Cisco ASA Firewall Interview Questions and Answers

If you are preparing for a Cisco ASA firewall admin job, then we have got your back with these Cisco ASA firewall interview questions and answers. ASA stands for Adaptive Security Appliances, a security device used for proactive threat defence. It combines VPN capabilities, antivirus, firewalls, and intrusion prevention to stop attacks before they spread to the whole network. These Cisco ASA Firewall interview questions and answers are curated by our top trainers, who are also industry leaders in this technology. Cisco ASA (Adaptive Security Appliance) is a widely used firewall solution developed by Cisco Systems. It serves as a critical component of network security, providing robust protection for organizations of all sizes. The Cisco ASA firewall is designed to defend against various cyber threats, such as unauthorized access, data breaches, malware, and other malicious activities. Without any further a due, let’s start with ASA interview questions and answers. Here are the most asked Cisco ASA Firewall interview questions and answers that are favourites to most interviewers. Understanding these questions will give you a better chance of clearing any job interview. Firewall is a device that is placed between a trusted (Higher security Zone / Inside Network) and an untrusted network (Low-security Zone / Outside Network) to provide security to users, servers, and internal network. It allows or denies traffic that is allowed to enter or leave the network according to pre-configured rules. Network firewalls guard an internal LAN network from malicious access from the outside/unsecured zone, such as malware-infested websites or vulnerable ports. A Firewall also regulates inbound and outbound communications between devices. It works at the Network (Layer 3), Transport (Layer 4), and Application layers (Layer 7) of the OSI Model. A Gateway is used for making your network/segment/VLAN communicate with the outside network because Layer 3 devices (Routers) do not accept Broadcast. Therefore, we must have a default gateway for unicast communication with the router. A firewall on a network secures networks from unauthorized access, either outgoing or incoming. Network firewalls could comprise hardware components or virtual machines, e.g., Cisco ASA, Checkpoint. Stateful Firewall – Stateful Firewalls are equipped to monitor and detect the state of all traffic that is on the network. They can track and defend based on traffic flow patterns, and a Stateful firewall is aware of connections that go by it. It adds and keeps details about the connections of users in a state table, also called the connection table. It then utilizes this connection table to establish security policies that apply to the connections of users. Examples of stateful firewalls are: Juniper, ASA, and Checkpoint. Stateless Firewalls – Stateless firewalls concentrate on specific packets and use preset rules to filter traffic. Stateless firewalls, however, do not examine the status of connections; instead, only at the packets. An excellent example of a filtering firewall is the Extended Access Control lists available on Cisco’s IOS Router. ASA utilizes the same security level for every interface. Every logical ASA interface should have an IP address, security level, and a nameif configured to function. ASA uses security levels to assess the trustworthiness of the network connected to the interface. The security level limit is between 0 and 100, where Level 100 is the highest secure, while 0 is the most distrusted. By default, the ASA only permits traffic from a secure upper level down to the lower level. Transparent mode firewall is one of the two modes ASA Firewall; while the other is Layer3 (Routed mode). In transparent mode, the Firewall works on layer two-mode and does not function in Layer 3 or routed mode. This permits it to be integrated into the network segment with little disturbance since no IP address changes are needed to the network. Mac forwarding and lookup are accomplished through the destinations’ mac addresses. The transparent firewall mode is supported by just two interfaces (inside and out). Packets are redirected between one interface on the ASA to the other based on their MAC addresses. It is a requirement for the ASA to keep the MAC address table so that it knows what hosts are available on its various interfaces. ASA doesn’t support HTTPS filtering. ASA cannot perform deep packet inspection or inspection using regular expressions for HTTPS traffic because all content in HTTPS is protected (SSL). When primary firewall is issued the command “no failover active”, it will make the secondary Firewall active. “Failover active” command will trigger fail back to the original active firewall. DMZ Zone is considered with reference to Perimeter Firewall. DMZ Zone has security level 50 on ASA Firewall and is what sits between an organization’s internal network and an external network. A DMZ network permits Internet users to connect to the public servers of a business. A DMZ network is responsible for ensuring the security of a private network. A DMZ is an open subnetwork to the public but is behind a firewall. A DMZ lets you redirect traffic from your WAN port to an address on your specific IP. You can set security rules for firewalls to permit access to specific ports and services within the DMZ from both the LAN as well as the WAN. A Denial-of-Service attack (DoS attack) is an attack that attempts to disable a computer or network, so it is not accessible to its intended users. DoS attacks do this by sending traffic to the target or information that causes a crash. Both DoS attacks deprive legitimate users (i.e., employees, members, or account holders) of the service or resource they expect. A Denial of Service (DoS) attack is made from a single machine where the attack may be directed to a specific Server, a specific port, or a service on a target. It may also be to the network or any of its components, a firewall or to any other system. DoS attacks often target high-profile websites such as media, commerce, government, and trade organizations. While DoS attacks are not usually associated with the theft or loss of significant information or other assets, they can be costly to the victim both, money and time-wise. A distributed denial of service (DDoS) is an attack that attempts to interrupt the regular traffic of a target server, service, or network. It overwhelms the target’s infrastructure or causes a flood of Internet traffic. This kind of attack happens from more than one source or location. Even the DDoS attackers are mostly unaware of their participation in the DoS attack. Infact, they are tricked by a third party into joining the attack. The attack generation in this type of attack is distributed among multiple computers. These are the top most asked Basic Cisco ASA Firewall Interview Questions and Answers. In an Active/Active failover configuration, both ASAs pass the network traffic by splitting traffic into groups. In the multiple context mode, Active/Active failover is only available to ASAs. In Active/Active failover, you divide the security contexts on the ASA into failover groups where the 1st unit is Active for one Failover Group. In contrast, the 2nd unit performs an Active role for the second Failover Group. The other unit takes over during the event of the Active unit going down. Active-Active setups are generally done to allow more traffic to pass through the firewalls than a single unit can handle. A failover group is a logical group consisting of security contexts, and it is possible to create up to two groups for failover. Administrator contexts are always part of the failover group 1. Any security contexts that are not assigned are also part of failover group 1 by default. Transparent mode to routed mode can be done using the below command – ciscoasa(config)# no firewall transparent From Routed mode to transparent mode, use this command – ciscoasa(config)# firewall transparent Only one unit can pass traffic with Active/Standby failover while the other unit is in standby mode. The units that run in either single or multiple context mode have Active/Standby failover availability. The Standby unit monitors the Active unit, and both share the state information. If the Active unit goes down, the standby unit takes over the role of the Active unit and starts forwarding traffic. Before passing traffic, the unit that becomes active assumes IP addresses and MAC addresses from the failed unit. An EtherType ACL consists of one or more Access Control Entries (ACEs) specifying an EtherType. The EtherType rule controls the EtherType that can be identified by a 16-bit hexadecimal number and other traffic types. Only non-IP layer-2 traffic is subject to the EtherType ACL, and this applies only to bridge group member interfaces. These rules can be used for traffic control (permit/drop) based on the EtherType value contained in the layer-2 packet. Webtype ACLs can be used to filter clientless SSL VPN traffic. These ACLs can deny access based upon URLs and destination addresses, and URL-based ACLs or TCP-based ACLs are the two types of web-type ACLs. These are the most asked Cisco ASA Firewall Interview Questions in any Cisco ASA interview. We understand that every interviewer is different and has different questions, but we are sure you will undoubtedly encounter at least 5/6 questions in any ASA interview. You can download the PDF containing more questions if you are looking for more Cisco ASA Firewall interview questions. You can submit your Email below; we will send you a complete list of top Cisco ASA interview questions. In this blog, we have covered the most important Cisco ASA Firewall Interview Questions and Answers both for freshers as well as Experienced candidates. We hope you find these question answer useful and able to succeed in your Interview. If you are looking for any CCNA/CCNP ENCOR training, you can check out our various training from the “All Courses” section in the menu. We are the top CCNA training institute in India as well as the USA.Introduction
About Cisco ASA Firewall
Cisco ASA Firewall Interview Questions and Answers for Freshers
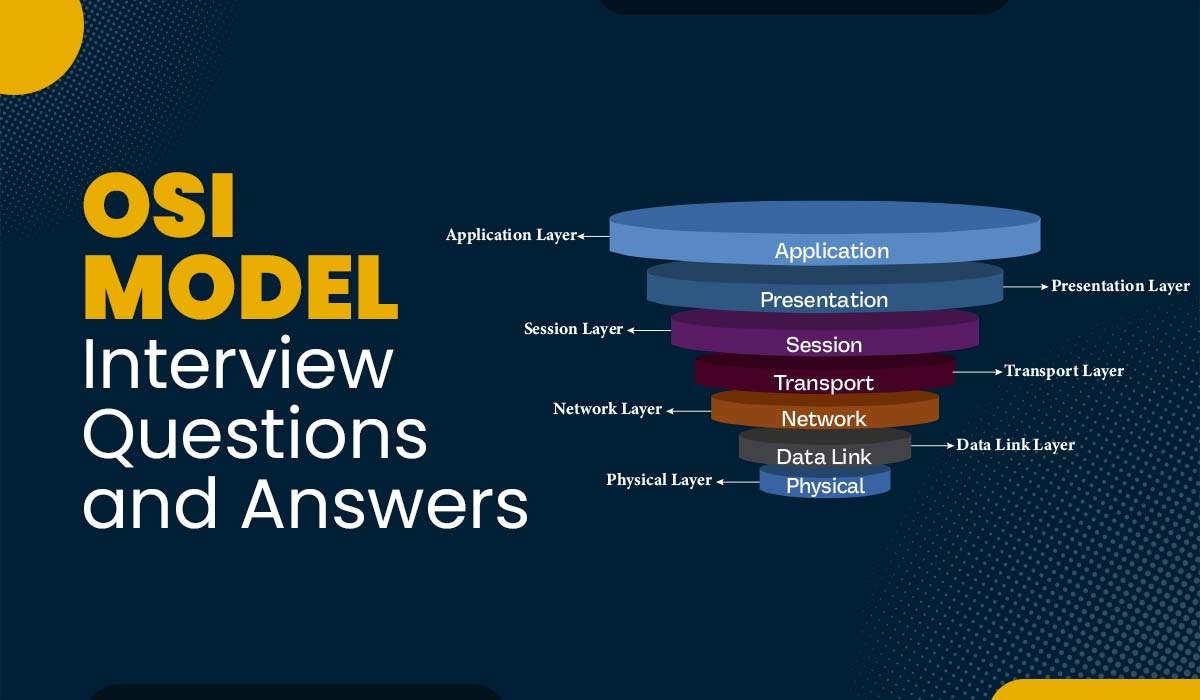
Q1 – What is a Firewall, and at which layer of the OSI model does it works?
Q2 – What is the difference between Gateway and Firewall?
Q3 – What is the difference between a Stateful & Stateless Firewall?
Q4 – What are the security levels in Cisco ASA?
Q5 – What is Transparent Firewall?
Q6 – Is it possible to block HTTPS Traffic on Firewall?
Q7 – What is the command to forcefully activate a secondary firewall to become an active firewall?
Q8 – What is DMZ Zone, and explain its purpose and usage?
Q9 – What is a denial-of-service attack (DoS)?
Q10 – What is a Distributed Denial of Service (DDoS) attack?
Cisco ASA Firewall Interview Questions and Answers for Experienced
Q11 – What is Active-Active Failover?
Q12 – Which commands are used to convert Transparent mode to Routed mode and vice versa?
Q13 – What is Active/Standby failover?
Q14 – What is EtherType ACL in Cisco ASA Firewall?
Q15 – What is Webtype ACL in Cisco ASA?
Cisco ASA Firewall Interview Questions and Answers PDF:
Conclusion