
Get equipped with these 15 most asked EIGRP interview questions and answers to perform better in your upcoming interview. These questions are curated by our experts, some of the most talented minds in the networking field.
Read More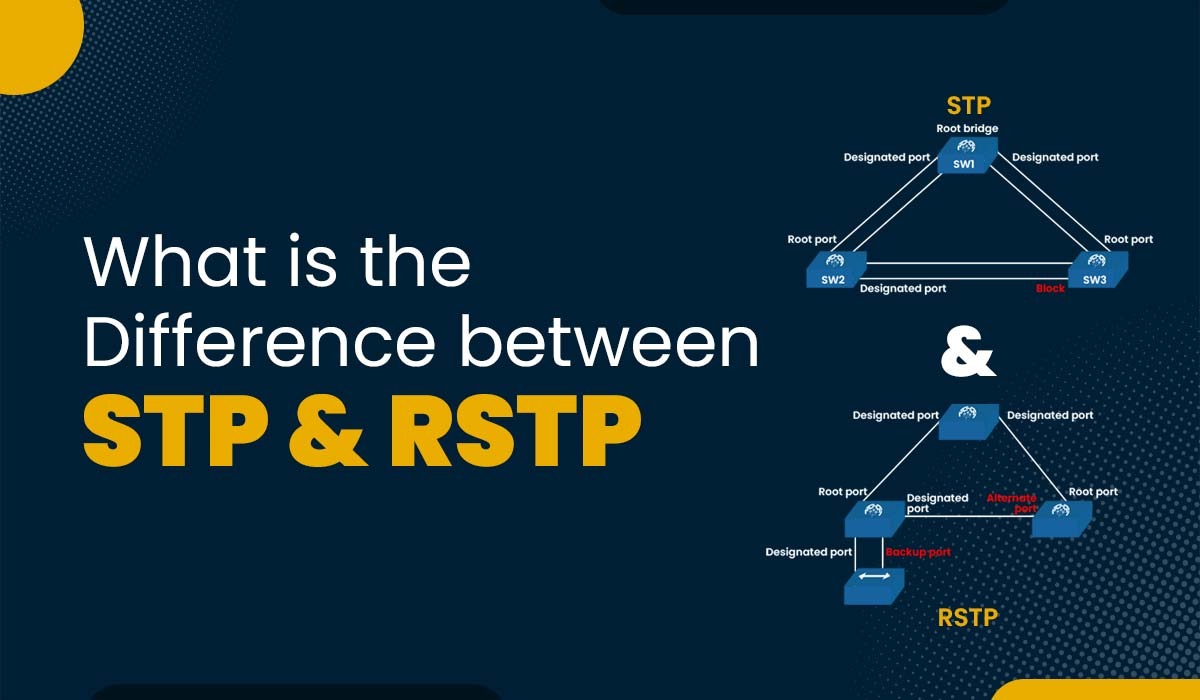
Introduction In a computer network, having multiple paths to reach a destination can be beneficial for redundancy and load balancing. However, it can also cause problems such as network loops, broadcast storms, and inconsistent routing. To avoid these issues, network devices need to agree on a single active path for each destination and block the […]
Read More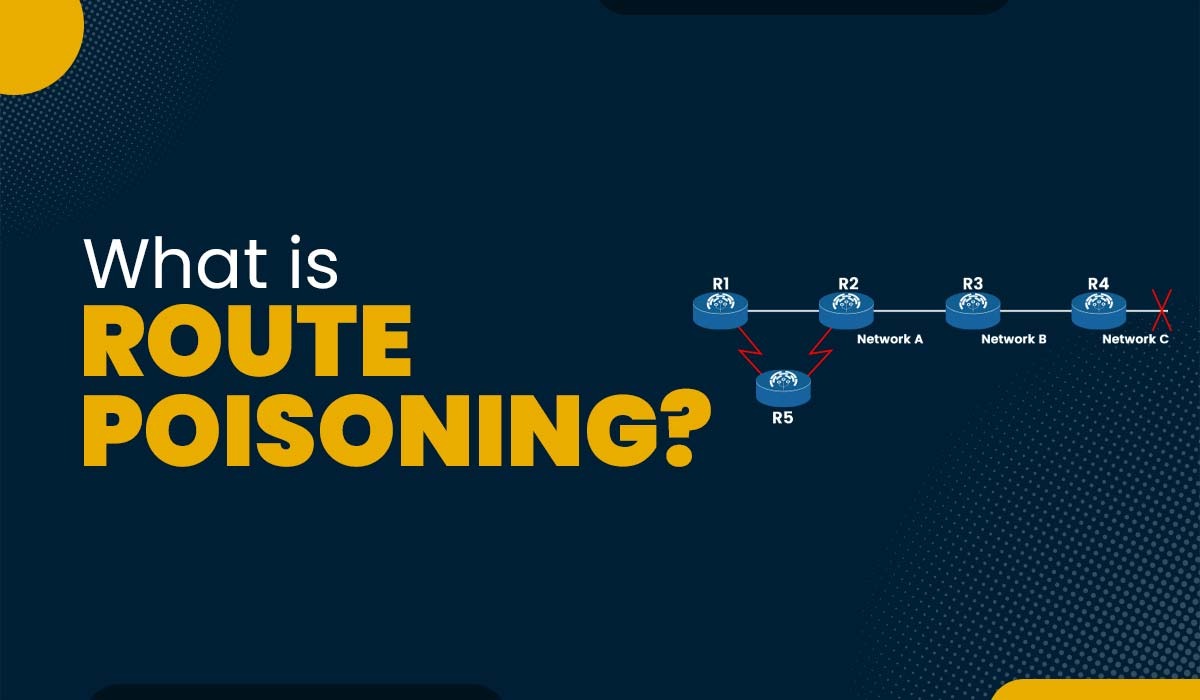
Introduction Finding the optimum route for data packets to transmit inside a network from a source to a destination is known as the routing process. The rules and algorithms known as routing protocols are what routers use to communicate with one another and exchange routing data. However, routing protocols can run into issues like routing […]
Read More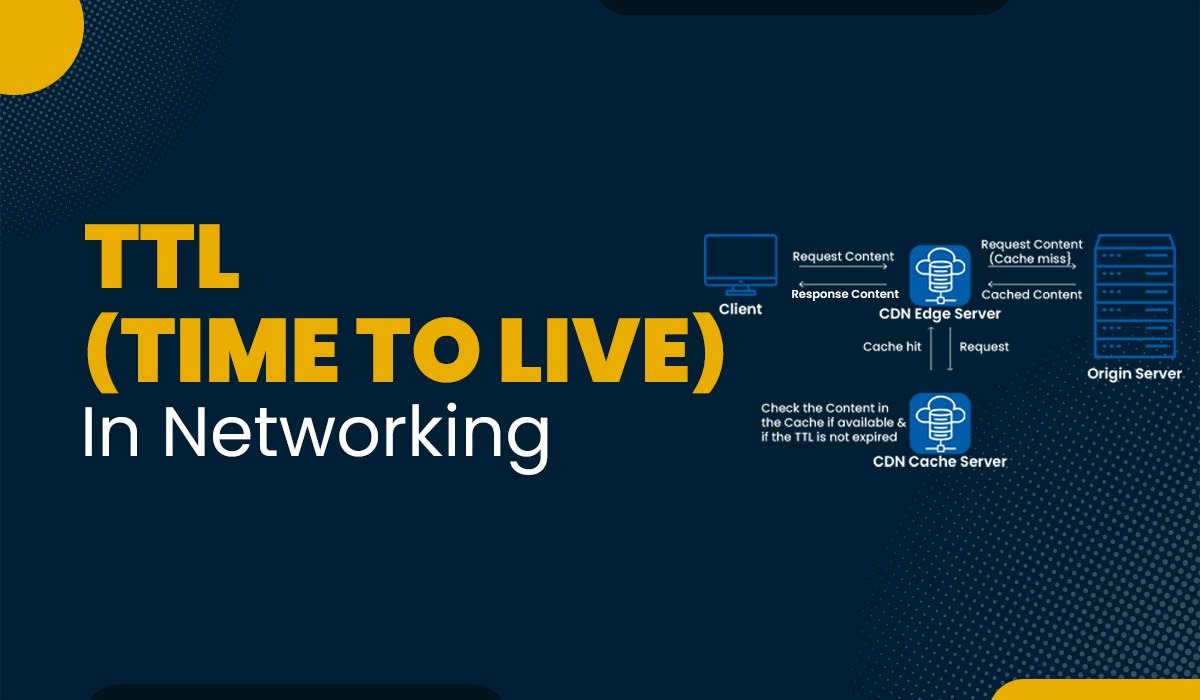
Introduction When users visit a website, everyone wants them to receive the most up-to-date information. However, they also need their site to load quickly. Otherwise, they risk a bounce, where the user gives up and leaves their site quickly. Fortunately, they can find a balance by adjusting their website’s Time to Live (TTL). But what […]
Read More
Introduction Scammers and other cyber criminals are getting more active in today’s society, harming millions of consumers. It is essential to encrypt everything to stop these people from stealing priceless data. Fortunately, three alternative encryption techniques may be used: symmetric encryption, asymmetric encryption, and hash functions (Keyless). In this blog, we will be mainly focusing […]
Read More
Introduction A thorough understanding of network structure and devices is essential for network engineers and administrators. The devices that are part of a network as well as the interfaces, protocols, and settings each one uses, must all be understood. This data may help with troubleshooting, boost performance, and keep the network safe. But where may […]
Read More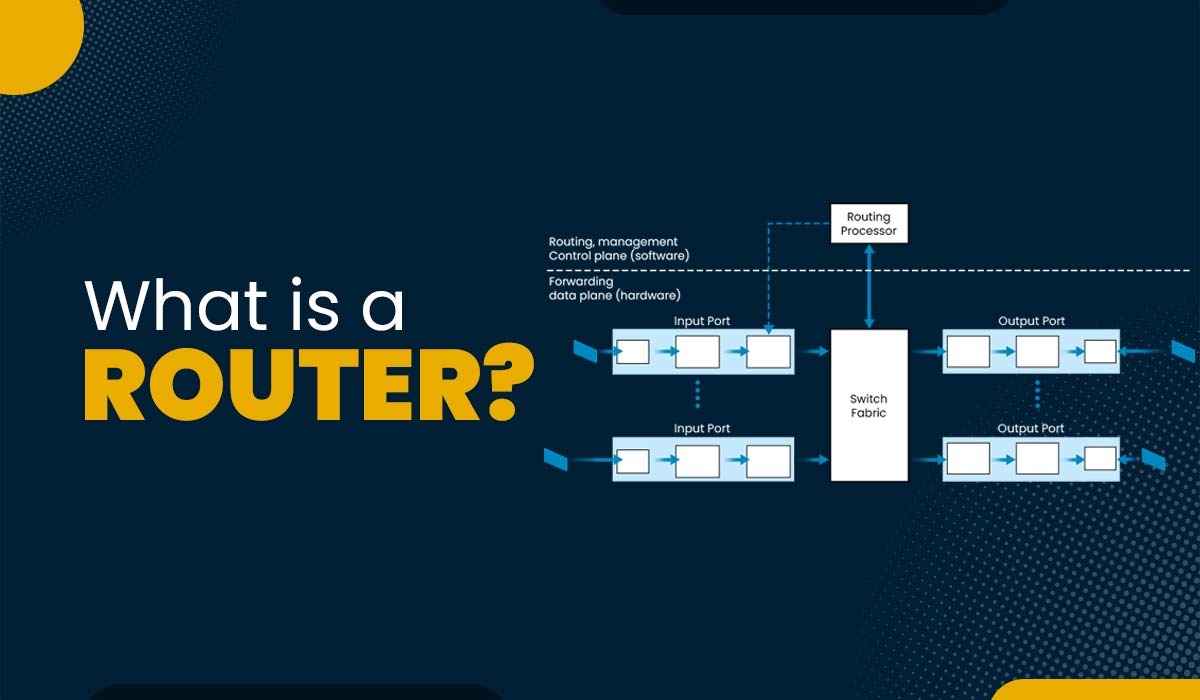
Introduction Data can be found anywhere nowadays. We use it for work, study, fun, and communication. But how is information delivered between devices? How can we guarantee the security and dependability of our data? Routers are the solution. A router in computer network is a component that connects various networks and routes data packets to […]
Read More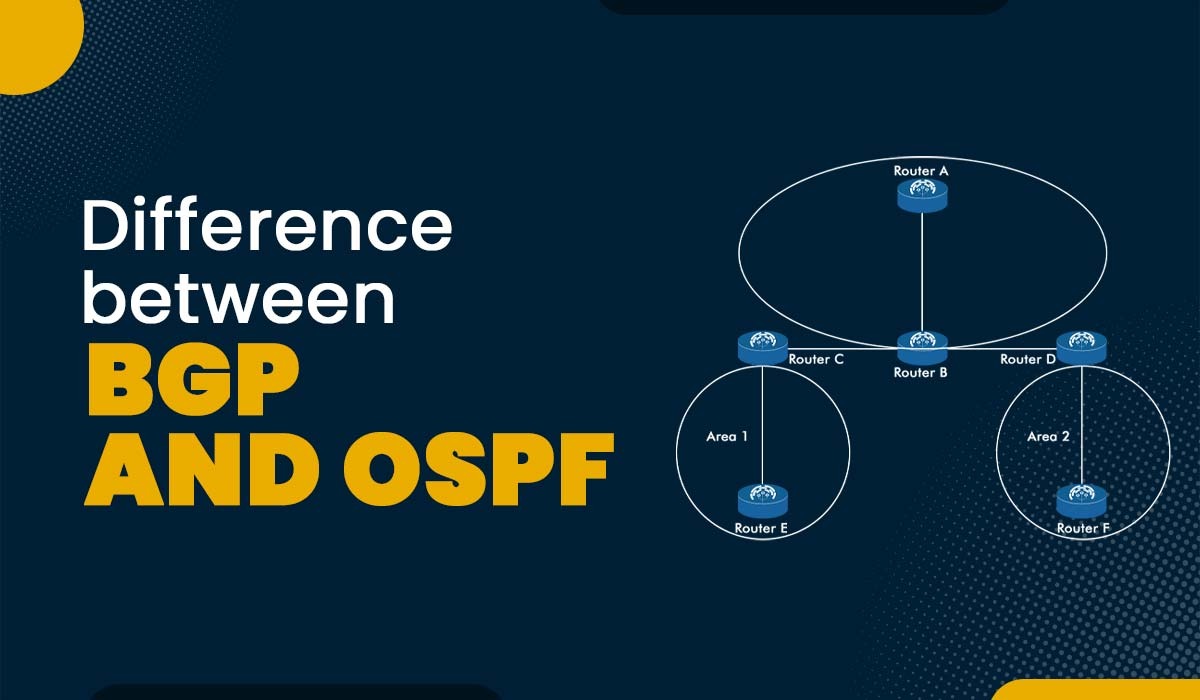
Introduction Using routing protocols, routers may automatically and dynamically exchange routing data. As each routing protocol has been developed to be ideally suited to a certain network implementation situation, there are several routing protocols to select from, each with its own advantages and disadvantages. Open Shortest Path First (OSPF) and Border Gateway Protocol (BGP) are […]
Read More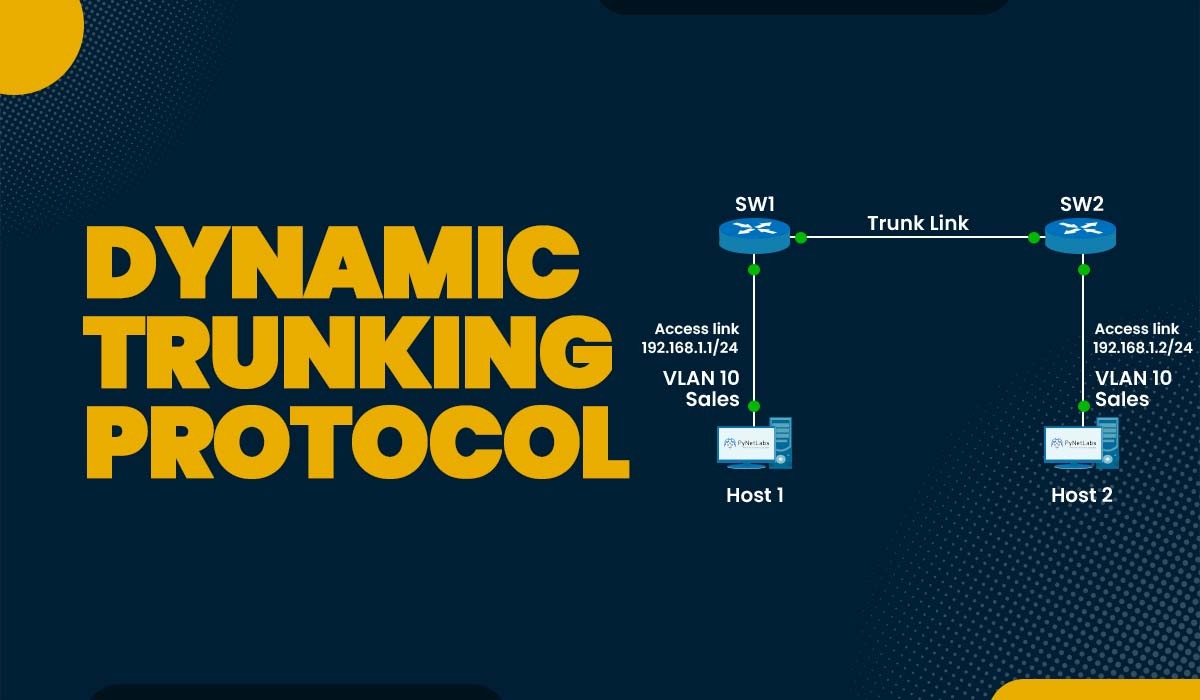
Introduction The word trunking may be familiar to network engineers or students studying networking. Multiple VLANs (virtual LANs) may share the same physical connection between switches using the practice known as trunking. With this method, you may separate various traffic types for security and performance reasons while conserving ports, cables, and bandwidth. But how do […]
Read More
Introduction Nowadays, everyone relies heavily on digital platforms, whether for business purposes or some important transactions. With the increase in digital presence, protecting personal data from hackers is crucial. VPN in cyber security is one approach to stop third parties from obtaining vital data for their benefit. In this blog, we will discuss what a […]
Read More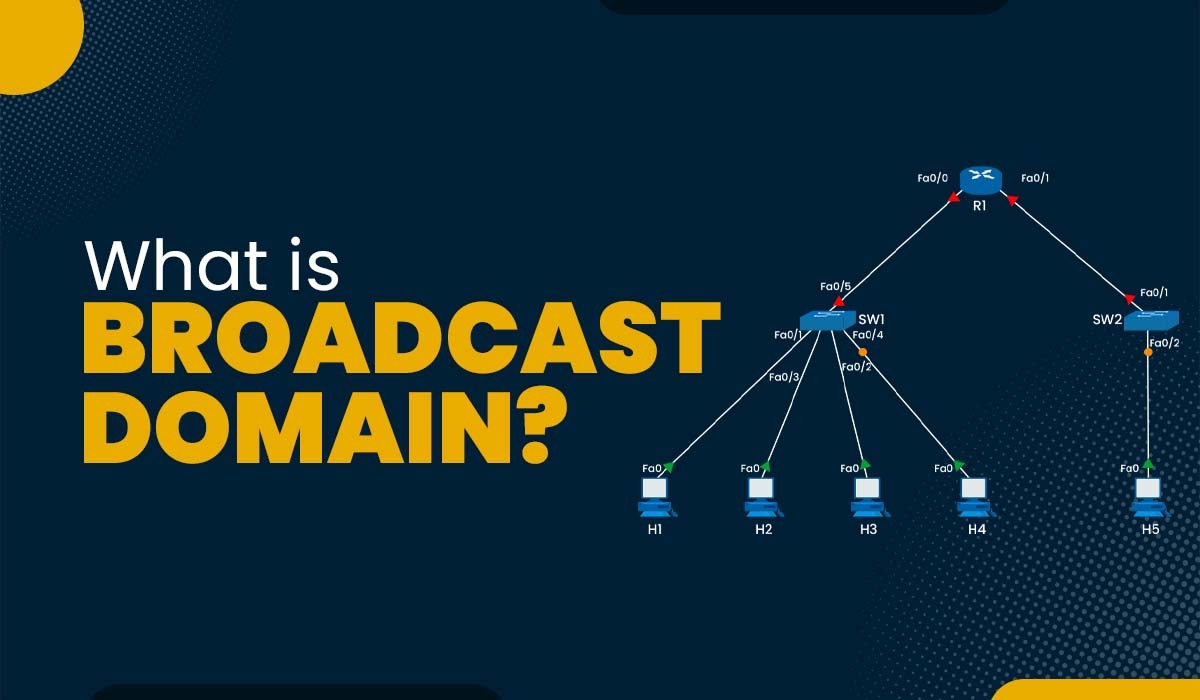
Introduction The study of networking covers a wide range of topics and technologies. A logical subdivision of a computer network where all nodes may interact with one another by sending and receiving broadcast messages is known as the broadcast domain. Regardless of their destination address, broadcast messages are unique data packet types distributed to all […]
Read More
Introduction Networking is now crucial to the success of almost every business in the modern digital environment. The importance of understanding how VLAN and Subnet function has grown as networks have expanded in both complexity and size. In this blog, we will explain the basic difference, i.e., VLAN vs Subnet, that will assist in understanding […]
Read More










