain sensitive information. It can be done by requesting that the victim click on a harmful link or download a dangerous attachment in order to obtain private data including credit card numbers, usernames, passwords, and network credentials. Incorporating secure communication methods, such as utilizing video interview software, can also help in verifying the identity of individuals and reducing the risk of falling victim to phishing attacks. Here are some strategies for avoiding phishing: An online application’s database server, such as MySQL, SQL Server, or Oracle, can be attacked via a technique known as SQL injection, which involves the execution of malicious SQL queries. The goal is to get illegal access to sensitive information, such customer information, personal information, information on intellectual property, and so forth. An organization’s data integrity is lost as a result of this attack because the attacker has the ability to add, change, and delete records from the database. Here are some of the methods to prevent SQL injection: A hacking attempt known as a “Man-in-the-Middle” (MITM) attack occurs when a hacker inserts himself in the middle of a conversation between two people in order to acquire their data. Let’s say that A and B are the parties communicating. The hacker then enters this conversation. He impersonates party B in front of party A and party B to party A. Both parties’ data are transferred to the hacker, who then redirects it to the intended recipient after stealing the necessary info. While the two parties believe they are speaking with one another, they are actually speaking with the hacker. You can prevent MITM attack by using some of the below mentioned practices: Despite their differences, vulnerability assessment, and penetration testing, both play a crucial role in securing the network environment. These are the most important Advanced Cyber security Questions and Answers. If you want to learn Cyber Security in-depth, you should check out our Certified Ethical Hacker Course. It is rated the best course in the IT industry for Cyber Security Enthusiasts. In conclusion, these top cyber security interview questions and answers are crucial for both the interviewer and interviewee to gauge the level of understanding and experience with cyber security. It’s essential for organizations to secure their systems and protect sensitive data, making the selection process for hiring a cyber security professional an important one. The candidate’s answers to these questions provide valuable insight into their technical skills, problem-solving abilities, and overall approach to cyber security. As the threat landscape continues to evolve, organizations need to ensure they have the right professionals in place to defend against potential attacks. Suggested ReadsIntroduction
About Cyber Security
Basic Cyber Security Interview Questions and Answers
Q1 – What is Cryptography?
Q2 – What is the difference between Symmetric and Asymmetric encryption?
Key Differences Symmetric Encryption Asymmetric Encryption Size of Cypher Text Cypher text is smaller as compared to the original file Cypher text is larger as compared to the original file Key Length Depending on the level of protection required, the length of the keys that are often used is either 128 bits or 256 bits The key length is substantially higher, for example, the suggested RSA key size is 2048 bits or higher Speed & Efficiency Faster and more efficient Slower and less efficient, as there is a usage of two keys Key Exchange The key must be securely exchanged between the sender and the recipient, which can be a challenge in practice Key exchange is simplified Examples AES, DES, Blowfish RSA, Elliptic Curve Cryptography (ECC), Diffie-Hellman algorithms Q3 – Explain the CIA triad.
Q4 – What is a three-way handshake?
Q5 – What is a traceroute? Why is it used?
Q6 – What steps will you take to secure a server?
Q7 – What is the difference between HIDS and NIDS?
Feature HIDS NIDS Purpose Detect intrusions on a single host Detect intrusions on the network Location Installed on individual host Installed at the network perimeter Data Analyzed Local system logs, process tables, files, etc. Network packets and traffic Performance Impact High, as it runs on the host Low, as it runs on a separate device Detects Intrusions on a specific host Intrusions across the network Q8 – What is a Brute Force Attack? How can you prevent it?
Q9 – What are the different layers of the OSI model?
Q10 – Explain the DDOS attack and how to prevent it?
Advanced Cyber Security Interview Questions and Answers
Q11 – What countermeasures will you take to secure a server?
Q12 – Do you know what is a VPN?
Q13 – Do you know how to prevent identity theft?
Q14 – What are salted hashes?
Q15 – What is phishing and how do you prevent it?
Q16 – What is SQL injection and how to prevent it?
Q17 – What is the MITM attack and how to prevent it?
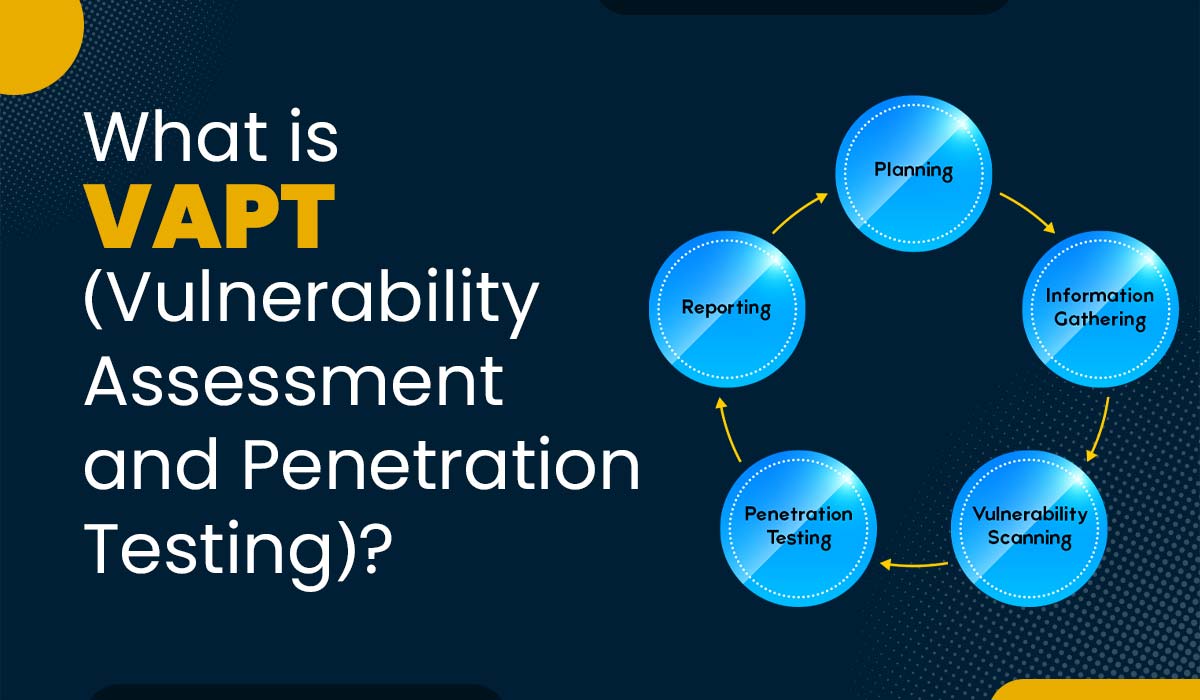
Q18 – Explain the difference between vulnerability assessment and penetration testing.
Conclusion
Penetration Testing Interview Questions