What is Policy Based Routing (PBR)?
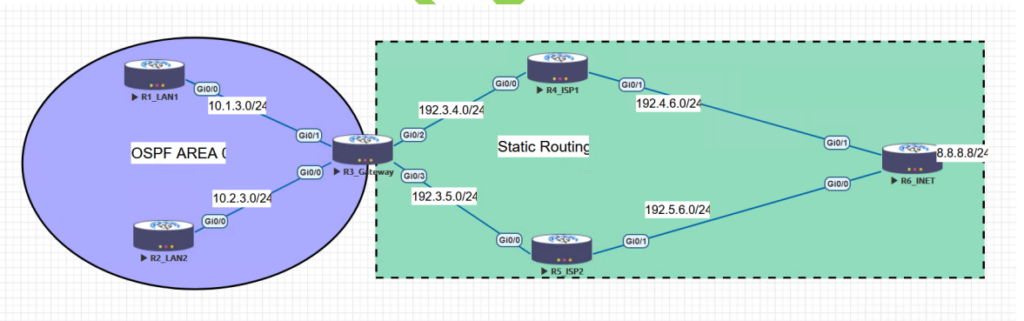
Policy Based Routing is a powerful network management technique that enables efficient control and prioritization of network traffic flow. Nowadays, a number of applications are working side by side, and it’s a must to connect these applications. Because of this, the network traffic nature has become more complicated. Using traditional mechanisms, it may be difficult or even impossible to meet these requirements. Organizations now must place an even greater emphasis on managing their operating expenses than in the past. One way is to maximize the use of resources. One such area is networking, where rather than investing in more capacity, the focus is on making the most of what already exists. All this can be achieved by implementing Policy Based Routing (PBR). You can learn more about PBR in our CCNP ENCOR 350-401 Training. Under this blog, we will understand Policy Based Routing, its benefits, and the configuration of PBR with topology for better understanding. Let’s first understand what policy based routing is and the various advantages associated with using PBR. Policy based routing, sometimes known as PBR is a technique that allows network administrators to control the path of traffic based on specific criteria, such as It can be used to optimize network performance, enhance security, implement load balancing, or enforce policy compliance. PBR can be used as a versatile alternative to traditional routing protocols, including but not limited to OSPF and BGP. Policy based routing (PBR) allows network engineers to apply distinct policies to various types of traffic, thereby enabling more precise and adaptable control over network traffic, as opposed to routing all traffic based on a uniform set of routing rules. For example, different types of data may be sent via distinct paths with varying characteristics, such as higher or lower bandwidth, lower or higher latency, and different security standards or policies. In order to operate properly, Policy Based Routing first compares incoming traffic against a set of rules and then assigns it to a particular set of routes. The specified routing policy is used to inform a set of rules included inside the route map. PBR’s route map supports ACL matching, which allows you to restrict traffic based on factors like origin IP address, destination IP address, protocol, and port. One can also match: After establishing a successful match, you may configure the next-hop device’s IP address. At the same time, you can establish Quality of Service (QOS) values to guarantee that an application receives the required resources to perform optimally. “Deny” statements may also be included in the route map. (If nothing else is mentioned, “permit” will be assumed.) You may use them as a filter, too. If the route map encounters a deny when matching against an access control list, it will skip over that statement and go on to the next one in the map. When a route map statement is encountered that does not have a matching permission statement, the route map is marked as “policy rejected.” The RIB governs the standard traffic forwarding in the event of a policy-rejected situation. Traditional routing systems are designed to direct network traffic according to the respective destination of the data. The continuous expansion of cloud computing, mobility, and web-based applications demands the network’s awareness of every application type of traffic that passes through it. PBR employs a distinct approach for each application type to ensure efficient prioritization, segregation, and traffic routing while maintaining optimal performance and availability. Moreover, the complexities of voice, data, video, and applications residing on a single network expose networks to potential security breaches or limit their ability to effectively counteract such breaches. Business applications are frequently subjected to various cyber-attacks, which pose a significant threat to their security. Policy-based routing (PBR) allows network administrators to categorize network traffic according to specific applications and assign them with corresponding labels for more comprehensive analysis. This approach enhances network security by providing increased visibility, control, regulations, and protection. Traditional routing primarily focuses on destination-based forwarding, whereas Policy-Based Routing (PBR) provides more control over the routing process. PBR can be used to: This is Policy Based Routing is used. Now, let’s verify PBR using a Lab scenario. In this lab, we will take a look at Policy Based Routing configuration. PBR is all about telling the router to forward traffic according to what we set rather than what is in the routing table. We define what traffic is via access lists and create instructions for how to route the matched traffic with a route map. The three steps to configuring PBR are as follows – Let’s quickly start by creating a topology like the one below. In the first phase, we will segregate the traffic transmission so that the traffic coming from LAN2 takes the path via ISP2 to reach the internet (8.8.8.8 in the topology). Step 1: Configure OSPF on R1, R2, and R3. Step 2: Configure Static routes on R4, R5, and R6. Step 3: Configure a default route on R3 towards ISP1 (R4). Step 4: Define the traffic using the access list. R3(config)#access-list 1 permit 10.2.3.0 0.0.0.255 Step 5: Create a route map to define the next hop as ISP2 for the traffic coming from LAN2. R3(config)#route-map REDIRECT 10 R3(config-route-map)#match ip address 1 R3(config-route-map)#set ip next-hop 192.3.5.5 R3(config-route-map)#exit Step 6: Apply the route-map on the required interface R3(config)#int g0/0 R3(config-if)#ip policy route-map REDIRECT We are done! Now it’s time to verify. Let’s trace the path to 8.8.8.8 from R2. R2#trace 8.8.8.8 Type escape sequence to abort. Tracing the route to 8.8.8.8 VRF info: (vrf in name/id, vrf out name/id) 1 10.2.3.3 48 msec 9 msec 9 msec 2 192.3.5.5 20 msec 10 msec 8 msec 3 192.5.6.6 30 msec * 19 msec R2# We can observe that the traffic is taking ISP2 as the next hop to reach destination 8.8.8.8. PHASE 2: Now, in this phase 2 we will try to redirect the HTTP traffic from LAN1 and LAN2 to the ISP2 using an extended ACL. Let’s see how this can be configured. Step 1: Creating an extended ACL to define the traffic. R3(config)#ip access-list extended 100 R3(config-ext-nacl)#permit tcp any eq 80 R3(config-ext-nacl)#exit Step 2: Creating the route-map to define the next hop for HTTP traffic. R3(config)#route-map HTTP-DATA R3(config-route-map)#match ip address 100 R3(config-route-map)#set ip next-hop 192.3.5.5 R3(config-route-map)#exit Step 3: Apply the route-maps to the interfaces attached to our LAN1 and LAN2. R3(config)#int r g0/0-1 R3(config-if-range)#ip policy route-map HTTP-REDIRECT R3(config-if-range)#exit R3(config)#^Z It’s time to verify!! Let’s try to reach 8.8.8.8 via port 80 now. We can do this with telnet and specifying port 80. Therefore, configure telnet on R6 and enable debugging on R3 to verify the functioning of PBR in this case. R3#debug ip policy Policy routing debugging is on R3# Let’s create a telnet connection and observe the debug output on R3. R1# telnet 8.8.8.8 80 Trying 8.8.8.8, 80 … Open You’ll observe logs confirming the policy getting matched and data getting routed towards ISP2. This confirms that we were able to configure the PBR successfully. There are various advantages of using Policy Based Routing in network infrastructures: PBR assists in selecting and forwarding network traffic based on the best available path. The optimal path for traffic depends on various factors, such as the shortest distance, lowest latency, or the highest bandwidth. It also enhances the QoS for certain applications and also reduces congestion on overloaded links. PBR can assist in routing traffic with security policies. It can block or redirect malicious or unwanted traffic to a firewall, IPS, or proxy server. This, in return, prevents attacks and filters content. With PBR, traffic may be routed depending on load balancing parameters, such as delivering it to the multiple links or server that is currently experiencing the lowest volume of traffic. This may improve the network’s scalability and availability. Policy Based Routing can also be used to route traffic based on policy compliance. It includes routing traffic from a specified user to specific destinations or services or assigning QoS levels depending on the kind of traffic. Now, we understand the basic meaning of policy based routing and the advantages of using PBR. You can also check out our webinar on Policy-based routing – PBR can be useful for implementing different policies for different types of traffic and can be used for the following: Static routing and policy-based routing are two methods of forwarding traffic based on different criteria. Static routing is the simplest form of routing, where the administrator manually configures the routes for each destination network or host on the router. In policy-based routing (PBR), an administrator establishes rules that match certain characteristics of the traffic in order to determine which paths it should take. BGP uses Policy-Based Routing because it allows network administrators to control how traffic flows between different autonomous systems. BGP does not use metrics like other routing protocols but relies on attributes and policies to determine the best path for each destination. There are many capabilities associated with PBR; some of these are: This blog mainly focuses on policy based routing (PBR), a technique network administrators use to direct traffic based on parameters such as their source and destination IP addresses, protocol names, port numbers, and applications. We have also shown the topology-based configuration of PBR on Cisco routers. This will provide some understanding of the advantages of PBR and how one can implement Policy Based Routing using a lab scenario.Introduction
What is Policy Based Routing (PBR)?
How does Policy Based Routing works?
Problems addressed by PBR
How can Policy Based Routing be used?
Policy Based Routing configuration
Topology
Advantages of using Policy Based Routing
Optimizing network performance
Better network security
Implementing load balancing
Enforcing policy compliance
Frequently Asked Questions
Q1 – Why do we need Policy-Based Routing?
Q2 – What is static and Policy-Based Routing?
Q3 – Why does BGP use Policy-Based Routing?
Q4 – What are the capabilities of PBR?
Conclusion







