
Introduction With the rapid advancement in technology, individuals must go for IT courses that will help them acquire specialized skills that are in high demand. For beginners especially, it can be challenging to get a job in the present competitive market. Now, how do students get job assurance after completing IT courses? This is where […]
Read More
Introduction In today’s competitive market, getting a job can be difficult for many students as well as recent graduates. With the uncertainty of finding employment after completing their education, many individuals are left feeling anxious and overwhelmed. This is where a 100% job guarantee comes into action. In this blog, we will explain the meaning […]
Read More
Introduction In today’s world of connectivity, Wide Area Networks (WANs) play a major role in connecting different networks irrespective of the location. This further assists in smooth communication and data transfer among clients and organizations. As cloud computing and remote work become more prevalent, having a good knowledge of the WAN types is crucial for […]
Read More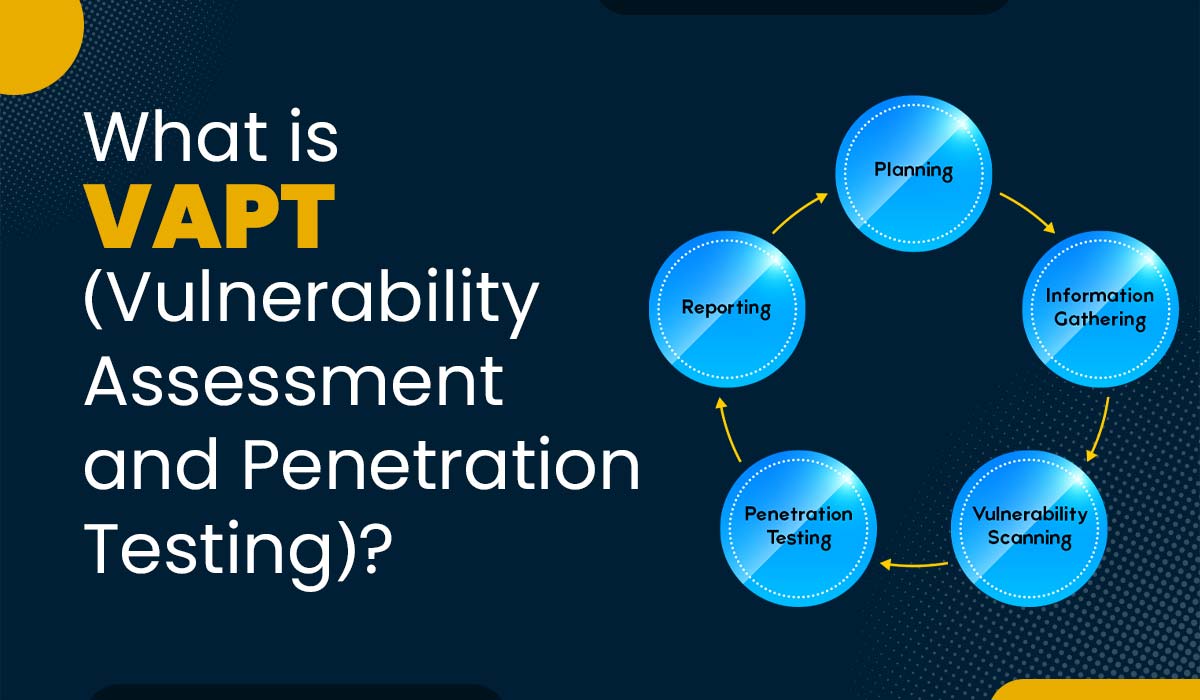
Introduction Nowadays, cybercrimes have seen a massive increase due to the development of new technologies and our reliance on Internet usage. Hackers and cybercriminals are trying to find newer ways to exploit vulnerabilities in systems and networks to steal sensitive information. This, in return, poses a serious threat to businesses, organizations, and individuals. Vulnerability assessment […]
Read More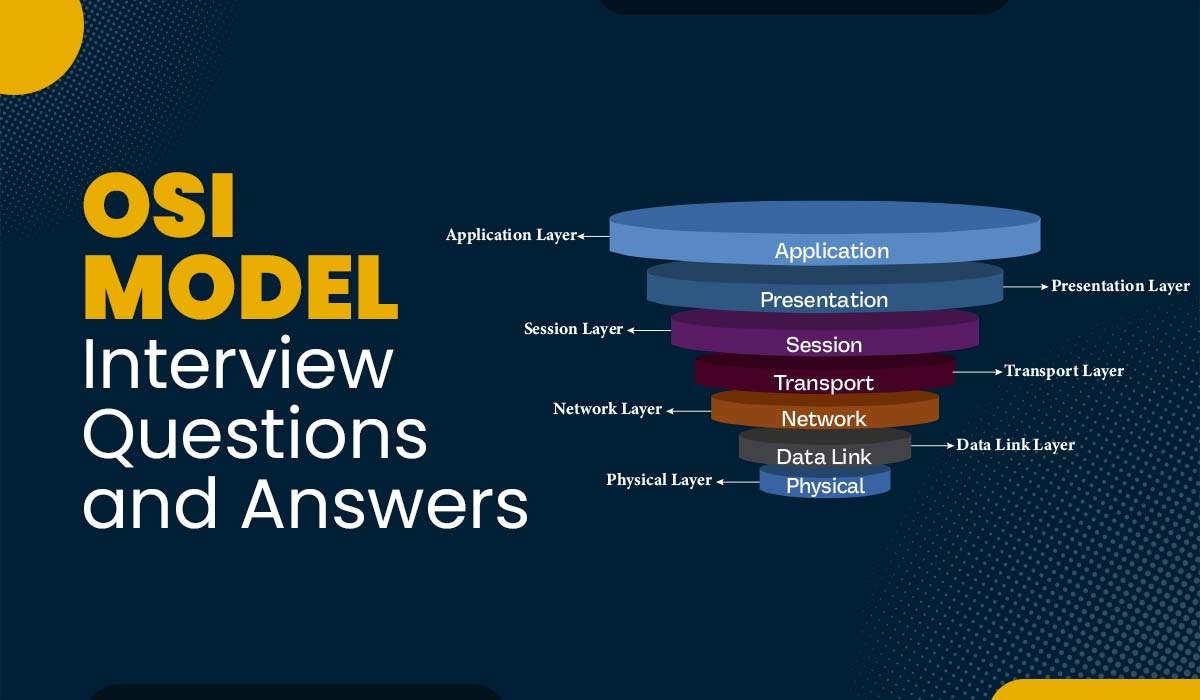
Introduction If someone is preparing for a network-related job interview, it is possible that they may encounter some questions based on the OSI model. In order to help students clear their interviews, we have hand-picked some of the most asked and important OSI model Interview questions and answers for freshers as well as working professionals. […]
Read More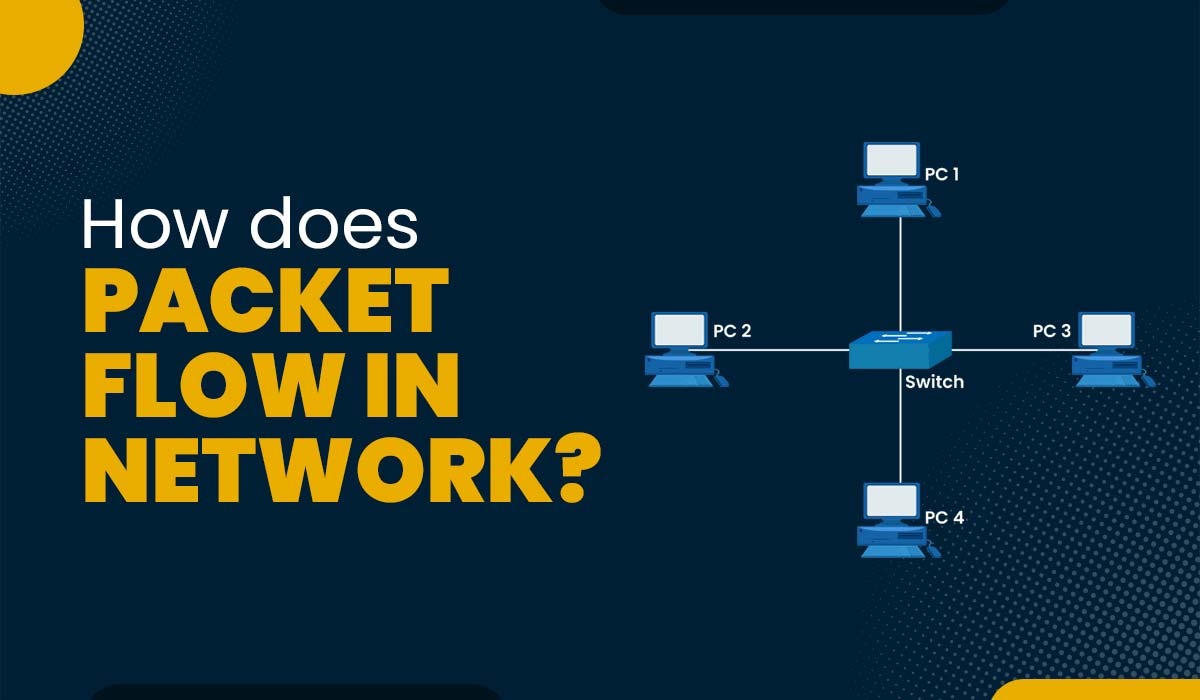
Introduction Packets are the basic units of data that are transmitted over a network. A packet is a small piece of information that contains the source and destination addresses, the data itself, and some additional information for error checking and routing. Packets are sent from one device to another through various intermediate devices, such as […]
Read More
Introduction Multicast is a technique that allows one source to send data to multiple destinations simultaneously without duplicating the data packets. This can save bandwidth and improve network efficiency, especially for applications that involve streaming media, online gaming, video conferencing, or distributed computing. However, multicast routing is a challenging task, as it requires the network […]
Read More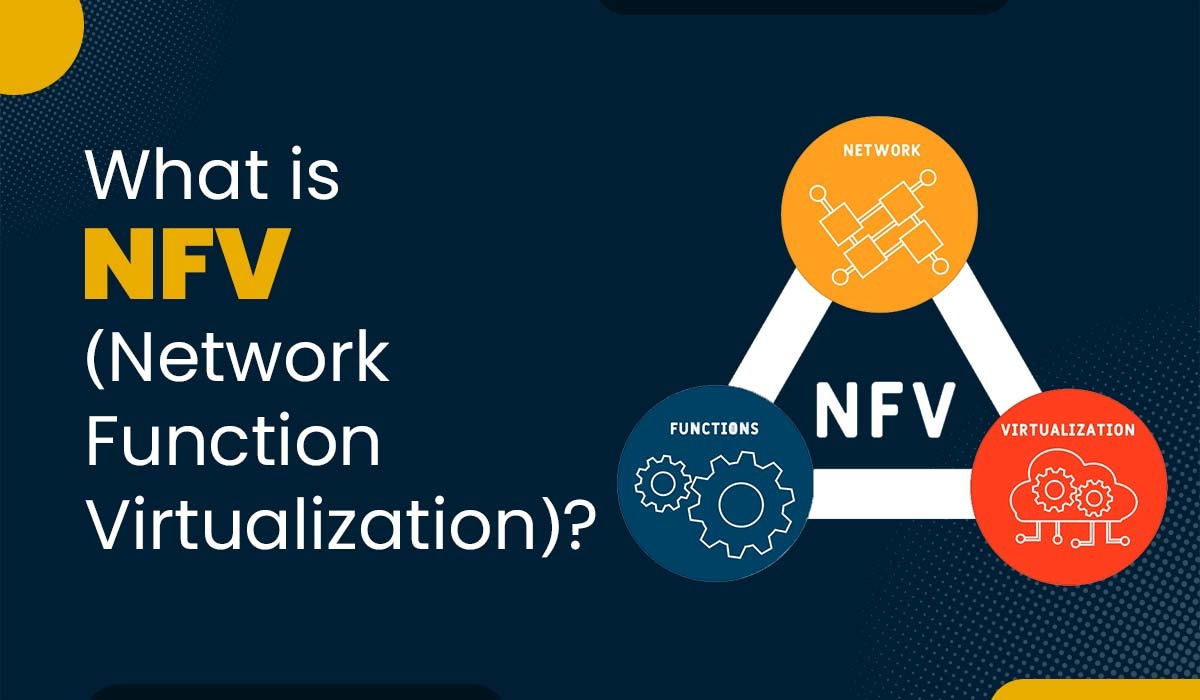
Introduction NFV stands for Network Function Virtualization, and it’s a way of running network services, such as routers, firewalls, and load balancers, on virtual machines (VMs) instead of physical hardware. This means one doesn’t need to buy expensive and specialized hardware for each network function. One can just use standard servers and run multiple functions […]
Read More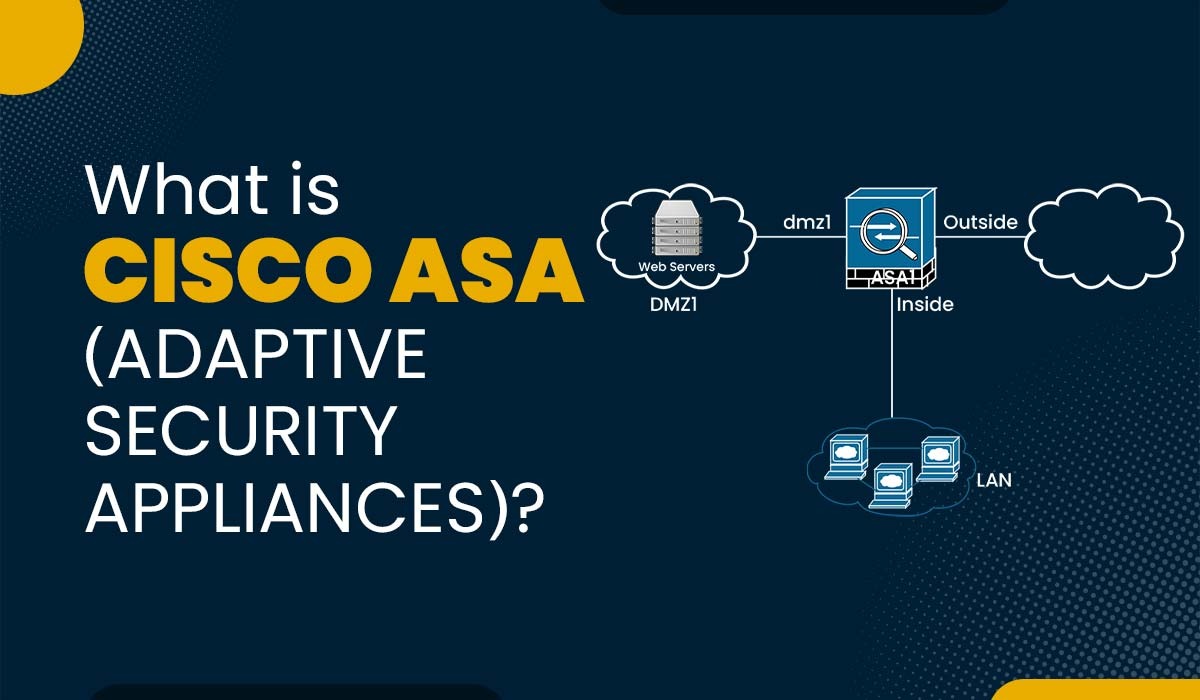
Introduction Nowadays, network security is more than crucial for any organization that completely relies on the Internet for its operations. Cyberattacks can lead to an impact on the integrity, confidentiality, and availability of data as well as network resources. Therefore, it is mandatory for all to have a robust network security solution that can protect […]
Read More
Introduction As we all know, the networking industry is developing rapidly, and all companies are becoming increasingly dependent on networking technology. The demand for network engineers is also increasing; hence, people are focusing on this field due to the enormous demand. If you are also interested in making a career in it, you must know […]
Read More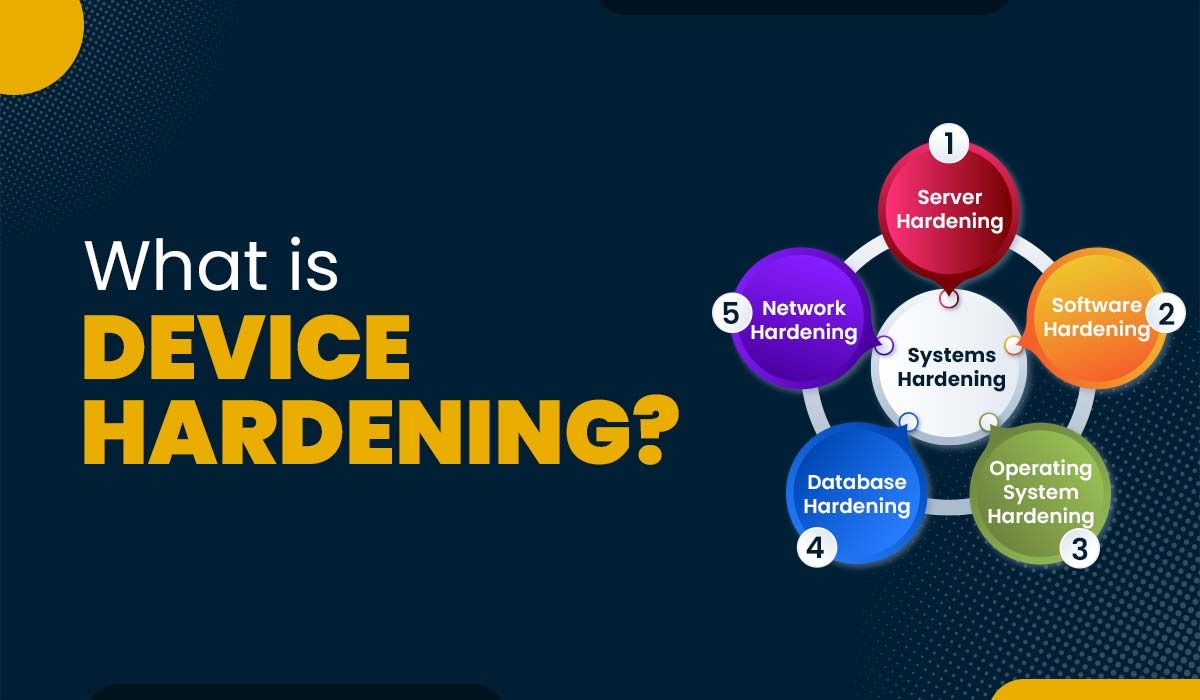
Introduction The internet has completely transformed how we communicate, work, learn, and entertain ourselves. It has also brought new opportunities for innovation, collaboration, and creativity. Along with these opportunities come risks. Cyberthreats are constantly becoming more sophisticated, targeting not only large organizations and governments but also individuals and small businesses. These cyberattacks can compromise the […]
Read More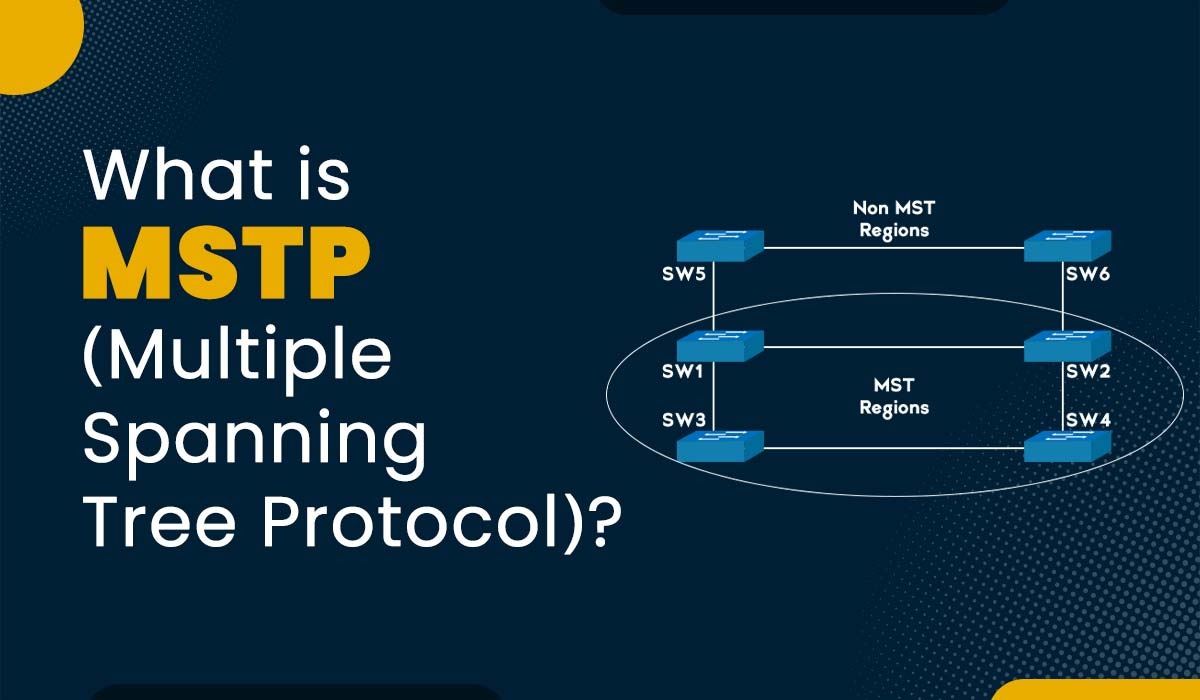
Introduction Networks are becoming more complex and demanding as the number of devices and applications increases. In order to ensure efficient communication, network engineers must utilize protocols that can handle Vlans, redundancy, and load balancing. One protocol that serves this purpose is MSTP. It is an extension of the STP (Spanning tree protocol), which assists […]
Read More










