What is Access Control List (ACL) in networking?
You may have heard about the Access Control List or ACL. It is used to control permissions to a computer system or network, but do you know what is Access control list? As we know, the Internet is a network of networks, and routers play a vital role in having connectivity between different networks. Routers are used in industries, universities, businesses, corporate offices, schools, colleges, etc., to connect their different branches from different locations. As a router sends traffic from one network to another, sometimes we need to monitor and control this traffic for security purposes. So, we use ACLs, i.e., Access Control List, to control and monitor this traffic. So, let’s understand what is Access control list. Access Control List (ACL) is a list of rules defined for controlling network traffic to reduce network attacks. Using a set of rules specified for the network’s incoming or outgoing traffic, ACLs filter this traffic. Using an ACL is primarily intended to secure your network. Without it, any traffic is allowed to either enter or exit the network. Access control lists are employed on computer networks to forbid or permit particular network traffic. They filter the traffic on the basis of the traffic’s origin and destination. In the current times, Network interfaces and operating systems, like Linux and Windows, are also equipped with ACLs. A user or group of users’ names make up one or more access control entries (ACEs) that are contained within each ACL. The access privileges are specified for each user, group, or role in a string of bits known as an access mask. The person who creates the access control list for an item is often the system administrator or the object owner. Access Control List provides a flexible way to manage various access rights by allowing network administrators to manage access of various people or groups. Here’s how it typically works – This is how ACLs works. They are commonly used in operating systems, network devices, databases, etc to enforce security policies and protect sensitive information from unauthorized access. First, you need to know how traffic moves in and out of the router to enforce ACLs and set rules according to the router’s interface, as it is separate from the network. For example, traffic going into a router means it is going out of the web, so it isn’t easy to understand how the traffic motion is mentioned. Setting an ACL requires the ACL to perform its intended function on the router’s interface. To create a faster process, the router’s hardware implements forwarding and routing decisions. When setting up an ACL entry, enter the source address and the destination address as the router reads the entry if it is represented in this format. Source means where the traffic comes from, i.e. outside the router, and destination is a station beyond the router, where the data packet will terminate. Access Control Lists consists of several components to carry out its operations. Here are some common components of Access Control List – These are some common ACL components. ACLs or Access control Lists can be used for two purposes, namely: As mentioned above, access lists are a set of rules organized in a rule table. A condition, either permit or deny, is provided by each rule or line in an access list. We hope you have a better understanding of what is the purpose of the Access control list. Access Control Lists are kind of security devices that are used to control access to various network devices. Depending on the situation and the specific network devices or systems involved, it can be installed in a variety of places. The following are some typical locations where an access control list can be placed: These are just a few examples of where access control lists can be placed. The specific implementation and configuration of ACLs may vary depending on the system or technology being used. Here are the common types of Access Control Lists available – These Access-lists were created solely utilizing the source IP address. These ACLs either allow or disallow the whole set of protocols. There is no distinguishing between the IP traffic like TCP, UDP, HTTPS, etc. Using numbers 1-99 or 1300-1999; the router will recognize it as a standard ACL and the provided address as the source IP address. IP standard access list – This ACL makes use of source IP, destination IP, source port, and destination port. With these ACL types, we can also mention which IP traffic should be allowed or denied. These use range from 100-199 and 2000-2699. IP extended access list – Reflexive ACLs are also known as IP connection ACLs. They filter traffic based on the session information from top layers. They enable or disable outbound traffic in response to internal router sessions. Outgoing ACL Traffic is detected by router and a new inbound ACL entry is added. Telnet, extensive ACLs, and authorization are used in dynamic ACLs. This type of ACL, often known as “Lock and Key,” can be used for certain time periods. Such lists only allow users to access resources or endpoints after they have established Telnet authentication with the device. These are the types of ACL. There are many benefits of using Access Control Lists (ACLs). Some of these are as follows – Overall, ACL provides a strong framework for access control, improving security, flexibility, and control over resource access. Organisations can mitigate security risks and protect important assets by deploying ACL, which ensures that only authorised persons have proper access to critical information. Here are some disadvantages of Access Control List – Access control lists (ACLs) are used to control network traffic by specifying rules for permitting or denying access to network resources. Examples include allowing or blocking specific IP addresses, defining access permissions based on user groups or roles, and setting restrictions on certain protocols or services. ACLs are commonly used in firewalls, routers, and network devices to enforce security policies and protect against unauthorized access. ACL stands for Access Control List. It is a set of rules or permissions that determines which users or network entities are granted or denied access to specific resources or services. There are two main types of ACLs: Network ACL (NACL) and File System ACL (FACL). Access Control Lists (ACLs) are used to manage and enforce access permissions for various resources or services within a network or system. Administrators can use ACLs to regulate who has access to specific files, directories, networks, or services, as well as what actions they can take on them. Access Control List (ACL) possess various features such as – Granularity, Flexibility, Rule-based system, Hierarchical structure, Audibility, Scalability, and much more. In this blog, we have discussed what is Access Control List (ACL) in networking, how it works and where can they be implemented. An Access Control List (ACL) is a fundamental tool in network security that regulates and controls access to resources. It acts as a protective layer by determining which users or systems are allowed or denied access to specific networks, devices, or data. In summary, Access Control Lists play a vital role in maintaining the integrity and security of networks. They empower organizations to define and enforce access policies, protect sensitive data, and safeguard against potential threats. We certainly hope you have a good idea about Access Control List now. If you want to learn in-depth about such topics, you should join our CCNA training. Please spare a moment and do let us know about your experience in the comment box below. We would love to hear from your side.Introduction
What is Network Access Control List (ACL)?
How does ACL Work?
How to implement Access Control List?
Components of Access Control List
What is the purpose of Access Control List?
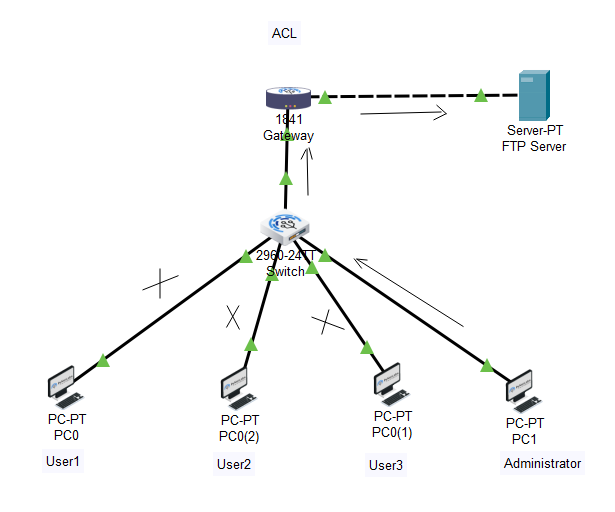
Where can you place an access control list?
Types of ACL (Access Control List)
1. Standard ACL
2. Extended ACL
3. Reflexive ACL
4. Dynamic ACL
Important rules to understand ACL
Benefits of using Access Control List (ACL) –
Disadvantages of Access Control List
Frequently Asked Questions
Q1 – What are Access Control Lists examples?
Q2 – What is ACL and its types?
Q3 – What is the use of ACL?
Q4 – What are the features of ACL?
Conclusion







