Penetration Testing Interview Questions and Answers

In today’s world, cyberattacks pose several threats to many companies. Therefore, it is of the utmost importance that trained specialists capable of conducting penetration tests have the knowledge to take the measures required to discover all the security gaps and risks hiding in an IT network or an organization. Now, if you want to work in the field of Penetration Testing, you need to practice Penetration Testing Interview Questions. You should also check out our WAPT Course, which is currently available at a great discount. Penetration testing, also known as ethical hacking, is a proactive approach to identifying and addressing vulnerabilities in computer systems, networks, and applications. It involves simulating real-world cyberattacks to assess the security posture of an organization’s digital infrastructure. Skilled professionals, known as penetration testers or ethical hackers, employ a variety of tools and techniques to identify potential weaknesses, exploit them, and gain unauthorized access to systems. The goal of penetration testing is to provide organizations with a comprehensive evaluation of their security controls and help them understand their exposure to potential threats. By conducting penetration tests, organizations can identify and rectify vulnerabilities before malicious actors can exploit them, enhancing their overall security and mitigating potential risks. Let’s move on and get answers to all these penetration testing interview questions. Let’s Start! Here are the top 10 basic Penetration Testing interview questions and answers to help you succeed in your next interview. XPath injection refers to a security flaw when malicious input is utilized to insert unwanted instructions into an XML document. This may be achieved by using specially created elements and attributes or by just inserting any user-supplied string straight into an XPath expression. To exploit software vulnerabilities, injection attacks are mainly used as they allow hackers to run arbitrary code for attack payload. In penetration testing, hijacking execution is a tactic used by attackers to obtain access to targeted systems or networks. Using this technique, an attacker may get access to and exploit the full range of capabilities of a hacked system for malicious purposes. Attackers may exploit extant administrator permissions on target devices and user accounts established particularly for reconnaissance or attack operations. By exploiting these vulnerabilities, hijackers can hack computers without raising red flags in standard security monitoring. XAMPP stands for cross-platform, Apache, MySQL, PHP, and Perl. XAMPP is an extremely popular cross-platform web server that allows developers to test and develop their programs locally. It was developed by the Apache Friends community, and its original source code is available for review and modification. It supports several programming languages and contains MariaDB, Apache HTTP Server, and PHP/Perl interpreters. John the Ripper is a widely used open-source password-cracking program used by penetration testers and security professionals to audit the security of password hashes and find weak passwords that may be readily hacked. It’s compatible with several operating systems, including Windows, Linux, macOS, and UNIX. John the Ripper is used by penetration testers as part of a security assessment to find passwords that are easy to crack. It aids businesses in spotting security flaws, fixing them, and bolstering their data and system security. John the Ripper is also useful for measuring the robustness of password regulations and the efficiency of various password storage strategies, including hashing algorithms and encryption approaches. Local file inclusion (LFI) is a process in which a hacker injects malicious files into request packets aimed at vulnerable systems. An attacker may gain access to sensitive data or possibly gain the ability to run arbitrary code on the vulnerable system. Web applications are especially prone to LFI vulnerabilities, which can be exploited in a remote attack against unsuspecting users that visit affected websites. Using specially crafted HTTP requests, an attacker can get complete control of the program and the data it serves by injecting scripts into the sites it serves. In penetration testing, Remote File Inclusion (RFI) refers to an attack method in which a malicious user uploads files to the target server that aren’t a part of the online application or system under evaluation. These files should be placed somewhere other than the document root. As a result, attackers may steal information, run commands as privileged users, or even take control of infected computers by injecting arbitrary script code into pages served up by vulnerable servers. An incognito attack is a method that may effectively test the safety of a system without raising the risk of the attacker being discovered. You are able to test the safety of a system without the user of the system being aware of the test if you use Meterpreter to carry out an attack using the Incognito mode. Also check out – What is Bluetooth Hacking? Server Side Request Forgery, also known as SSRF, is a simple form of attack in which the server acts as a proxy on behalf of the attacker to make a request either to a local or to a remote source. The server will then return a response that contains the data that was obtained as a result of the request. It’s possible to draw parallels between SSRF and the usage of a proxy or virtual private network (VPN) in that the user first makes a request to a resource, then the proxy or VPN Server makes a request to that resource, and lastly, the proxy or VPN Server returns the results to the original user. Automated scanning and the collection of data are one of the primary obstacles that must be overcome in penetration testing. As a result, this is the point when automation comes into the picture. The available automation now enables penetration testers to automate the actions contributing to data collecting. Capturing and analyzing the data in this way ensures that it is done in an organized and effective manner. In addition to these benefits, automation enables a faster response time for reports, saves time overall, and reduces the amount of labour required. An attacker may get access to sensitive information like user names and passwords stored in a database using SQL injection. This security weakness enables malicious SQL queries to be executed on the database. SQL injection attacks occur when an attacker provides malicious input to a web application that is then passed to a database for processing. The attacker can manipulate the input to include malicious SQL commands that are executed by the database. For example, suppose a web application is vulnerable to SQL injection. In that case, the attacker could modify a query in a way that allows them to retrieve data from the database to which they wouldn’t usually have access. You may also like – These are the top 10 Basic Penetration Testing Interview Questions and Answers for freshers. Let’s move on and see some Advanced Penetration Testing Interview Questions. Here are some advanced Penetration Testing Interview Questions and Answers – USSD Remote Control is an outstanding tool for vulnerability testing. USSD Remote Control makes use of the particular USSD over GPRS signaling protocol. This can be used with a variety of devices to send and receive data over GPRS. There are many benefits to using USSD Remote Control for penetration testing. Thanks to USSD Remote Control, the penetration tester is able to control a wide range of devices remotely. This includes gadgets that aren’t always connected to the internet. USSD Remote Control is a very powerful tool that may be used to control a number of different devices. The penetration tester can also operate remotely on a variety of tasks thanks to it. For example, the penetration tester can use USSD Remote Control to examine devices for weaknesses. There are numerous strategies used in Penetration testing and the phases involved in it are listed below: When it comes to security, many organizations frequently forget about the perimeter. While the majority of the time this is appropriate, failing to sufficiently protect your internal network may cause it to be shut down as a result of breaches that frequently come from outside sources, like malware and phishing attempts. A third-party penetration testing business can help solve some of these problems by providing accurate and reliable information regarding vulnerabilities present in the systems or networks of your company. In addition, they can advise on the best approaches to take, such as vulnerability assessment or rehabilitation. Risk analysis simply investigates any potential flaws that could cause problems with the software, as opposed to penetration testing, which entails legally attacking the system to find the product’s vulnerabilities. While risk analysis takes a more practical approach to problem-solving, penetration testing takes a more technical approach. A risk analysis can be carried out by a finance expert who has some probability understanding, but a penetration tester must be an information technology specialist who is familiar with computer programming and, ideally, hacking. Risk analysis is more useful than penetration testing from a practical standpoint. To enhance an organization’s network security, here is the top network control aid – The Nmap tool can be allowed to scan ports. Below are a few common ports to focus on during pen-testing: Creating a Java applet popup is an intuitive process. First, a Java program must be prepared by the tester to function as a popup. Then, a file with a .html extension should be developed by the tester and moved to the same directory as the Java program. Categorize the file into two parts. The HTML code that allows the Java applet popup to be shown is available in the second part, whereas the first part provides the code that allows the Java applet popup to be created. CSRF stands for Cross-Site Request Forgery which preys on the degree of trust built at the time of an authenticated user experience. For example, in these cases, web-based apps typically do not perform any testing to ensure that the proposed request originally arises from an authenticated user; instead, the only form of verification is shared by the specific web browser the end user is using. How to deflect this happening: A frame injection vulnerability is like a security hole that an attacker exploits to inject an intended frame into the traffic stream running through a website or application. It can be achieved by changing elements in the HTTP request header or by inserting frames in the response shared by the server to the browser. Frames refer to small parts of HTML or XML that allow document content to be composed and displayed on a web page as if it were a part of the actual document. Attackers can insert malicious frames into these returns to inject code directly onto the screens of users of websites and applications that personally impact those individuals, stealing their data and even causing loss of income to online businesses. The amount of penetration testing differs from company to company. Generally, the penetration testing rates quoted depend on the salary of the security tester, the scope of the project, the expense of the tools used, etc. Additionally, some infosec organizations charge less than others due to market competition. These are the top Advanced Penetration Testing Interview Questions and answers. Now, we have the top Penetration Testing Interview Questions for both freshers and experienced candidates that could be asked in a pen-testing interview. The cyber world has a strong need for ethical hackers, yet it is a challenging sector to enter. Hopefully, the following set of Penetration Testing interview questions and answers may be helpful to you. All the best for your Interview. If you want to learn penetration testing in-depth, you can check out CEH Course.Introduction
About Penetration Testing
Basic Penetration Testing Interview Questions and Answers
Q1 – What is XPath Injection in penetration testing?
Q2 – What is Hijacking Execution in pen-testing?
Q3 – What is XAMPP?
Q4 – What is John the ripper tool, and how are penetration testers using it?
Q5 – What is Local File Inclusion (LFI)?
Q6 – What is Remote File Inclusion (RFI)?
Q7 – Explain Incognito attacks with Meterpreter?
Q8 – What is Server-Side Request Forgery vulnerability?
Q9 – Can Penetration Testing Be Automated?
Q10 – What is a SQL injection?
Ethical Hacking Interview QuestionsAdvanced Penetration Testing Interview Questions and Answers
Q11 – Explain what USSD Remote Control is?
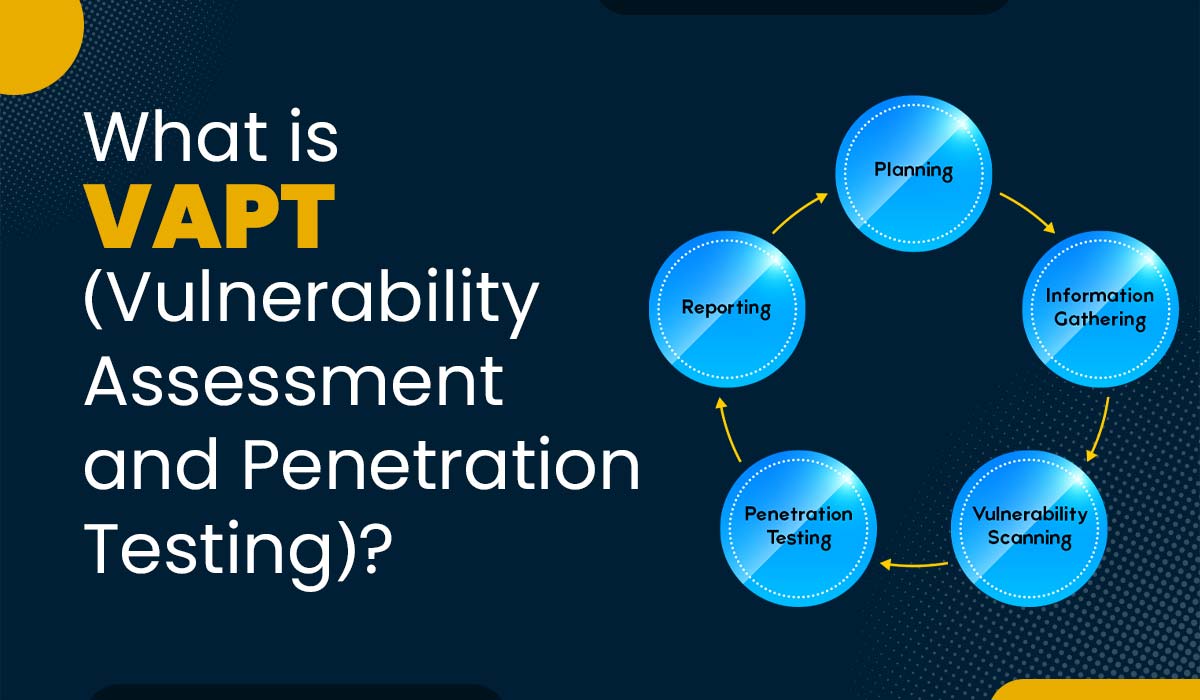
Q12 – Explain what are the phases of Penetration Testing?
Q13 – Should a third-party conduct penetration testing, and why or why not?
Q14 – What are the differences between risk analysis and penetration testing?
Q15 – For strengthening an organization’s network security what network controls would you suggest?
Q16 – What are some common ports to focus on during penetration testing?
Q17 – What is the purpose of Java applet popup in penetration testing?
Q18 – How can CSRF be deflected during pen-test practice, and what does it mean?
Q19 – Explain Frame Injection vulnerability.
Q20 – We received a penetration testing proposal that was quoted much lower than the rest of the proposals we received – why?
Conclusion