What is VAPT (Vulnerability Assessment and Penetration Testing)?
Nowadays, cybercrimes have seen a massive increase due to the development of new technologies and our reliance on Internet usage. Hackers and cybercriminals are trying to find newer ways to exploit vulnerabilities in systems and networks to steal sensitive information. This, in return, poses a serious threat to businesses, organizations, and individuals. Vulnerability assessment and penetration testing, also known as VAPT has now become crucial for everyone in order to find security weaknesses and loopholes before hackers take advantage of it. In this blog, we will explain VAPT in cyber security, its purpose, its different types, and its working. We will also look into the basic difference between Vulnerability assessment and penetration testing. Before getting into more details, let’s first understand what VAPT really is. Vulnerability Assessment and Penetration Testing (VAPT) is a process that involves identifying, evaluating, and addressing security vulnerabilities in networks, systems, or applications. It consists of two elements: During vulnerability assessment, automated tools are used to scan systems for known vulnerabilities like software, misconfigured settings, or weak passwords. This helps organizations pinpoint weaknesses in their systems that could be exploited by cybercriminals. On the other hand, penetration testing entails simulating real-world cyber attacks to evaluate a system’s security. Ethical hackers, also known as penetration testers, try to exploit vulnerabilities in a controlled setting to assess how well the system can withstand attacks. The primary goal of VAPT is to detect and resolve security vulnerabilities before individuals can leverage them. Through regular VAPT assessments, organizations can enhance their defenses and, side-by-side, lower the risk of cyber incidents and safeguard sensitive information from breaches. Whatever industry your company operates in, vulnerability assessment and penetration testing are essential. It is about confirming and evaluating your company’s security position. To put it simply, it’s a way to determine whether or not your business is safe from external threats. We hear a lot about hacking problems and cyberattacks these days. Networks and systems security is a requirement for all of us. You may learn about attacks and security flaws and how to address them by conducting vulnerability assessments and penetration tests. Let’s now understand the different types of VAPT in cyber security. There are several types of VAPT assessments that organizations can conduct to enhance their security posture. Some of the most common types include: One way to assess a network’s security is through network penetration testing, which is a type of security audit. It is among the best methods for spotting and stopping both real and possible cyberattacks and hacks, as well as safeguarding critical data and information you keep on the network and move between different networks. The goal is to attempt to breach the system by simulating a cyberattack. Another method for examining the website’s cyber security is web application penetration testing. It is employed to identify the website’s or its web applications’ vulnerabilities. It may be used for black hat or white hat tasks. Web application penetration testing is done to identify the website’s vulnerabilities before malicious hackers do. Typically, penetration testing is used to identify the website’s security flaws, which are subsequently reported to the relevant team. The technique of examining a mobile application for security flaws is known as mobile penetration testing. This procedure is carried out to guarantee that the apps are not disclosing private information to unaffiliated parties. This is an important stage for a mobile application, as even a little system error can result in significant financial loss for a business. Mobile application penetration involves testing all types of mobile apps, such as: This involves testing the security of wireless networks, such as Wi-Fi or Bluetooth, for vulnerabilities like weak encryption, unauthorized access points, or rogue devices. Wireless network penetration testing helps organizations secure their wireless infrastructure and prevent unauthorized access to sensitive data. Before getting into the functioning of VAPT, let’s first understand the basic difference between vulnerability assessment and penetration testing. Below, we explained the difference between the two in a tabular form based on different factors. Let’s move on to its functioning in detail. The process of conducting a VAPT assessment typically involves the following steps: The first step in conducting a VAPT assessment is to define the scope of the assessment, identify the target or applications, and establish the goals as well as objectives. Once the scope is defined, the next step is to gather information about the target systems or applications, such as IP addresses, domain names, or network configurations. With this information, one can easily identify potential vulnerabilities as well as plan the testing approach. After the information-gathering process, it’s time to scan the target systems or applications with the use of automated tools for known vulnerabilities. This includes outdated software, misconfigured settings, or weak passwords. With the help of vulnerability scanning, it will be easier to get information regarding potential weaknesses that need to be addressed. The next stage is penetration testing. Here, penetration testers simulate real-world cyber-attacks in order to test the security of the target systems or applications. Now, the question that arises is how one can simulate cyber-attacks. Here, the penetration tester attempts to exploit vulnerabilities in a controlled environment in order to assess the system’s resilience to attacks. The sole purpose of penetration tests is to help identify security gaps that need to be taken care of. There are several types of penetration testing that organizations can conduct. Some of the most common types include: The last stage is Reporting. Now it’s time to compile a detailed report of all the research, including identified vulnerabilities, potential risks, and recommended actions that can be taken to strengthen the network as well as the system. This report assists in helping organizations to understand their security status, prioritize security measures, and in the end, improve their overall security of the system. VAPT, or Vulnerability Assessment and Penetration Testing, is a process by which one can test their applications and IT networks. There are different stages in it, these are: VAPT is a subset of cybersecurity that solely focuses on identifying and exploiting vulnerabilities in order to find security weaknesses in systems and networks. VAPT or Vulnerability Assessment and Penetration Testing includes identifying vulnerabilities and exploiting them, whereas pen test or penetration testing focuses on exploiting vulnerabilities to assess security weaknesses. The scope of the VAPT revolves around identifying security vulnerabilities, assessing networking configurations, and reviewing security policies and procedures. Companies are searching for innovative ways to safeguard their data urgently since the frequency of data breaches is increasing. There is no shortage of information on the internet about data protection strategies for businesses. The fact is that in order to protect the data, enterprises of all sizes must use an excellent VAPT solution. In this blog, we have explained What it is, Its purpose, different types, and its functioning. Feel free to use the comment section below if you have any queries or suggestions.Introduction
What is VAPT?
Why is Penetration Testing Important?
Different types of VAPT
Network Penetration Testing
Web Application Penetration Testing
Mobile Penetration Testing
Wireless Network Penetration Testing
Vulnerability Assessment Vs Penetration Testing
Factor Vulnerability Assessment Penetration Testing Purpose Identify and prioritize vulnerabilities. Simulate real-world attacks to exploit vulnerabilities. Scope Broad and comprehensive. Focused and targeted. Approach Passive assessment using automated tools. Active assessment involving manual testing. Timing Regularly conducted. Periodic or in response to specific concerns. Output List of vulnerabilities with remediation recommendations. Detailed report of exploits, impact, and recommendations. Skill level required Basic security knowledge. Specialized skills in ethical hacking. Legal implications Low risk of disruptions or legal issues. Potential legal risks if unauthorized access occurs. Cost Lower cost due to automation and less specialized skills. Higher cost due to specialized skills and manual testing. How Does VAPT Work?
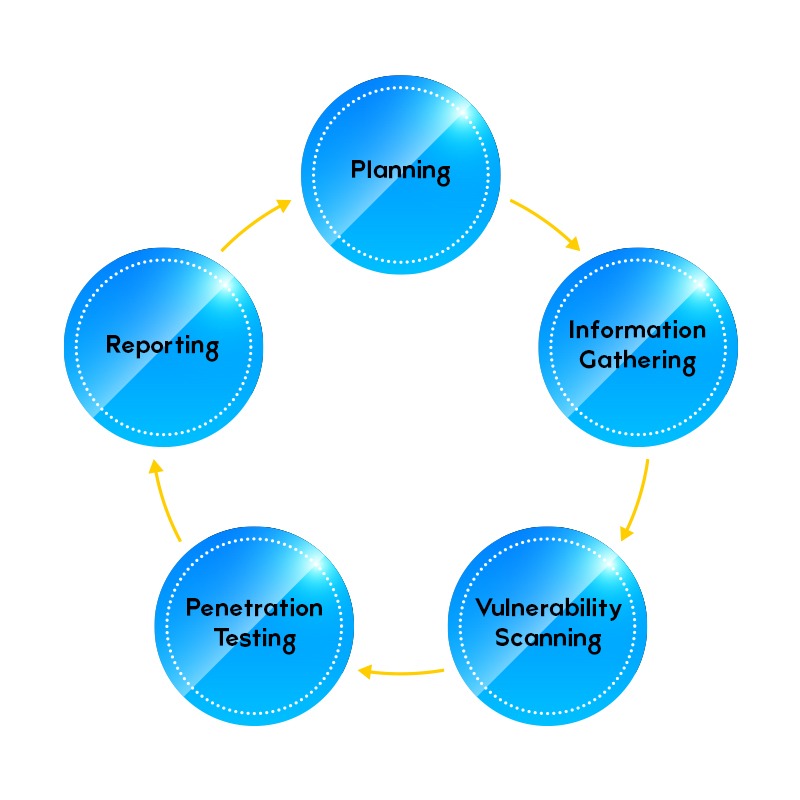
Planning
Information Gathering
Vulnerability Scanning
Penetration Testing
Reporting
Frequently Asked Questions
Q1. What is Vapt and how IT works?
Q2. What is the difference between VAPT and cyber security?
Q3. What is the difference between VAPT and pen test?
Q4. What is the scope of the VAPT?
Conclusion







