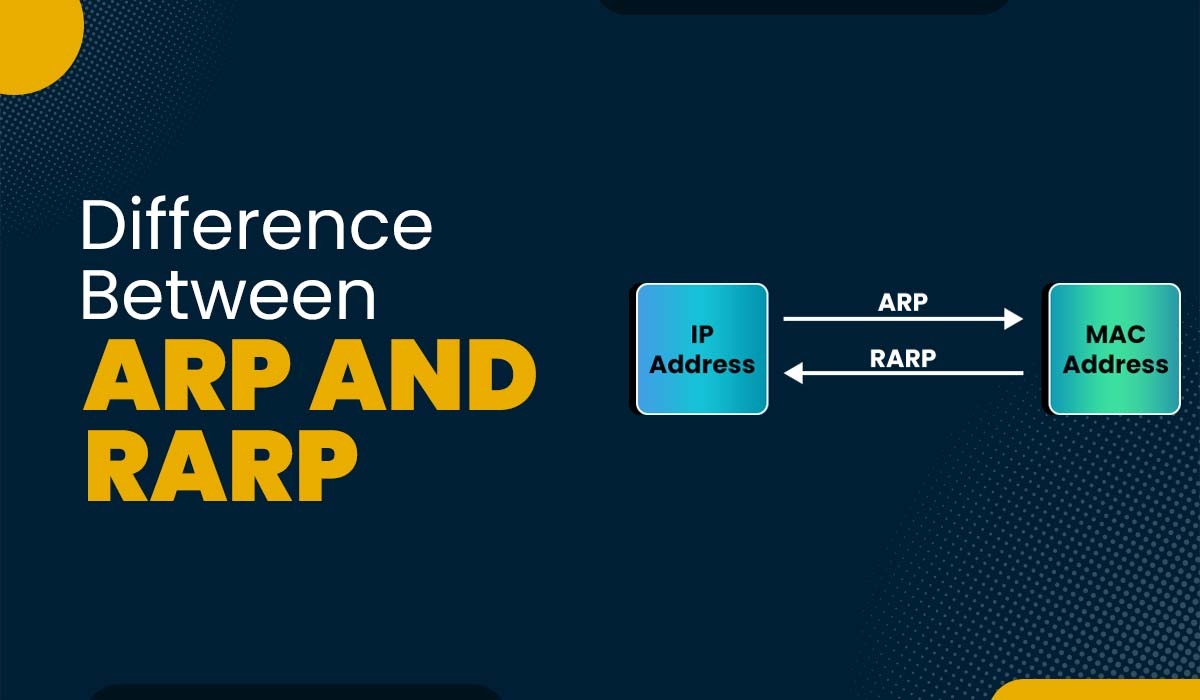
Introduction In computer networking, it is crucial to map a logical address (such as an IP address) to a physical address (such as a MAC address). The reason behind this is that network layers use different types of addresses to identify and communicate with different devices available within a network. But the question that comes […]
Read More
Introduction A computer network comprises a collection of interconnected devices. These devices, including computers, printers, and other data-transmitting tools, are linked through communication channels. Various types of network devices are utilized to establish, maintain, protect, and improve network connections. Network Devices carry out different functions at different layers of the OSI model and have different […]
Read More
Introduction Ethernet is a technology that enables devices to communicate over a wired network. It is widely utilized in area networks (LANs) where computers, printers, scanners, and various other devices are interconnected both with each other and with the internet. Ethernet is also employed in wide area networks (WANs) where multiple LANs are linked over […]
Read More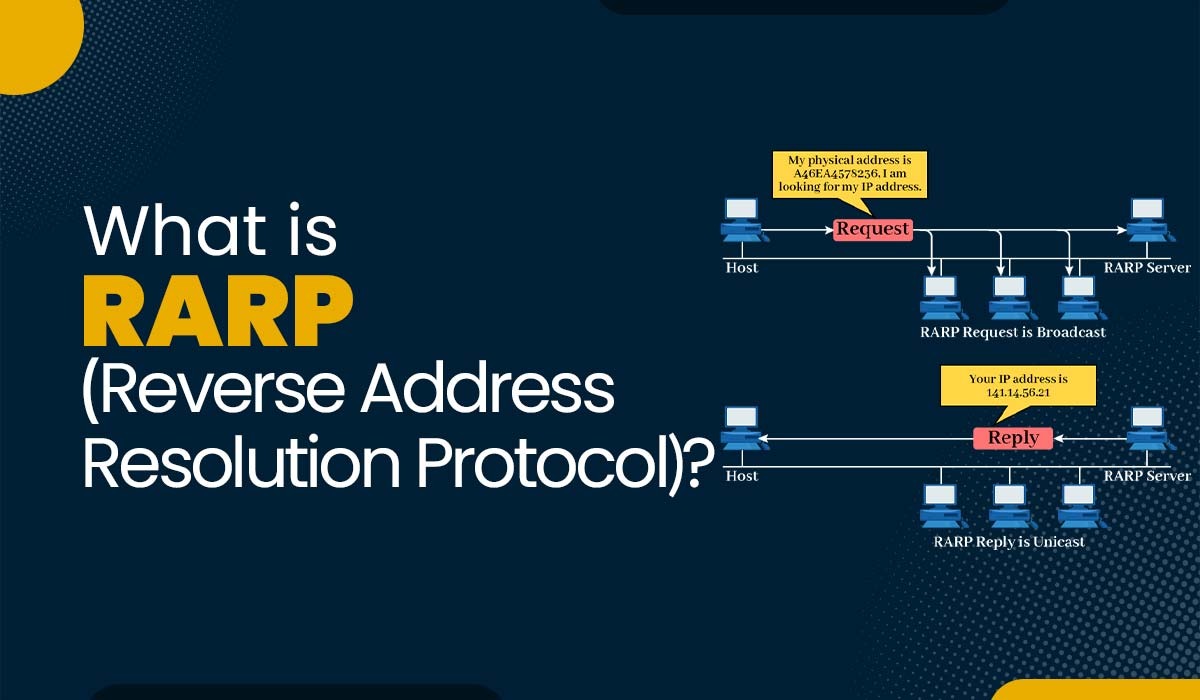
Introduction Reverse Address Resolution Protocol, also known as reverse ARP, is a networking protocol used to link a MAC address with an Internet Protocol (IP) address. It is the inverse of the Address Resolution Protocol (ARP), which links an IP address with a MAC address. RARP was originally developed in the stages of computer networking as […]
Read More
Introduction A cybersecurity career stands out as one of the best and is in demand worldwide. As our digital landscape grows increasingly, data, systems, and networks are needed to be protected from cyber threats. The realm of Cybersecurity can bring about changes in one’s life in many ways. It presents a challenging and captivating career […]
Read More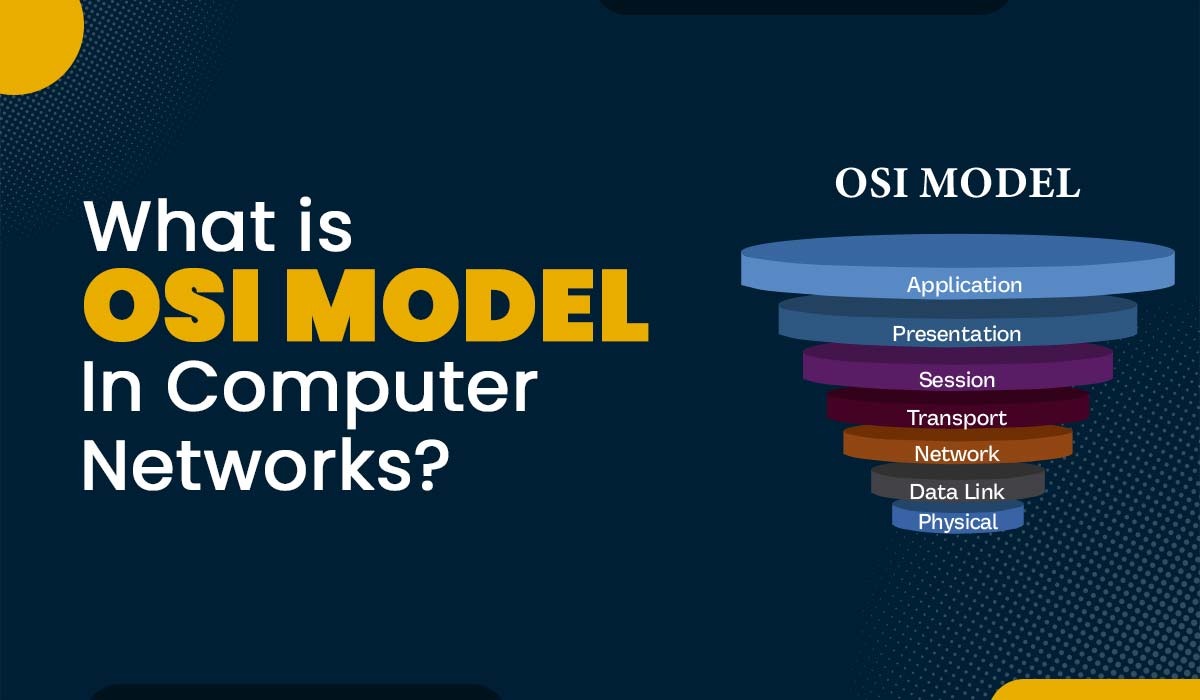
Introduction OSI model or Open Systems Interconnection model serves as a framework that explains the process of information transfer, i.e., from one computer’s software application to another computer through a medium. It was created by the International Organization for Standardization (ISO) in 1984. It is now widely acknowledged as an architecture model for inter-computer communication. […]
Read More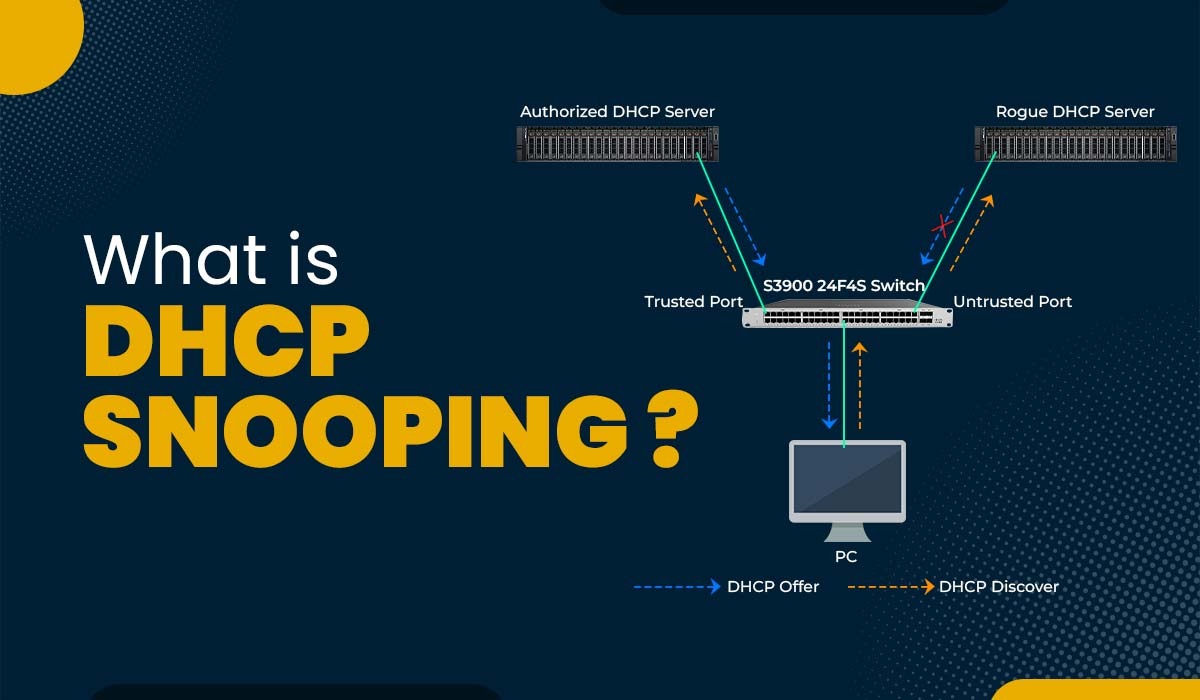
Introduction The Dynamic Host Configuration Protocol (DHCP) is a network protocol that enables devices to obtain IP addresses and other network configuration details from a server. DHCP simplifies IP addresses as well as reduces the need for configuration. However, it also introduces security risks, such as DHCP spoofing and DHCP starvation. To safeguard the network […]
Read More
Introduction A MAC address, also known as a Media Access Control address, is an identifier given to a network interface controller (NIC) in a device that communicates through a network. They have uses, including filtering, routing, security, and identifying devices. In this blog, we will explain the MAC address and its purpose. We will also […]
Read More
Introduction The Internet is a web of interconnected devices that communicate using protocols. One such protocol is the Internet Control Message Protocol (ICMP), which helps network devices diagnose communication issues. ICMP protocol plays a significant role in determining whether the data is reaching its intended destination on time or not. Typically, routers and other network […]
Read More
Introduction One of the most important concepts in routing is administrative distance (AD). AD is a metric that determines the reliability or trustworthiness of a routing source. With the help of AD value, routers can easily choose the best route among multiple routes to the same destination. In this blog, we will explain the concept […]
Read More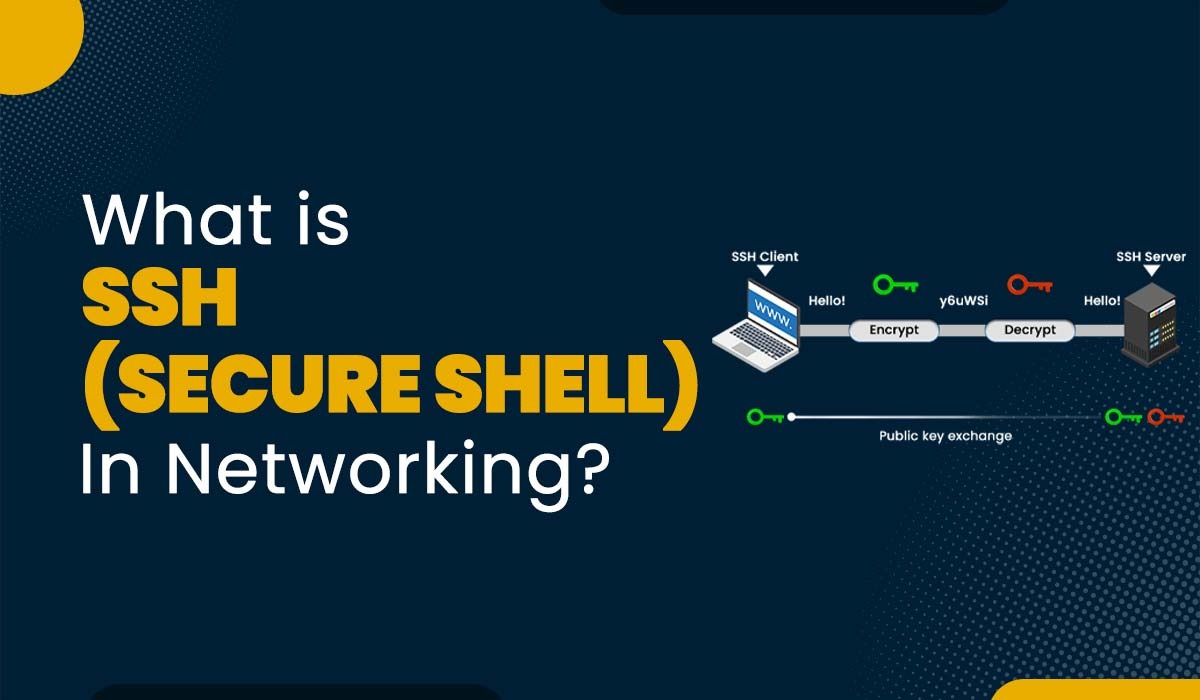
Introduction If you want to control a server or machine that is physically inaccessible, you need to communicate with it remotely. However, not all remote strategies are stable and secure. For example, older protocols like Telnet or rlogin ship your commands and passwords in simple text, which can effortlessly be intercepted by means of hackers […]
Read More
Introduction The Internet is a vast network where a number of devices are connected with the help of IP or Internet Protocol. IP addresses are numerical identifiers that are used to uniquely identify each device that is available inside the network. As we all have seen, the internet is growing exponentially day by day, resulting […]
Read More










