Multicast Communication

Before starting about multicasting, we have to understand why we need multicast communication and what possible challenges we can face without multicast communication. In this blog, we will cover how multicasting works and how the data is processed in multicast communication, its advantages, multicast forwarding, and everything you need to know about it. Key Takeaways – The term “multicasting” refers to a method of sending a single message to a large group of people. Multicast Communication is a type of technique that transfers packets from one source to many receivers simultaneously. Multicast is an integral part of PyNet Labs’ CCNA training. Do check it out. Multiple devices can now communicate with one another across the globe because of the interconnectivity made possible by computer networks. This kind of interaction, however, is not easy and requires a wide range of technological resources, from the physical to the logical, to take place. Cables, intermediate devices, addressing schemes, and protocols are all examples of such resources. More specifically, researching and constructing communication systems that ensure messages are addressed correctly is essential. Effective communication between linked devices may be ensured if these techniques are widely used. However, its incorrect use might cause network congestion and safety issues. Before jumping to what is Multicast communication, let’s first look at communication and it various types. In computer networks, “casting” refers to the process of sending information from one or more clients to one or more recipients across a shared communication medium called a network. Computer networks use three distinct forms of casting: If you send the traffic from one source to one destination, it is unicast traffic. Whereas if we are sending from one source to all, it is considered as broadcast. And about multicast, we all know that it’s used to send data from one source to a group of receivers. Almost all of the data exchanged in an IP network is of the directed unicast type. By definition, only the two hosts involved in the initial request may interact with one another through the path set up by the unicast. Watch this video to know more about Types of Communication – Due to the high cost of transmitting a single audio or video stream to a single user, unicasting such streams to a wide audience is impractical. Therefore, this is an ideal scenario for multicast communication since it allows sharing of a single stream to multiple hosts. Now that we have good idea of communication, its time to move to Multicast Communication. The term “multicast” refers to a method of sending a single message to a large group of people and a tool to make the most of available network bandwidth while conserving system resources. Also, we can say that Multicast communication is a type of technique that transfers packets from one source to many receivers simultaneously. We also use many applications in our daily life, like Audio/Video Conferencing, Online Gaming, IPTV, etc. The best part is that all these applications work on multicast communication. Multicasting is regarded as a special kind of broadcasting. Similar to broadcasting in operation, multicasting sends information to selected or targeted network participants. This task can be completed by sending separate copies to each user or network node, but doing so is wasteful and could result in an increase in network latency. Multicasting, which allows a single transmission to be split up among numerous users to address these drawbacks, therefore limits the signal’s capacity. Ethernet multicast signifies the process of multicasting at the data link layer in Ethernet networks. Ethernet Frames are sent to a group of destination devices that shares a common multicast address. By setting the least significant bit of the first byte of the destination address to 1 these frames are identified, differentiating them from unicast and broadcast frames. IP multicast is a communication method that allows one-to-many communication over an IP network. The sender sends a single packet that is replicated by routers in the network to reach multiple receivers, instead of sending multiple individual unicast packets to each recipient. It helps in reducing Network traffic and conserves bandwidth. Again, by sending join and leave messages to the network routers the destination nodes indicate their interest in receiving multicast messages. This way, the sender only needs to transmit the data packet once, and the routers take care of replicating and delivering it to the intended recipients. Any host within a small home or office network has the ability to send and receive multicast datagrams. A multicast datagram can be received by any host on the network that has been set up to receive messages on the corresponding multicast address. Also, a host has the capability to send and receive on multiple multicast addresses. Note: UDP is used by multicast and are sent through switches and hubs. The host must be configured to receive on that multicast address to receive a multicast message. A multicast group consists of all hosts that have been configured to receive packets on a specific address. When a host is configured to receive datagrams sent to a multicast, it is added to the multicast group for that address. One to an unlimited number of hosts comes under a group. The list of individual group members is neither maintained by the host nor by routers. A host can belong to several multicast groups and send multicast messages to various multicast addresses. A host can send datagrams to a multicast group address even though there are no members present in that group, and a host doesn’t need to be a member of a group to send multicast datagrams to that group. Note: Multicast packets are routed through switches. A router will check to see if any hosts on a locally connected network are set up to accept multicast datagrams by using IGMP (Internet Group Management Protocol). On the local subnet on a regular basis router will listen to IGMP messages and send queries. By using the multicast group address 224.0.0.1 (reserved for all hosts). Multicast routers do not keep a record of which hosts are members of a group but only need to know if any hosts on that subnet are part of a group. If a router gets a multicast datagram from another network and does not have any members for that group address on any of its subnets, the packet is dropped. There are a few important terms in Multicast communication and these are very basic terminologies that are known by different names in normal. Let’s move on and understand the advantages of Multicast now. The success of certain cutting-edge applications is greatly aided by the benefits offered by multicast technology. Several of these advantages of Multicast are discussed below. These are the most common advantages of Multicast. NOTE: Another way of providing one-to-many packet delivery is Replicated Unicast. Let’s see a quick comparison between the two. In this section, we will discuss various multicasting technologies. Each of the following multicasting technologies has its place in certain contexts and with certain applications. Still, Multicast communication relies on the following: Network multicasting is managed and controlled by the Internet group management protocol (IGMP). It’s not limited to only LANs but also WANs. IGMP for its operation in L2 networks. IGMP Versions There are 3 versions available – a. IGMP v1 – old version not used today. b. IGMP v2 – common in most multicast networks. c. IGMP v3 – used by source-specific multicast IGMP v1 & v2 Messages PIM is a mechanism for sending multicast data packets across a network. A variety of unicast routing protocols may be used by PIM to determine the best route between sender and recipient. PIM’s main benefit over IGMP is that it reduces end-to-end latency in a multicast session by eliminating the need to monitor the receiver status. PIM allows it to function on Layer 3 networks. PIM Operating Modes – a. PIM Dense Mode (PIM-DM) b. PIM Sparse Mode (PIM-SM) c. PIM Sparse Dense Mode d. PIM Source-Specific Multicast (PIM-SSM) e. PIM Bidirectional Mode (Bidir-PIM) In L-3 Multicast – IP Addressing, Source IPs in multicast packets always remain in the form of unicast, whereas the destination IPs represent the multicast group. And these destination Multicast IPs belong to the D-Class of IPv4 address. The first four bits of this whole range start with 1110. And this is the entire range for Multicast Address – 224.0.0.0 – 239.255.255.255, and every single IP simply represents a multicast group. Source IPs in multicast packets always remain in the form of unicast as we know that there is a one-to-one correlation between IP and MAC at a data-link layer where we have two sub-layers of Data-Link, which are MAC & LLC. But when it comes to destination IP, a specific MAC is reserved for multicast destination IP. The motive is to have the sender and receiver agree on a single, suitable destination MAC. So, a new special reserved MAC is created to send multicast packets in the IP networks so that multicast traffic replication doesn’t have packet manipulation and the burden on routing resources could be avoided. The IP address of a multicast group is translated to a unique MAC address, which is used by interfaces to determine which multicast packets belong to which reserved groups. Depending on the MAC address associated with the multicast traffic, a LAN segment can support multiple streams, and the receiver can choose which stream to forward to the CPU for processing. So, that’s how the mapping is done here with the help of this reserved MAC add which is attached to multicast IPs. NOTE: Multicast Reserve MAC Address always starts with 01:00:5E Reserved Multicast Addresses To provide this, a simple mapping procedure is used to generate a well-known multicast MAC address which is the special MAC Address (01:00:5E) To illustrate this point, let’s presume that we have the multicast address 224.0.0.5. After Mapping, the first 24-bit standard part will be – 01:00:5E (Reserve MAC). Also, the 25th Bit is always set to – 0. 01:00:5E – 0000|0001: 0000|0000: 0101|1110 (This is the conversion of special MAC) Now we have this multicast address – 224.0.0.5 so, we’ll convert the remaining 24 bits of this IP. 224.0.0.5 – 11100000.00000000.00000000.00000101 (This is the conversion Multicast IP) so, now we’ll use the remaining 24 bits 224.0.0.5 – 11100000.00000000.00000000.00000101 So, the last 24 bits will be – 00000000.00000000.00000101 The bold and italic mark is the special 25th bit which is always 0 Now, the resulting destination MAC will be – 01:00:5E:00:00:05 Let’s move on and understand Multicast forwarding. A collection of hosts is often clustered under a multicast IP address in multicast forwarding. Data may then be sent from the source to the IP address, which subsequently sends data to the many hosts allocated to the multicast IP. This is a data transfer from one location to multiple locations. There are two major interface types per multicast source – So, we call this entire concept reverse path forwarding (RPF). If you want more insights about Multicast Communication, you can also check out this video – Multicast communication is a network communication method where a single sender can transmit data to multiple recipients simultaneously. Unlike unicast (one-to-one) communication, multicast enables one-to-many communication. For example, in video conferencing, a sender can multicast video and audio streams to multiple participants, allowing real-time communication and collaboration. The purpose of multicast is to enable efficient and scalable one-to-many or many-to-many communication over a network. It allows a sender to send a single copy of data packets to a group of recipients who have expressed interest in receiving the data. This eliminates the need for the sender to transmit separate copies of the data to each recipient, reducing network traffic and conserving bandwidth. Multicast is commonly used for applications such as multimedia streaming, software distribution, real-time collaboration, and content delivery networks. Multicast can be used with both TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). However, UDP is more commonly used for multicast due to its connectionless nature and lower overhead. UDP multicast offers a more efficient and scalable approach for delivering data to multiple recipients simultaneously, making it suitable for real-time multimedia streaming, online gaming, and other applications where speed and efficiency are crucial. TCP, on the other hand, is a connection-oriented protocol and is not typically used for multicast. Two applications of multicasting include video streaming and software updates. Multicasting enables efficient delivery of live video streams to multiple viewers simultaneously, reducing network bandwidth usage. Similarly, for software updates, multicasting allows for simultaneous distribution to numerous devices, reducing network congestion and ensuring timely updates for all recipients. These applications leverage the benefits of multicasting in optimizing data delivery to multiple recipients on a network. We have now taken a closer look at everything related to Multicast Communication and Multicasting. If you are still with us, it would be great if you share your honest feedback about this article. If you like this article, subscribe to our free newsletter. You may also like – You should check out our training by clicking this link – PyNet Labs Courses To conclude this article, we can say that communication methods represent vast opportunities for developing networked systems. With the proper software engineering and correct practical use of addressing methods, systems can communicate in the network with improved efficiency, reliability, and security.Introduction
Communication and Its Types
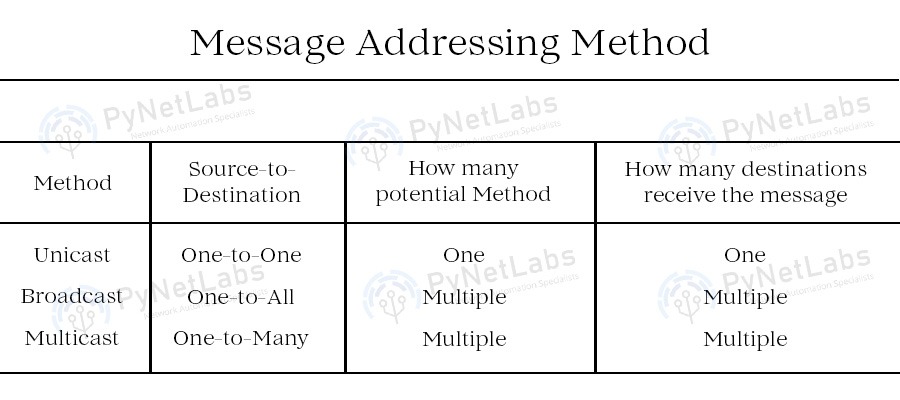
What is Multicast Communication?
Ethernet Multicast
IP Multicast
How Multicasting Works
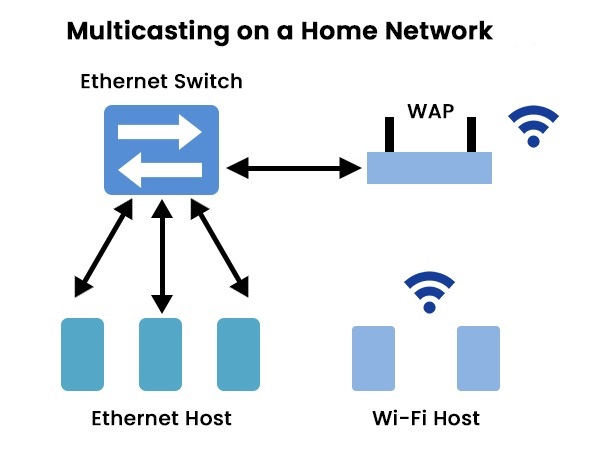
Multicast Groups:
Multicasting on Internet
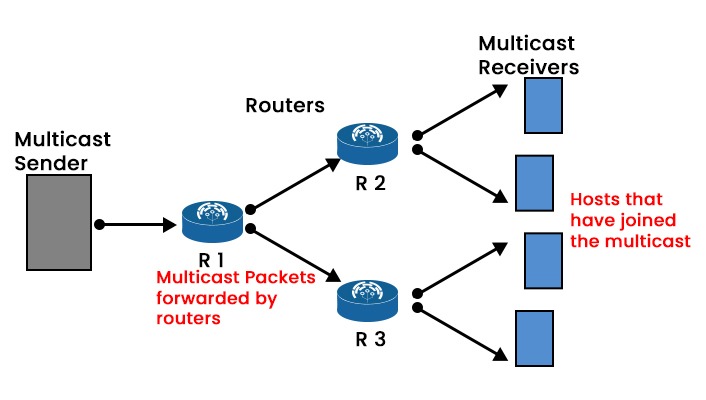
Multicast Communication basic terminologies
Advantages of Multicast
Multicast Vs. Replicated Unicast
Multicast Replicated Unicast In multicast source sends only a single copy of any packet. In replicated unicast, the source would have to send as many copies as the number of known receivers. Multicasting Technology
1. IGMP
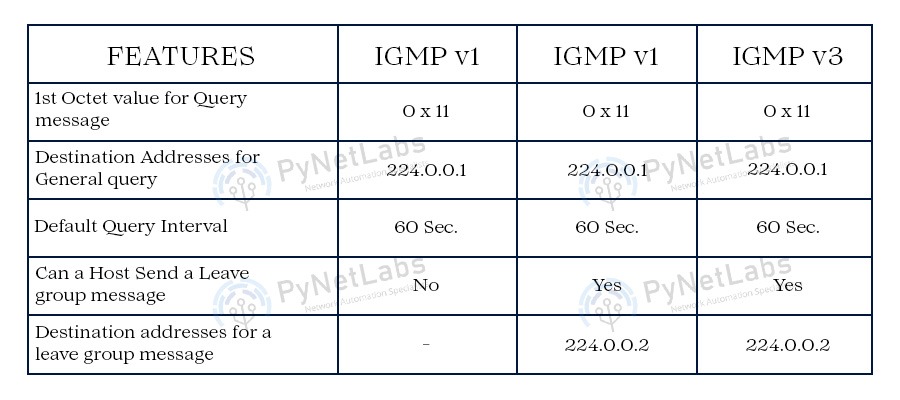
2. PIM
3. Layer-3 Multicast – IP Addressing
Layer 3 Multicast MAC
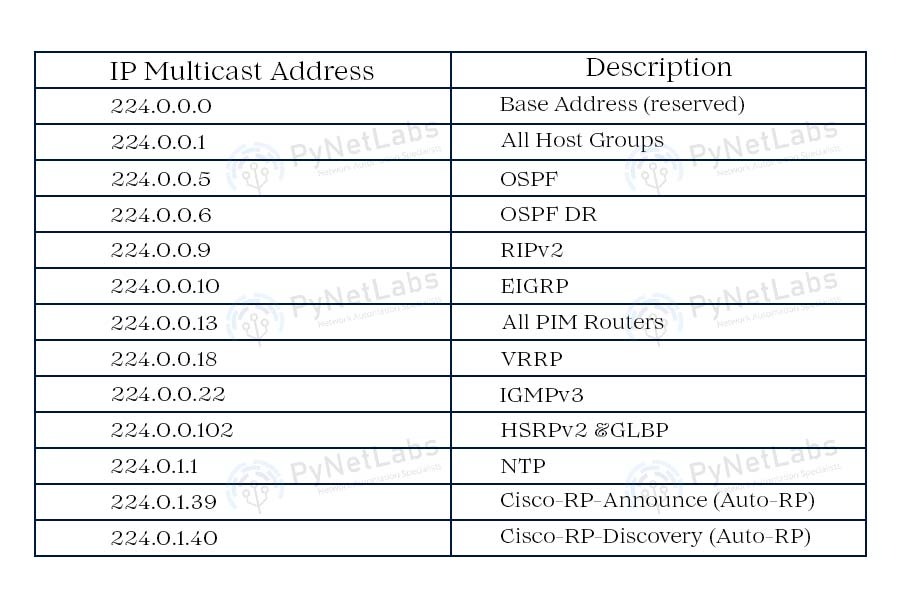
Mapping L3 TO L2
Multicast Forwarding
Frequently Asked Questions
Q1 – What is multicast communication with an example?
Q2 – What is the purpose of multicast?
Q3- Is multicast TCP or UDP?
Q4 – What are two applications of multicasting?
Conclusion







