Bluetooth Hacking and its Prevention
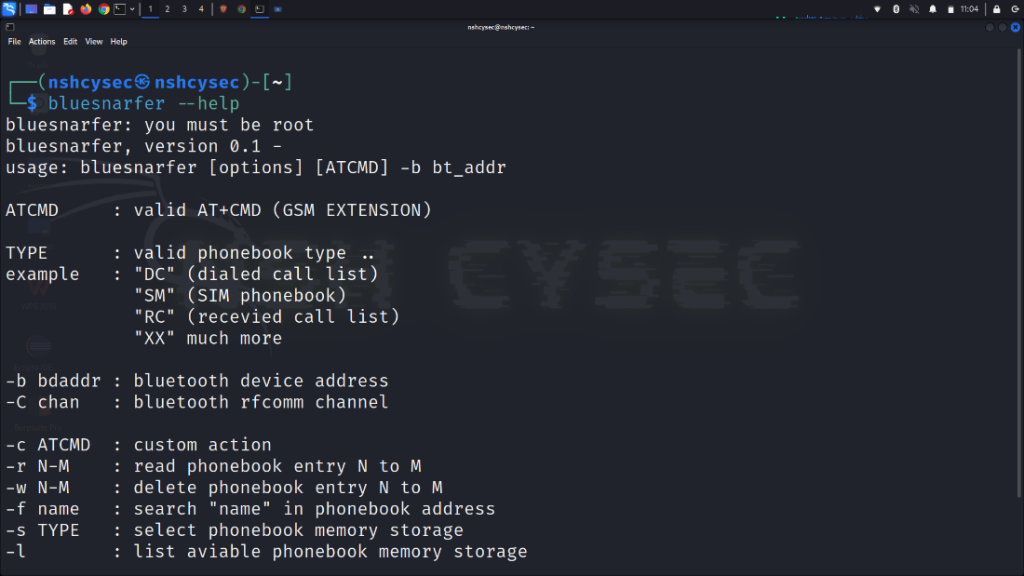
There is less need for wired connections as new innovations in smartphones and other devices become more widespread. These days, Bluetooth wireless communication is used by the vast majority of devices to establish wireless connections. Wireless devices are becoming increasingly popular because they allow users to stay connected without carrying cumbersome cables and wires. File sharing, wireless music streaming, data collection from fitness trackers, and more are all possible with its help. Bluetooth is a target for hackers because it can be used to access your devices and steal your data. Bluetooth hacking is becoming more common as more and more devices enter the market. Considering Bluetooth’s extensive usage history, the technology has its problems. Vulnerabilities have been exploited in various attacks throughout time, making the system very susceptible to hacking. Under this blog, we will be focusing on Bluetooth hacking and its types. Let’s Begin! You can also checkout our Certified Ethical Hacker Course which is available at a great discount. The term “Bluetooth Hacking” refers to a kind of cyberattack in which hackers obtain access to a target device by exploiting its discoverable Bluetooth connection. This event occurs as a result of security weaknesses in Bluetooth technology. It’s not only mobile phones that may be hacked through Bluetooth; PCs of all shapes and sizes can be compromised similarly. Bluetooth hacking can range from eavesdropping on conversations and stealing sensitive data to taking control of devices, spreading malware, or conducting denial-of-service attacks. It is important to note that Bluetooth hacking is illegal and unethical, as it violates the privacy and security of individuals and organizations. It is crucial to implement proper security measures, such as using strong authentication and encryption, to protect against Bluetooth hacking attempts. To locate Bluetooth-enabled devices, hackers utilize specialized software. They can also check which networks you’ve linked to in the past, which is useful information since your phone will likely join automatically to any networks it has previously connected to. If hackers can fake a secure network, they can force your gadget to pair with compromised Wi-Fi and Bluetooth gear. The hackers will then be able to flood your phone with spyware, snoop on your activities, and even take information from your text messages and app data. The following is a list of the many hacking tactics that hackers can use to infiltrate your Bluetooth and steal your sensitive data. Here are the various types of Bluetooth attacks – A cyberattack called Bluesmack targets Bluetooth-enabled gadgets. The assault sends an excessively large packet to Bluetooth-enabled devices via the L2CAP (Logic Link Control and Adaptation Protocol) layer, which causes a Denial of Service (DoS) attack. The attack has a relatively small window of opportunity, around 10 meters for smartphones. With strong transmitters, it can transmit to laptops up to a distance of 100 meters. Tool to use: l2ping Using the hacking technique known as “bluejacking,” a person can send unwanted messages—often flirty but occasionally malicious—to any Bluetooth-enabled device in his or her line of sight. The procedure, called “bluejacking,” starts with searching nearby Bluetooth-enabled devices. Bluejackers find frequent regions with plenty of people walking around. After all, they will probably see many users there with Bluetooth-enabled devices that can be discovered. Bus and train terminals, airports, retail centers, pubs, restaurants, and cafes are some of these locations. Then, the hackers search the region for targets for their anonymous communications. A business card is the first thing the bluejacker sends to a device owner within a 10-meter range. The hacker can then send the recipient a message if they agree to it. Tool – bluesnarfer Hackers use Bluebugging to easily access a device when it is in “discovery mode,” or while Bluetooth is enabled. Hackers use Bluebugging to get access to calls, read and send text messages, steal crucial information stored on the device, and even redirect incoming calls to their own numbers. Although laptops were the primary target of bluebugging, hackers soon found ways to exploit the vulnerability in any device that utilized Bluetooth. The attack was developed after the emergence of bluejacking and bluesnarfing. Bluesnarfing refers to the illegal acquisition of sensitive data over Bluetooth. Hackers access networks by infiltrating users’ unprotected mobile devices, such as cell phones, laptops, tablets, and PDAs. It entails taking advantage of Bluetooth flaws to steal information, including text messages, emails, contact lists, and more. It’s crucial to first grasp how Bluetooth functions to comprehend how this attack is conducted. The so-called Object Exchange (OBEX) protocol is used by devices that may communicate via Bluetooth to exchange data with one another. Bluesnarfing attacks need hackers to take advantage of the object exchange (OBEX) protocol by employing programs like Bluediving. It enables attackers to search for Bluetooth-enabled devices and pair with them secretly. Hackers may couple their systems with a targeted device after compromising the OBEX. Then they assault it with bluesnarfing tools. Attackers may steal data from a device that lacks sufficient firmware security. Tool- Bluesnarfer Here are some commonly used Bluetooth hacking tools – This tool enables to search for Bluetooth enabled devices and will try to collect as much information as possible for each newly discovered device after connecting it with the target. It is a GUI-based tool for locating Bluetooth-enabled devices that are both discoverable and concealed. The attackers take advantage of the device’s weakness to access photos, the phonebook, messages, and other private data. When a device’s Bluetooth is turned ON, Bluesnarfing enables a connection to the phone without the owner’s knowledge and allows access to certain parts of the stored data. Bluediving tests the penetration of Bluetooth. Attacks like Bluebug and BlueSnarf are implemented by it. All the hackers get an opportunity to penetrate any of the devices are relatively close in distance and you can prevent it by taking these safety measures. These are the prevention methods one can use to save themselves from Bluetooth hacking. Yes, Bluetooth can be hacked. Vulnerabilities like BlueBorne and Man-in-the-Middle attacks can compromise Bluetooth-enabled devices and allow unauthorized access or spread malware. Implementing security measures and keeping devices updated can help mitigate these risks. Bluetooth can be used for hacking through techniques like Bluejacking, Bluesnarfing, and Bluebugging. Bluejacking involves sending unsolicited messages to Bluetooth-enabled devices, while Bluesnarfing allows unauthorized access to device data. Bluebugging enables an attacker to take control of the device and execute commands remotely, potentially compromising its security and privacy. Yes, Bluetooth can be hacked without pairing. Vulnerabilities in the Bluetooth protocol can be exploited to gain unauthorized access or control over devices, allowing attackers to compromise them without the need for a prior pairing process. Examples include the BlueBorne attack, which can target and compromise devices even if they are not paired. The types of Bluetooth hacking attacks include Bluejacking (unsolicited messages/files), Bluesnarfing (data theft), Bluebugging (unauthorized control), Man-in-the-Middle attacks (intercepting and manipulating communication), Denial of Service attacks (disruption), and the BlueBorne exploit (remotely compromising devices). Bluetooth is a popular feature on most modern gadgets, which is why attackers are so interested in hacking these devices. The four Bluetooth hacking tactics listed above are only a handful of the attack methods that were relevant to highlight, although there are undoubtedly more vulnerabilities. Bluetooth devices are used on a regular basis, whether to connect to vehicle speakers or headphones. As a result, it is critical to educate consumers and businesses about Bluetooth safety to avoid such assaults. You may also like –Introduction
What is Bluetooth Hacking?
How does Bluetooth hacking work?
Types of Bluetooth Attacks:
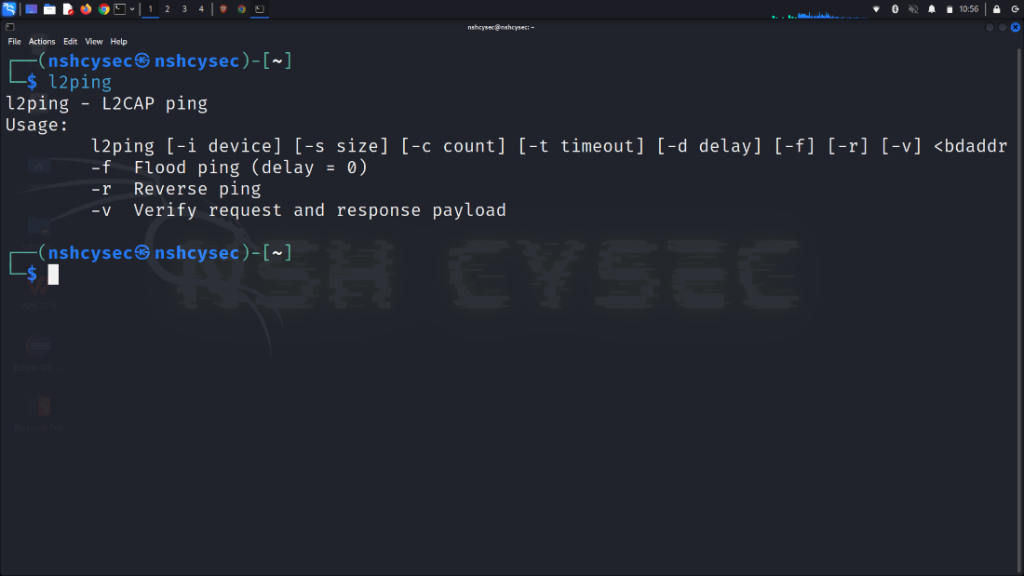
BlueSmacking
BlueJacking
How does BlueJacking work?
BlueBugging
How does BlueBugging works?
BlueSnarfing
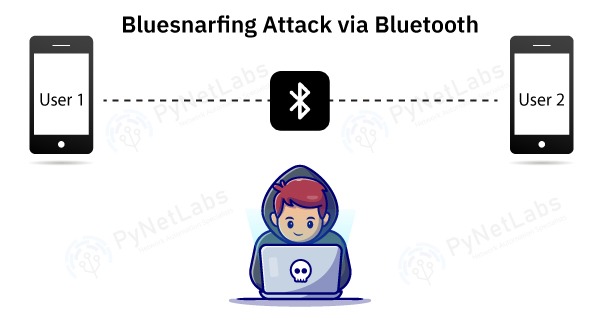
How does BlueSnarfing work?
Bluetooth Hacking Tools
BlueScanner
BlueSniff
BlueBugger
Bluesnarfer
BlueDiving
How to prevent Bluetooth Hacking?
Frequently Asked Questions
Q1 – Can a Bluetooth be hacked?
Q2 – How is Bluetooth used for hacking?
Q3 – Can Bluetooth be hacked without pairing?
Q4 – What are the types of Bluetooth hacking?
Conclusion